A malvertising campaign is exploiting Meta’s platform to spread SYS01 infostealer, targeting men 45+ via fake ads for popular software. The malware steals Facebook credentials, hijacks accounts espicially those administrating business pages, and spreads further attacks globally.
A new malvertising campaign is exploiting Meta’s advertising platform to spread the SYS01 infostealer, a cybersecurity threat known to Meta and particularly Facebook users for stealing their personal information.
What makes this attack targeted is that millions of users globally, specifically men aged 45 and above, are potential victims of this ongoing attack, which cleverly disguises itself as advertisements for popular software, games, and online services.
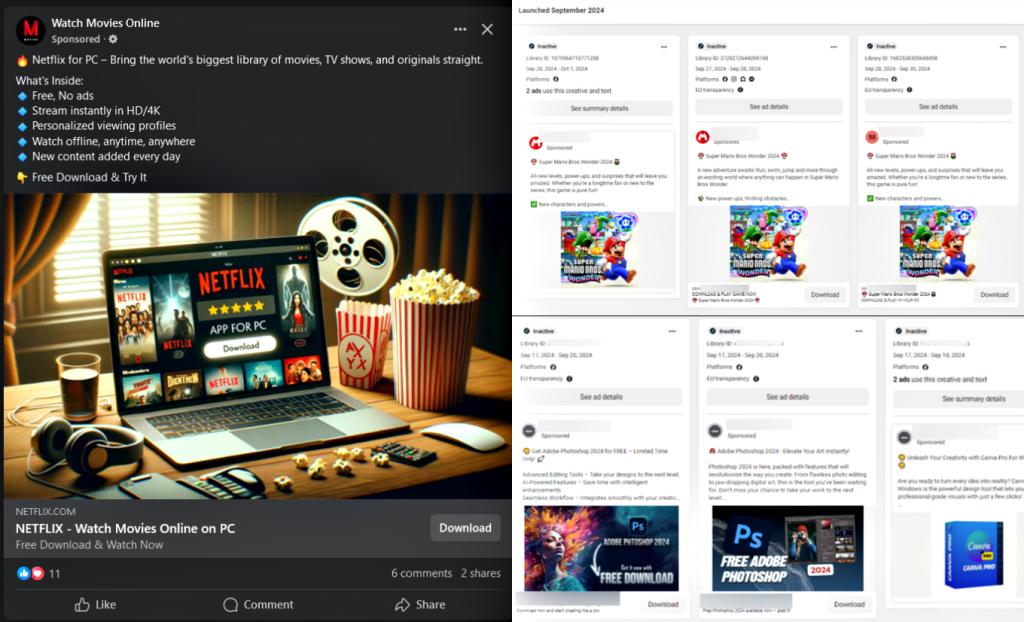
This campaign, first detected in September 2024, stands out due to its impersonation tactics and popular brands that it exploits. Instead of focusing on a single lure, the attackers mimic a broad range of trusted brands, including productivity tools like Office 365, creative software like Canva and Adobe Photoshop, VPN services like ExpressVPN, streaming platforms like Netflix, messaging apps like Telegram, and even popular video games like Super Mario Bros Wonder.
How the Attack Works:
According to Bitdefender’s blog post shared with Hackread.com ahead of publishing on Wednesday, the malicious ads often lead to MediaFire links offering direct downloads of seemingly legitimate software. These downloads, packaged as zip archives, contain a malicious Electron application.
Once executed, this application drops and runs the SYS01 infostealer, often while displaying a decoy app that mimics the advertised software. This deceptive tactic makes it difficult for victims to realize they’ve been compromised.
For your information, an Electron application is a type of desktop app built with web technologies like HTML, CSS, and JavaScript. Electron is an open-source framework developed by GitHub that allows developers to create cross-platform applications that run on Windows, macOS, and Linux, all from a single codebase.
In this attack however, behind the scenes, the Electron app uses obfuscated Javascript code and a standalone 7zip executable to extract a password-protected archive containing the core malware components. This archive includes PHP scripts responsible for installing the infostealer and establishing persistence on the victim’s system. The malware also incorporates anti-sandbox checks to evade detection by security researchers.
Stealing Data and Hijacking Accounts:
The primary goal of the SYS01 infostealer is to harvest Facebook credentials, particularly those associated with business accounts. These compromised accounts are then used to further attacks/scams.
What’s worse, the attack also leverages the advertising capabilities of hijacked accounts, allowing attackers to create new malicious ads that appear more legitimate and easily bypass security filters. This creates a self-sustaining cycle where stolen accounts are used to spread the malware even further. The stolen credentials are also likely sold on underground marketplaces, further enriching the criminals.
Global Reach and Protection
While the campaign has a global reach, impacting users in the EU, North America, Australia, and Asia, Bitdefender could not verify the full extent of its impact, especially outside the EU, which remains unclear due to limited data transparency.
Nevertheless, if you are on Facebook—especially if you run a business page—you must watch out for SYS01 Infostealer and similar threats. While using common sense is essential, here are some vital steps you should take:
- Monitor your accounts: Regularly check your Facebook and other social media accounts for suspicious activity. Report any unauthorized access immediately and change your passwords.
- Be wary of ads: Exercise caution when clicking on ads, especially those offering free downloads or deals that seem too good to be true. Verify the source before downloading any software.
- Stick to official sources: Download software directly from official websites or trusted app stores. Avoid third-party platforms and file-sharing services.
- Use strong security software: Install reputable security software and keep it updated. Choose a solution that offers real-time protection and advanced threat detection.
- Enable two-factor authentication (2FA): Activate 2FA on your Facebook and other important online accounts for added security.









