Latest News
Neptune RAT Variant Spreads via YouTube to Steal Windows Passwords
A new Neptune RAT variant is being shared via YouTube and Telegram, targeting Windows users to steal passwords and deliver additional malware…
Brothers Behind Rydox Dark Web Market Extradited to US
USA secures extradition of criminals from 9 countries, including two brothers behind Rydox, a dark web market for stolen data and hacking tools.
SpyCloud Research Shows that Endpoint Detection and Antivirus Solutions Miss Two-Thirds (66%) of Malware Infections
Austin, TX, USA, 7th April 2025, CyberNewsWire
Xanthorox AI Surfaces on Dark Web as Full Spectrum Hacking Assistant
New Xanthorox AI hacking platform spotted on dark web with modular tools, offline mode, and advanced voice, image, and code-based cyberattack…
Top Crypto Wallets of 2025: Balancing Security and Convenience
Crypto software wallets are invincible in the micro range. If you own multiple crypto assets, you need safe and reliable wallets, too.
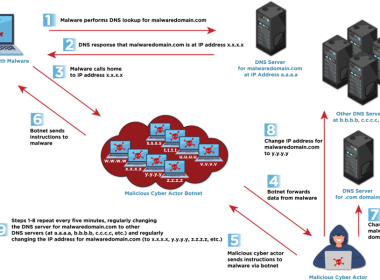
NSA and Global Allies Declare Fast Flux a National Security Threat
NSA and global cybersecurity agencies warn fast flux DNS tactic is a growing national security threat used in phishing, botnets, and ransomware.
Hacker Claims Twilio’s SendGrid Data Breach, Selling 848,000 Records (UPDATED)
This article has been updated with a statement from a Twilio spokesperson in response to Hackread.com's request. A statement from the hacker…
Hackers Exploit Stripe API for Web Skimming Card Theft on Online Stores
Cybersecurity researchers at Jscamblers have uncovered a sophisticated web-skimming campaign targeting online retailers. The campaign utilizes…
Secure Ideas Achieves CREST Accreditation and CMMC Level 1 Compliance
Jacksonville, United States, 3rd April 2025, CyberNewsWire
AutonomyAI Emerges from Stealth with $4M Pre-Seed Funding to Transform Front-End Development with Autonomous AI Agents
The first-of-its-kind solution integrates with company codebases, enabling AI agents to work in-context and generate production-grade,…
AI Image Site GenNomis Exposed 47GB of Underage Deepfakes
Cybersecurity researcher Jeremiah Fowler uncovers a massive 47.8GB database with disturbing AI-generated content belonging to GenNomis.
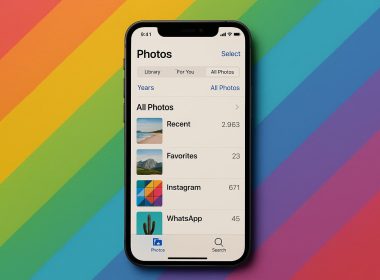
How to Recover Deleted Photos from an iPhone
Accidentally deleted some photos from your iPhone? You’re definitely not alone; most iPhone users have done it at some point. The good news is…