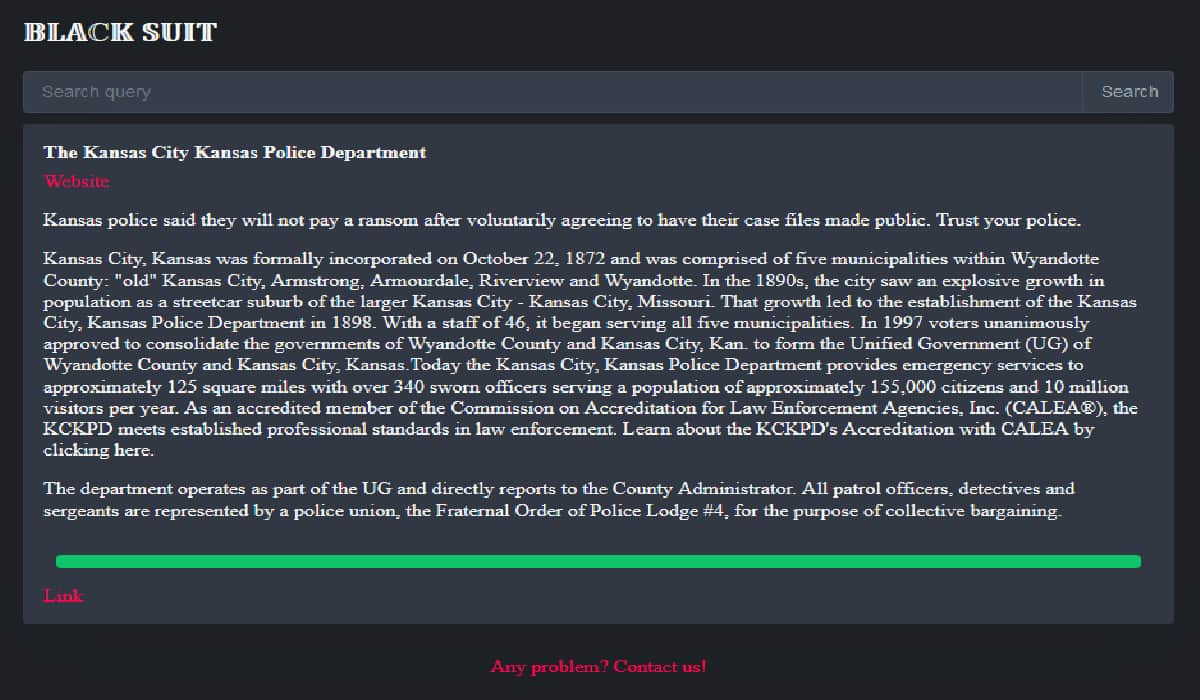
The Kansas City, Kansas Police Department (KCKPD) is facing a major security breach after the notorious BlackSuit ransomware group leaked what they allege is stolen department data on their official dark web leak site.
The site serves as a platform to showcase their victims. A look at the screenshot below shows the BlackSuit ransomware group is blaming the KCKPD for the leak, claiming they “voluntarily agreed to have their case files made public.”
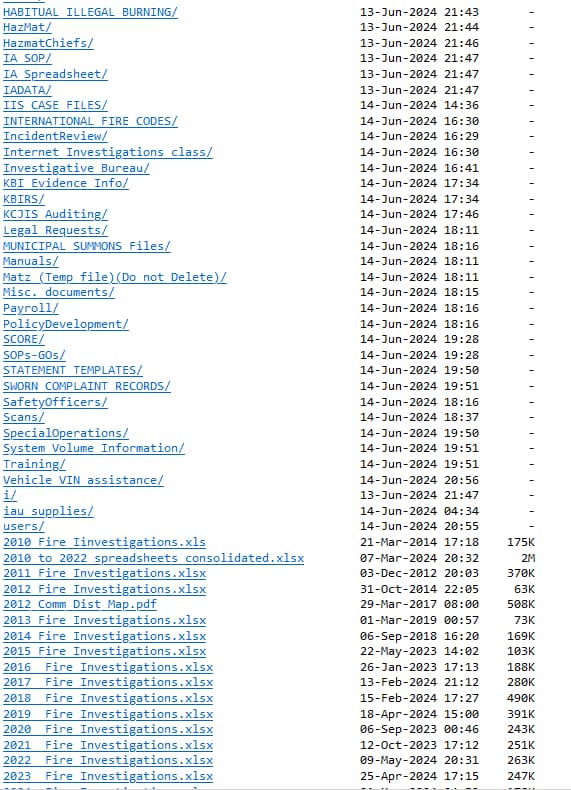
This leak comes after failed negotiations between the KCKPD and the attackers in which authorities were asked to ransom, a demand rejected by the police department. As seen by Hackread.com, the leaked KCKPD data contains a trove of police records including the following:
- Manuals
- Payroll data
- Case reports
- Investigations
- Legal requests
- Employee data
- Fingerprint database
- Evidence room information
- Details of special operations
- Homicide crime scene photos
- Communication between the police and fire department
And a lot more…
The KCKPD has not confirmed the extent of the leak or its authenticity or commented on the news. However, Hackread.com can confirm that the leaked information and files are as recent as June 13, 2024.
For your information, BlackSuit is suspected to be a rebrand of Royal, a notorious ransomware cartel and a rebrand of the Conti ransomware gang. The group emerged in May 2023 and has been among the most active groups, having victimized a staggering 58 organizations so far in 2024.
The KCKPD serves over 156,000 residents, so the leak, if authentic, may pose significant public safety concerns as it could expose details of past investigations, potentially leading to identity theft and financial scams. The breach could also damage public trust in the KCKPD’s ability to protect sensitive information.
The incident highlights the need for increased cybersecurity measures across all law enforcement agencies, investing in robust digital defences and fostering a culture of cyber awareness. Residents of Kansas City must remain cautious about unsolicited calls, emails, or texts, and be proactive about credit monitoring and identity theft protection.
RELATED TOPICS