Cyber attackers are using encoded JavaScript files to hide malware, abusing Microsoft’s Script Encoder to disguise harmful scripts in .jse files. ANY.RUN’s sandbox helps detect and decrypt these threats, enhancing security analysis efficiency.
Cyber attackers constantly innovate new ways to hide their malicious intentions. Recently, cybersecurity researchers at ANY.RUN came across a tactic used by attackers which involves the abuse of encoded JavaScript files. Attackers have been using the Microsoft Script Encoder to disguise harmful scripts within .jse files.
This tactic allows malware to remain hidden within seemingly legitimate scripts, posing a major threat to unsuspecting users and traditional security measures.
Microsoft Script Encoder Exploited
Microsoft originally developed the Script Encoder to help developers obfuscate JavaScript and VBscript while keeping them executable with wscript and similar interpreters. This tool was initially designed to protect source code, but it has also become a valuable resource for malware developers.
By encoding JavaScript into a non-human-readable format, attackers can hide their malicious scripts. The latter can be delivered through phishing campaigns or drive-by-download attacks, where users unknowingly run the malicious script.
This obfuscation technique makes it difficult for traditional security tools to detect hidden threats. However, they can be detected faster with the help of tools, like ANY.RUN’s Script Tracer.
How to Decrypt Encoded Malicious Scripts
To view the log of the script execution, run the sample inside ANY.RUN’s sandbox.
View analysis session
After running the sample, you can discover the behaviour of the script in an isolated environment using ANY.RUN’s Script Tracer:
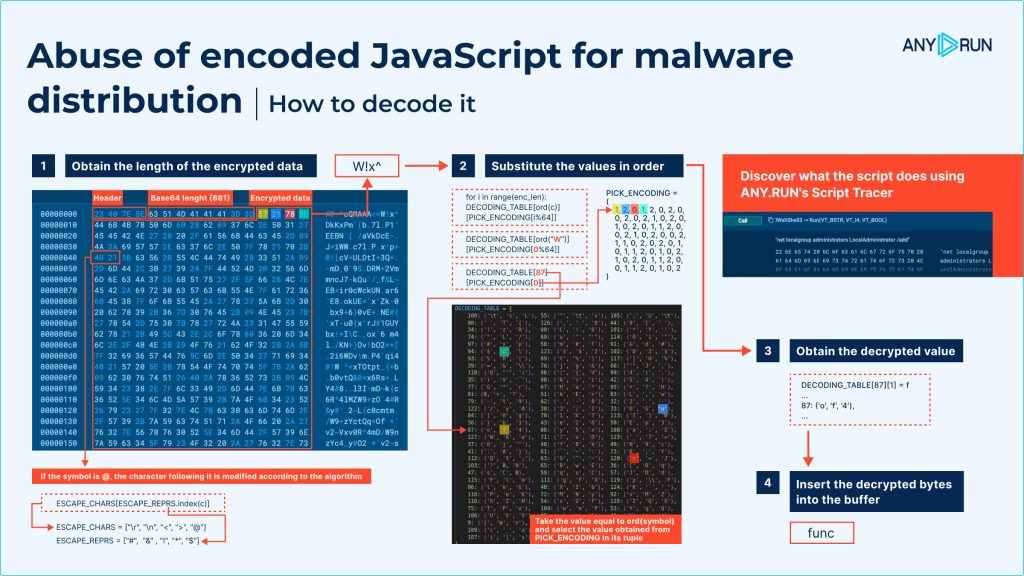
- Obtain the length of the encrypted data
Begin by identifying the length of the encoded portion of the script. While doing this, keep an eye out for the @ symbol, which serves as a key marker in the script.
When you see @, it indicates that the next character has been modified using a specific algorithm.
- Substitute values in order
With the encoded characters identified, begin the substitution process. This step involves replacing each encoded symbol with its corresponding decoded value. To decode each character in the script, follow the instructions in the image below:
- Obtain the decrypted value
As you decode each character, you will start to uncover the readable form of the script. This step-by-step decoding reveals the underlying commands hidden within the encoded data.
- Insert the decrypted bytes into the buffer
After decoding each character, store the decoded result in a buffer (a temporary space to hold the data). Continue adding decrypted characters until the entire script has been processed.
- Use the ord() function for character values
Take the numeric value of each symbol using the ord() function, then retrieve the corresponding decoded character from the predefined encoding tuple using PICK_ENCODING.
Analyzing Malicious Scripts in a Safe Environment
Manually decrypting encoded scripts can be complex and time-consuming. To make the decryption process easier and faster, you can use tools like ANY.RUN’s sandbox.
It allows you to analyze malware behaviour in a secure environment, giving you the insights you need for detailed analysis.
Sign up for a 14-day free trial for unlimited malware analysis and see how it simplifies the process.
RELATED TOPICS
- Analysis of Top Infostealers: Redline, Vidar and Formbook
- PythonAnywhere Cloud Platform Abused for Hosting Ransomware
- OpenSSF Warns of Fake Maintainers Targeting JavaScript Projects
- ANY.RUN Upgrades Threat Intelligence to Identify Emerging Threats
- Visa warns of Baka JavaScript skimmer capable of evading detection