Google fixed the vulnerability only after the security researcher ended up disclosing its technical details online.
Imagine receiving an email from the White House, you’d be super amazed at being a recipient. Yet, it could be that the email you received looks like it is from the White House but in actuality is from another malicious source.
Such an identity misrepresentation could take place through a classical email spoofing attack in which the “From” value of the mail received is tampered with. To tackle this, we have two rules in place that help prevent such spoofing:
- Sender Policy Framework (SPF)
- Domain-based Message Authentication, Reporting, and Conformance (DMARC).
This helps email providers prevent attackers from using their services to send such fake emails and at the same time informs users if a suspicious tampered email finds its way into their inbox. However, what happens when a spoofed email also evades these rules and gets to the user regardless? Unless you check really closely, you may just fall for it.
See: Google admits third-party app developers read your Gmail emails
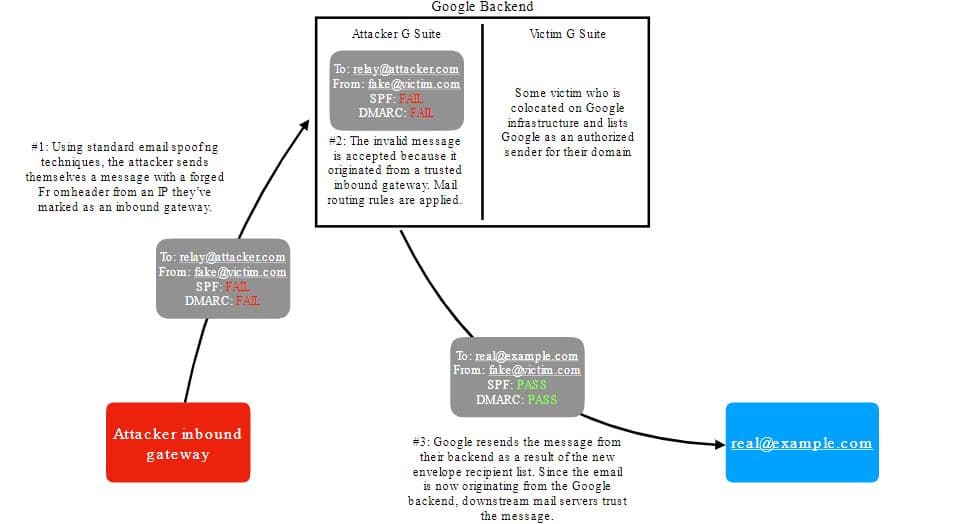
This is exactly what happened recently according to a report by researcher Allison Husain with users being able to send spoofed emails which were interpreted as being completely compliant with both SPF and DMARC standards.
Furthermore, by using custom email routing rules, a user could also change the email recipient’s address redirecting any incoming emails.
Elaborating, the researcher stated in her blog post that:
Worryingly, the recipient value is accepted by G Suite without performing any validation to ensure that I own either the destination email address or the destination domain.
This buggy feature would let me redirect incoming emails, including spoofed emails, to someone else using Google’s backend so that it no longer appears to be spoofed according to SPF and DMARC if the victim also designates Google as an approved sender!
To conclude, the issue was first discovered on 1st April 2020 and then reported 2 days later on the 3rd to Google. Subsequently on 16 August, even though Google accepted the flaw’s existence, it was marked as duplicate 5 days later on the 21st.
But then came a 10-day gap where there were no updates on the actions that were being taken to fix the flaw. Seeing this, Allison disclosed the vulnerability publicly on 19 August after giving Google a deadline. Nonetheless, 6 hours after the disclosure, Google issued a fix using “return-path modification and anti-abuse mechanisms”.
See: Google to stop scanning user emails for Gmail ads
Hence, users can rest assured now that they’re safe. Regardless, this does though give us a sense of irresponsibility on behalf of Google where they took so long to remedy the situation.
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.