Cybersecurity researchers at the Positive Technologies Expert Security Center (PT ESC) have found a sneaky malware campaign targeting the Python Package Index (PyPI), a popular online repository for Python software. The attack focused on developers, machine learning engineers, and AI enthusiasts who might integrate DeepSeek AI into their projects.
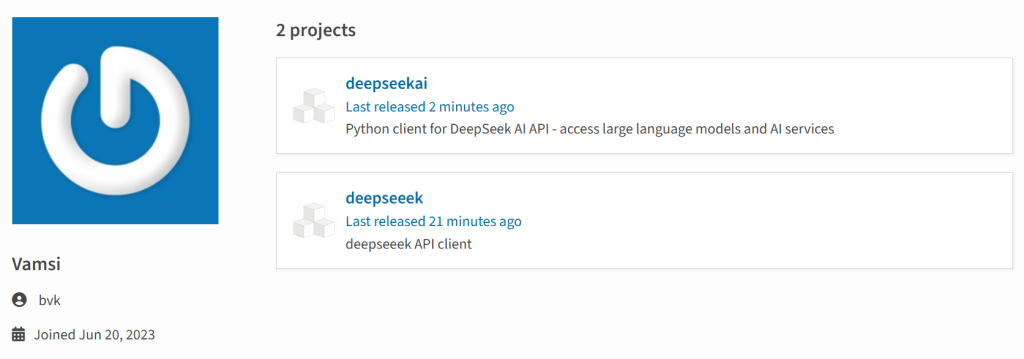
It all began on January 29, 2025, when a suspicious user named “bvk,” whose account had been inactive since its creation in June 2023, uploaded two malicious packages: deepseeek or deepseekai. These packages were designed to mimic legitimate integrations with DeepSeek but contained malicious code aimed at stealing sensitive information from users’ systems.
Once installed, the harmful packages executed commands that collected system information and stole environment variables. These variables often contain critical data, such as credentials for cloud storage, database access, or other infrastructure resources. The stolen information was then sent to a command-and-control (C2) server hosted on Pipedream, a developer integration platform.
Interestingly, according to PT ESC’s blog post shared with Hackread.com, the attackers appeared to use an AI-powered assistant to write their malicious script, as evidenced by the code’s comments explaining its functionality. AI-generated content and codes have become a significant cybersecurity threat, with experts warning that the risk is only growing.
Quick Action
After discovering the malicious packages, Positive Technologies immediately alerted PyPI administrators, who quarantined and deleted the packages within an hour. However, during that short window, the packages had already been downloaded 222 times across various tools and methods in the following countries:
- US: 117 downloads
- China: 36 downloads
- Russia: 12 downloads
- Other countries, including Germany, Canada, and Hong Kong, also reported downloads.
Exploiting DeepSeek’s Popularity
Although the attack was contained before causing large-scale harm, it presents important questions about the security of open-source repositories. Cybercriminals frequently monitor emerging trends and exploit them to trick unsuspecting users. In this example, the popularity of DeepSeek likely attracted malicious actors seeking to exploit its growing user base.
In a comment to Hackread.com, Jason Soroko, Senior Fellow at Sectigo, emphasized the impact of this incident stating, “This report underscores how attackers exploit trusted naming conventions and the reliance on authentic package sources within the open-source ecosystem. While the threat was neutralized quickly, it serves as a reminder of the growing risks associated with software supply chains.”
Protecting Yourself from Similar Threats
This incident is a good sign to be careful when downloading and installing software, especially from public repositories like PyPI. Here are a few quick tips to help you stay safe:
- Security Tools: Use services like Positive Technologies’ PyAnalysis, which monitors PyPI for malicious activity in real-time.
- Verify Package Sources: Only download well-established packages with a strong reputation. Be cautious of newly uploaded tools, especially those with names similar to popular projects.
- Scan Dependencies: Use tools to analyze the code of packages before installing them.
- Monitor Environment Variables: Keep an eye on sensitive data stored in your system and limit its exposure where possible.