DragonRank, a Chinese-speaking hacking group, has compromised 30+ Windows servers globally. They exploit IIS vulnerabilities to manipulate SEO rankings, distribute scam websites, and spread malware like PlugX and BadIIS.
A Chinese-speaking hacking group, known as “DragonRank,” has been discovered compromising over 30 Windows servers across the globe, including in Thailand, India, Korea, Belgium, Netherlands, and China.
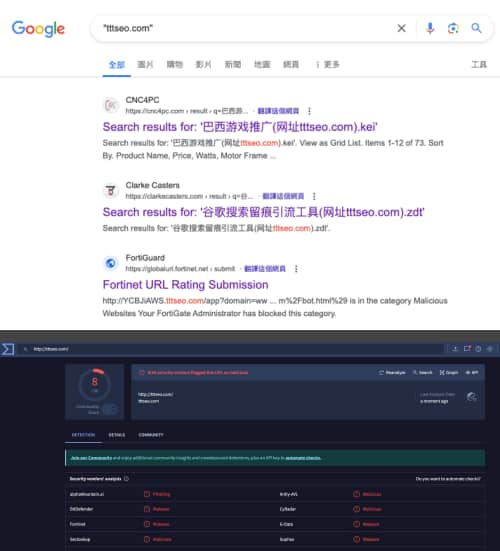
The group’s primary goal is to manipulate search engine crawlers and disrupt the Search Engine Optimization (SEO) of affected sites, ultimately distributing scam websites to unsuspecting users.
How the Attack Works
The DragonRank hacking group gains initial access to Windows Internet Information Services (IIS) servers by exploiting vulnerabilities in web application services, such as phpMyAdmin, WordPress, or similar web applications. Once they obtain the ability to execute remote code or upload files on the targeted site, they deploy a web shell like ASPXspy, granting them control over the compromised server.
According to Cisco Talos’ long and technical report shared with Hackread.com ahead of publishing on Tuesday, the group then utilizes the web shell to collect system information and launch malware, including PlugX and BadIIS, as well as credential-harvesting utilities like Mimikatz, PrintNotifyPotato, BadPotato, and GodPotato. They also breach additional Windows IIS servers in the target’s network, either through web shell deployment or by exploiting remote desktop logins using acquired credentials.
For your information, PlugX is a well-known RAT (remote access tool) equipped with modular plugins and property configurations, deployed by various Chinese-speaking cyber threat actors for over ten years. The PlugX configuration in this campaign contains all necessary values and information to properly run the executable.
On the other hand, BadIIS is a malware used to manipulate search engine crawlers and hyperlink jumps. The version of BadIIS detected in this campaign shares similar traits with the one mentioned (PDF) at Black Hat USA 2021, including configuration as an IIS proxy and capabilities for SEO fraud.
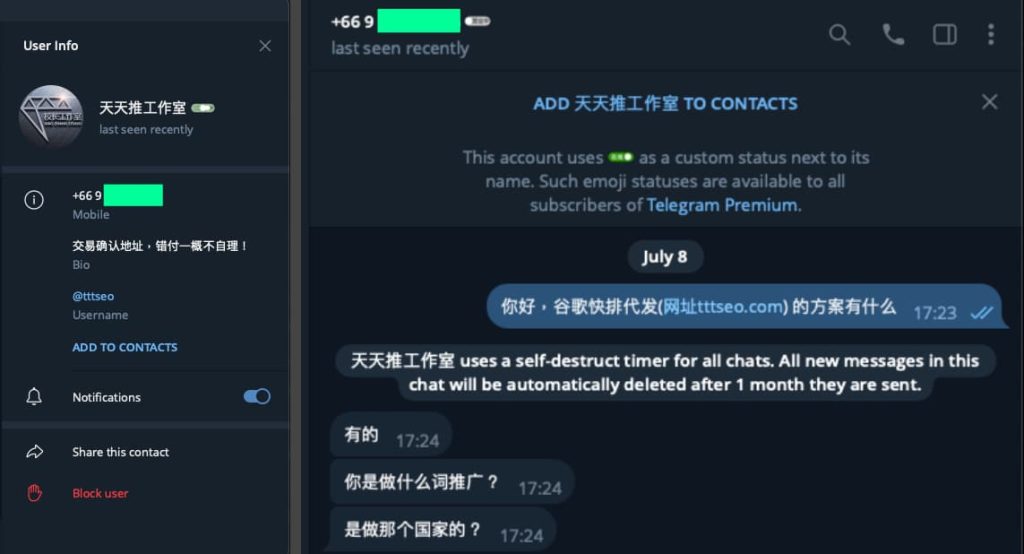
Interestingly, researchers also noted that DragonRank operates much like a business, with a commercial website offering their services in both Chinese and English. They engage with clients through platforms like Telegram and QQ, providing tailored SEO fraud services. Their business model includes a cautionary note about transaction confirmations, suggesting they operate with a level of professionalism uncommon in typical cybercrime groups.
Nevertheless, the DragonRank hacking group’s activities are a threat to online security, as they can drive traffic to malicious sites, increase the visibility of fraudulent content, or disrupt competitors by artificially inflating or deflating rankings.
These attacks can harm a company’s online presence, lead to financial losses, and damage its reputation by associating the brand with deceptive or harmful practices. Therefore, businesses and IT departments must:
- Use Advanced Threat Detection: Implement solutions that can detect and respond to sophisticated malware like PlugX.
- Regularly Update Security Measures: Ensure all systems, especially web servers, are patched against known vulnerabilities.
- Monitor Network Traffic: Look for unusual outbound connections or changes in server behavior that might indicate malware like BadIIS.
- Educate Staff: Awareness training on cyber threats can help in early detection of phishing or other social engineering attempts.
RELATED TOPICS
- Chinese SMS Phishing Group Hits iPhone Users in India Post Scam
- ValleyRAT Malware Targets Chinese Windows Users in New Attack
- Chinese Velvet Ant APT Target F5 Devices in Years-Long Espionage
- “Unfading Sea Haze” Hackers Hit Military Targets in South China Sea
- Chinese Blackwood APT Deploys NSPX30 Backdoor in Cyberespionage