Latest News
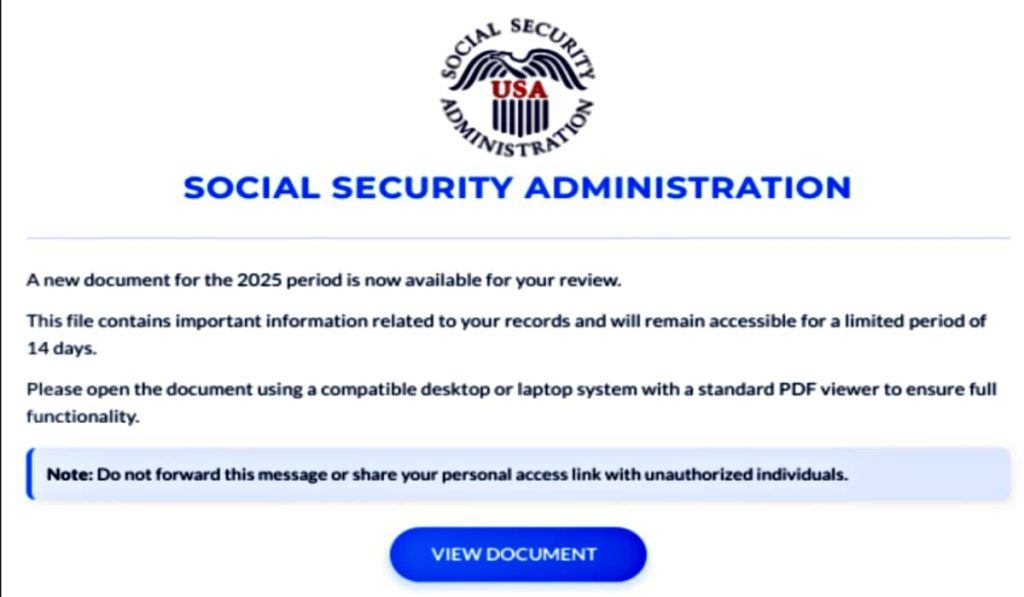
New Social Security Scam Emails Use Fake Tax Documents to Hijack PCs
A new phishing campaign is targeting thousands in the US by posing as the Social Security Administration. Learn how scammers use fake…
Hackers Spread Fake Red Alert Rocket Alert App to Spy on Israeli Users
Researchers at Acronis have discovered a malicious trojanized version of the Red Alert rocket warning app targeting Israeli Android users.…
900+ Certificates Used by Fortune 500, Governments Exposed by Key Leaks
A joint study by Google and GitGuardian reveals that over 2,600 valid TLS certificates, protecting Fortune 500 companies and government…
Cisco Patches 48 Firewall Vulnerabilities with Two CVSS 10 Flaws
Cisco patches 48 vulnerabilities in Secure Firewall products, including two critical CVSS 10 flaws that could allow authentication bypass and…
The Hidden Cyber Risks of Remote Work Infrastructure
Hidden cyber risks in remote work include insecure home Wi-Fi, phishing attacks, and data exposure, leaving businesses and employees…
Pakistan-Linked APT36 Floods Indian Govt Networks With AI-Made ‘Vibeware’
Bitdefender research reveals Pakistani group APT36 is using AI-generated vibeware and trusted cloud services like Google Sheets to target…
5 Best Next Gen Endpoint Protection Platforms in 2026
Discover the best next-gen endpoint protection platforms in 2026, built to detect modern threats, stop credential abuse, and secure enterprise…
PleaseFix Flaw Lets Hackers Access 1Password Vault via Comet AI Browser
Researchers at Zenity Labs uncover PleaseFix flaws in Perplexity’s Comet browser. See how zero-click calendar invites allow AI agents to steal…
Interview with Tom Howe of Hydrolix: AI Bots, the Friends, Foes, and Frenemies of Online Shopping
Hydrolix expert Tom Howe explains how AI bots impact ecommerce, how to spot good vs malicious bots, and why blocking them can hurt sales.
LeakBase Cybercrime and Hacker Forum Seized
Europol seizes LeakBase cybercrime and hacker forum used to trade stolen data, disrupting a global platform with over 140,000 members.
Authorities Shut Down Tycoon 2FA Phishing Platform Used to Bypass MFA
Europol and partners dismantle Tycoon 2FA phishing service used to bypass MFA, disrupting a global phishing-as-a-service operation targeting…
Institutional DeFi: Building Secure Bridges Between Decentralized Protocols and Corporate Treasury
Institutional DeFi helps corporations improve treasury liquidity, speed cross-border settlements, and manage capital using secure permissioned…