Dell faces its third data leak in a week as hacker “grep” continues targeting the tech giant. Sensitive internal files, including project documents and MFA data, were exposed. Dell has yet to issue a formal response.
Dell has allegedly been hit with yet another data leak, marking the third such incident in a week. The threat actor, who goes by the alias “grep,” has claimed responsibility for the latest breach and continues to target the tech giant.
This time, the hacker has leaked approximately 500 MB of sensitive data, including internal documents, PDFs, images, internal device testing videos, and Multi-Factor Authentication (MFA) data, which if confirmed by Dell could further escalate concerns over the company’s data security.
According to information obtained by Hackread.com, the hacker shared details of the data leak, stating that Dell suffered a third breach that exposed internal files. The hacker revealed, “I knew Dell would fix their failure without confirming or denying my claims, for the same reason I had exfiltrated more data when I breached the internal employees, which was not leaked and waited for this exact moment.”
The leaked data includes access vectors and references to Chinese infrastructure, which, if not at a large scale, could still have some impact on the company’s operations.
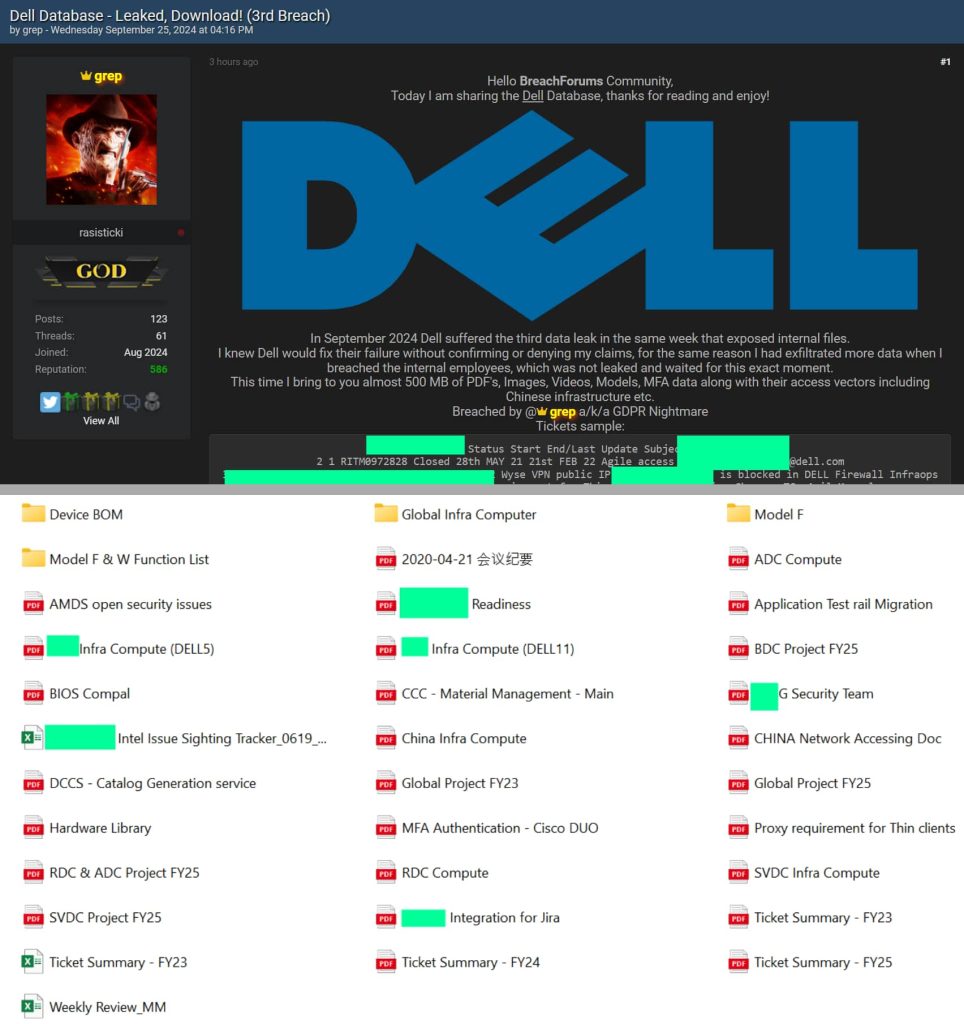
Leaked Data Includes Internal Tickets and Infrastructure Documents
Among the leaked data is a CVS file titled “Ticket Summary – FY23,” which includes details of Dell’s internal ticketing system. Some of the entries shared in the leak include:
- Incident reports on Agile access, VPN issues, proxy requirements for testing, and application migrations.
- Ticket summaries that highlight VPN enhancements, DevOps software access requests, and network setups.
Additionally, the hacker shared a range of files and folders containing critical infrastructure information, such as:
- “China Infra Compute.pdf”
- “Global Project FY23.pdf” and “Global Project FY25.pdf”
- “MFA Authentication – Cisco DUO.pdf”
- Various project summaries and security-related documents.
The documents released by “grep” provide a snapshot of Dell’s internal operations and project infrastructure, revealing sensitive information that could pose security risks if exploited. Therefore, for security reasons; we are withholding specific details of the leaked files.
Pattern of Breaches: A Coordinated Attack or Piecemeal Leaks?
This third leak follows two previous data breaches conducted by the same hacker within a short time frame. On September 19, 2024, “grep” leaked data belonging to over 12,000 Dell employees, sparking an internal investigation. Just days later, on September 22, more sensitive internal files were released, allegedly compromised through Dell’s use of Atlassian tools.
In today’s data leak, the hacker clarified that all the data was stolen during a single breach, but he is strategically leaking it in parts. This statement eliminates speculation that Dell is facing repeated attacks, confirming instead that the data is being gradually released from one initial breach.
It is worth noting that Dell has yet to confirm the extent of the damage or whether the hacker gained access through a third-party vendor, as seen in other recent incidents. The hacker’s method aligns with his earlier attack, where he leaked 12,000 Twilio records from a compromised customer. Twilio confirmed to Hackread.com that it was a third-party breach, which resulted in the leak of only one Twilio customer’s data.
Dell’s Response and Next Steps
So far, Dell has not released a formal statement regarding today’s data leak. With three data leaks in just one week, concerns about Dell’s cybersecurity are growing. Hackread.com has reached out to Dell for comment, and this article will be updated as more information becomes available. Stay tuned!









