Hackers stole $243M from a single victim by posing as Google and Gemini support, resetting 2FA to access crypto. Investigator ZachXBT helped trace the thieves, leading to arrests and the recovery of millions.
A major breakthrough in cryptocurrency theft came to light on September 19, 2024, when anonymous Twitter user and crypto investigator ZachXBT (@ZachXBT) revealed his investigation into one of the largest crypto heists in history.
The theft of $243 million worth of cryptocurrency from a single Genesis creditor, was carried out through a sophisticated social engineering attack in August 2024. ZachXBT’s investigation played a key role in tracing the alleged culprits, which led to multiple arrests and the recovery of millions in stolen funds.
The Heist
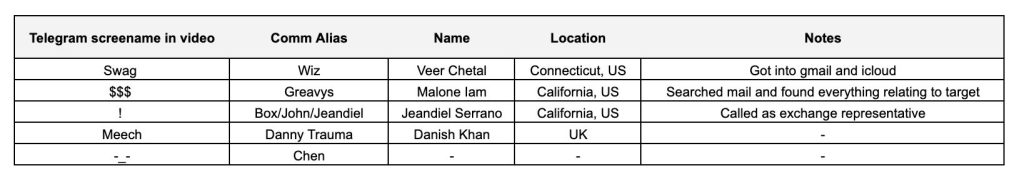
On August 19, 2024, a group of cybercriminals identified as Greavys (Malone Iam), Wiz (Veer Chetal), and Box (Jeandiel Serrano) allegedly conducted a phishing operation targeting a victim in Washington, D.C.
The attackers, posing as support personnel from Google and Gemini, tricked the victim into resetting two-factor authentication (2FA) and transferring funds to a compromised wallet. The group further exploited the victim using remote access software AnyDesk to reveal private keys stored in the victim’s Bitcoin core.
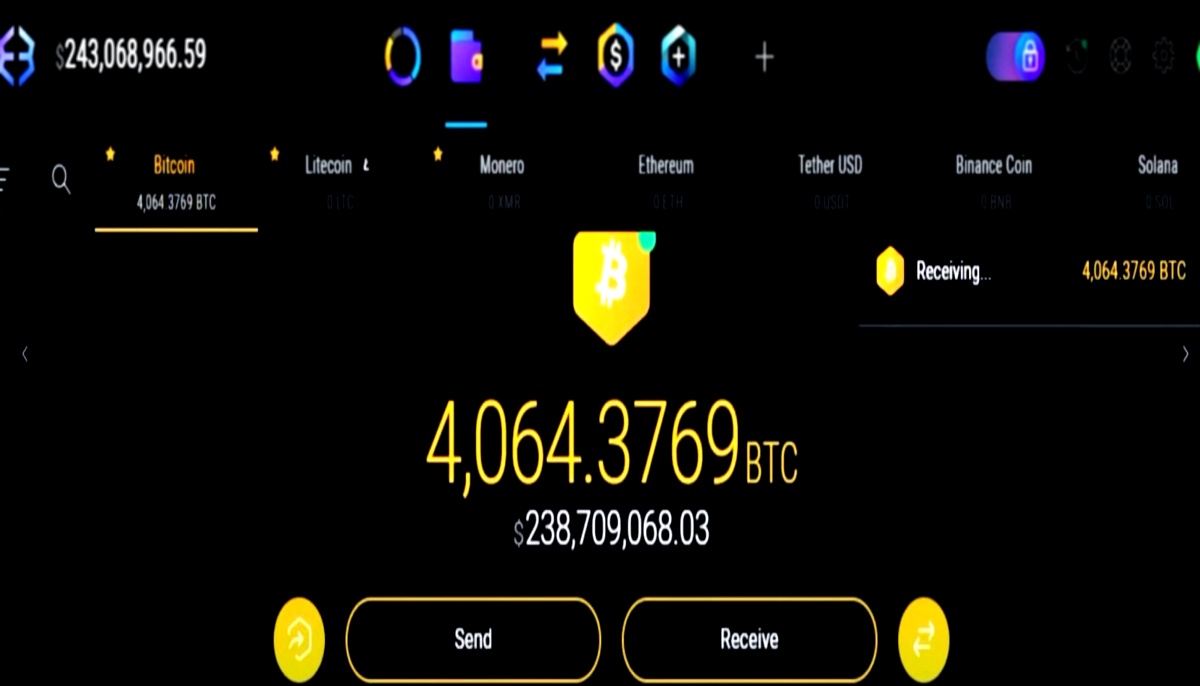
ZachXBT provided transaction hashes that tracked the flow of Bitcoin, confirming that 59.34 BTC and 14.88 BTC were stolen during the attack, followed by the transfer of a massive 4,064 BTC, worth $243 million at the time, which was quickly split among the attackers.
3/ Here is a private video recording showing the live reaction by multiple of the threat actors to receiving $238M.
— ZachXBT (@zachxbt) September 19, 2024
Theft txn hash
4064 BTC – Aug 19 at 4:05 am UTC
4b277ba298830ea538086114803b9487558bb093b5083e383e94db687fbe9090 pic.twitter.com/djSxBTkOF8
Criminals’ Identities Unveiled
According to ZachXBT’s in-depth investigation, the details of which he shared in a must read detailed Twitter thread, revealed the identities of the thieves. Allegedly, Wiz (Veer Chetal) made a critical error during a screenshare session, where his real name was exposed.
Furthermore, he and his friend Aakaash (Light/Dark) allegedly attempted to launder the stolen funds through exchanges such as eXch and Thorswap. Despite efforts to cover their tracks, they linked laundered funds to the stolen assets by reusing addresses.
Greavys, a key figure in the scam, flaunted his newfound wealth by purchasing luxury items, including over 10 cars and expensive nights out in Los Angeles and Miami. His flashy lifestyle, documented on social media, helped investigators track his location.
Box (Jeandiel Serrano), who impersonated a Gemini representative during the heist, also left traces linking him to the stolen funds. A shared profile picture across multiple platforms and a series of missteps in cryptocurrency transactions allowed investigators to trace $18 million back to him.
Arrests and Asset Recovery
ZachXBT’s collaboration with @CFInvestigators, @zeroshadow_io, and the Binance Security Team resulted in the freezing of over $9 million in assets, with $500,000 already returned to the victim. His findings also led to the arrest of Greavys and Box, who were taken into custody in Miami and Los Angeles, respectively, on September 18, 2024.
Anoop Nannra, Co-founder and CEO at Trugard, a real-time web3 intelligence and security platform, commented on the development stating, “Social engineering, a classic decades-old web2 threat vector, used to gain access to private keys for wallets is sadly more common than most in web3 are willing to admit. I’ve often said all the attack vectors of the internet will continue to plague the growth, adoption, and confidence in web3 and digital assets.”
“Over the past decade that I have been in the blockchain space, I have lost count of the number of times a prospective customer has asked, ‘If I build it on the blockchain, am I more secure?’. Sadly the answer is no,” Anoop explained.
He further warned that “This is not to say that exploits, vulnerabilities, or threat vectors that are uniquely born from web3 are any less or more novel since these are being both created and uncovered as innovation continues in web3, but from a hacker’s perspective, the old methods are still valid.“
Anoop also appreciated ZachXBT’s efforts stating, “The work of the crypto investigator, ZachXBT, to identify these particular cyber criminals, is a textbook example of a tactician at their best. I’ve seen similar investigative discipline in other cases, and each time, the perpetrators are caught, tried, sent to prison, and sometimes, assets recovered.”
Legal Proceedings
The Department of Justice (DOJ) confirmed the arrests in a press release, announcing charges of conspiracy to steal and launder cryptocurrency against Malone Lam (aka “Anne Hathaway” and “$$$”) and Jeandiel Serrano (aka “VersaceGod” and “@SkidStar”).
The indictment outlines how the pair, alongside other conspirators, executed a series of crypto thefts, using complex laundering techniques to conceal the funds. Both individuals appeared in U.S. District Court following their arrests.
ZachXBT’s investigative work played a crucial role in cracking one of the largest cryptocurrency theft cases of the year. As law enforcement continues to crack the network behind the crime, ZachXBT has stated that updates will follow as the legal proceedings unfold.