In total, researchers have identified around 190 malware-infected games, some of which were designed to specifically target Russian users, whereas some targeted Chinese and foreign users.
Researchers from Doctor Web have shared details of a mobile campaign that infected at least 9.3 million Android devices. Reportedly, a new class of malware was used in this campaign, which was hidden inside dozens of strategy, arcade, and shooter games.
These games were available on Huawei’s AppGallery marketplace. The main objective behind this malicious campaign was to steal device info as well as the mobile phone number of the victim.
About Android.Cynos.7.origin
Doctor Web researchers have classified the trojan as Android.Cynos.7.origin because the malware is a modified variant of the Cynos malware. They identified around 190 malicious games, some of which were designed to specifically target Russian users, whereas some targeted Chinese and foreign users.
SEE: GriftHorse Android malware hit 10 million devices in 70 countries
The Cynos program module can be integrated into Android apps and generate revenues for the attacker. This module was discovered in 2014; some of its versions implemented aggressive features, such as premium SMS sending capabilities, intercepting incoming SMS, downloading/installing other apps, downloading/launching additional modules, etc.
However, the malware strain Doctor Web researchers identified in this campaign could only collect user/device data and display ads.
List of Infected Games
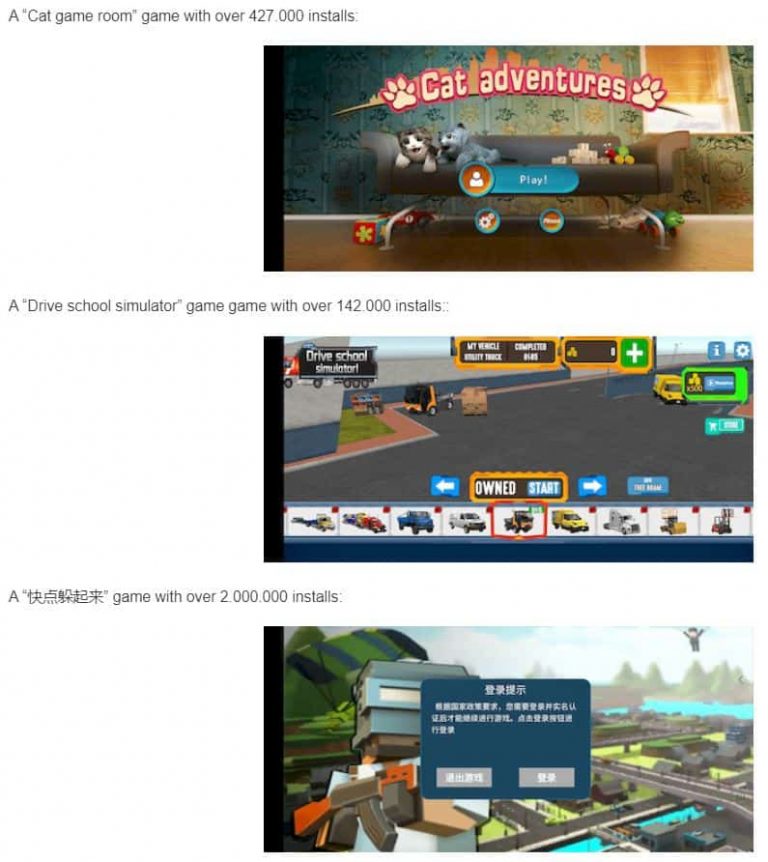
Here are the games featuring the highest number of installs.
- 快点躲起来 (Hurry up and hide) – 2,000,000 installations
- Cat game room – 427,000 installations
- Drive school simulator – 142,000 installations
What Happens When Malware Gets Installed?
After the user installs an infected app, it requests advanced permissions such as making and managing phone calls.
When this permission is granted, they use this privilege to steal phone numbers and sensitive device data like geolocation, system metadata, and mobile network parameters (country code, GSM cell ID, international GSM location area code if the app has permission to access the location).
Although mobile number leaking may appear as a harmless issue, in reality, it can cause serious harm to the user given that children are the “main target audience” of these games, researchers explained.
“Even if the mobile phone number is registered to an adult, downloading a child’s game may highly likely indicate that the child is the one who uses the mobile phone. It is very doubtful that parents would want the above data about the phone to be transferred not only to unknown foreign servers but to anyone else in general,” Doctor Web AV’s report read.
SEE: New Android malware TeaBot found stealing data, intercepting SMS
Researchers shared their findings with Huawei, and the malicious apps were later removed from the AppGallery store.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.