Massive Pakistani cybercrime network HeartSender has been shut down in a joint US-Dutch operation. Learn how their phishing kits and other tools caused millions in losses and impacted countless victims.
U.S. and Dutch law enforcement have taken down a major Pakistani cybercrime network known as HeartSender, or Saim Raza. The takedown was part of Operation Heart Blocker in which authorities seized multiple domains and servers used by the group including Heartsender(.)com and Botsdetector(.)com.
Visitors to these sites are greeted with the following message: “This domain has been seized in accordance with a seizure warrant issued pursuant to 18 U.S.C. § 1030 in the United States District Court for the Southern District of Texas as part of a coordinated law enforcement operation and action by: The U.S. Department of Justice’s Computer Crime & Intellectual Property Section, the Federal Bureau of Investigation, and the Dutch National Police.”
This takedown closely follows another international law enforcement action dubbed Operation Talent resulting in the seizure of two major online cybercrime-as-a-service marketplaces, Cracked and Nulled.
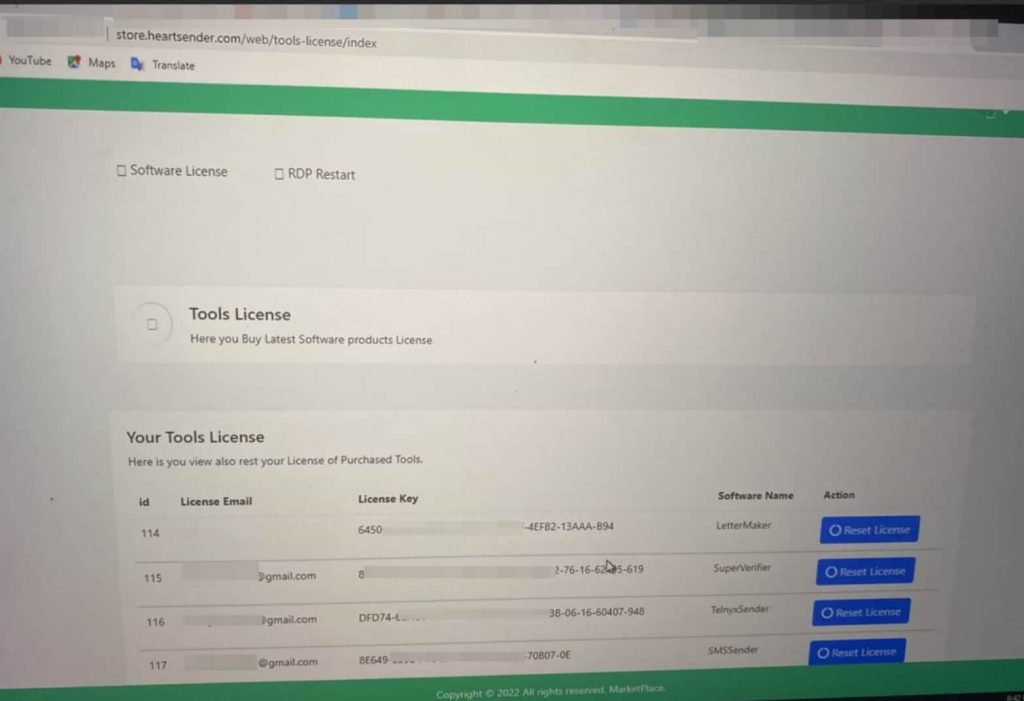
HeartSender specialized in developing and distributing cybercrime tools, including phishing kits for deceptive emails, credential-stealing software, and resources for large-scale spam campaigns. These tools were sold to other cybercriminals, enabling them to carry out a range of attacks.
The US Department of Justice states that these tools are estimated to have caused over $3 million in losses to victims. Furthermore, the seizure of HeartSender’s servers yielded millions of records containing sensitive information belonging to their victims.
HeartSender ran multiple online storefronts and used platforms like YouTube to promote its malicious products. The network specialized in offering a full suite of cybercrime tools, enabling criminals to automate and scale large-scale attacks worldwide. HeartSender also provided access to other compromised resources, such as cPanels, SMTP servers, and WordPress accounts, further expanding the scope of their illicit services.
The investigation leading to the takedown uncovered a vast trove of stolen data, including millions of victim records. Among them were around 100,000 login credentials belonging to individuals in the Netherlands, highlighting the widespread reach of HeartSender’s cybercrime operations.
Apart from law enforcement, HeartSender has been on the radar of cybersecurity researchers for years. Independent journalist Brian Krebs previously reported on the group’s operational security shortcomings, including malware infections within their own network and significant security vulnerabilities in their services. These vulnerabilities reportedly exposed customer data and internal operations to unauthorized access.
Krebs notes that the group was called The Manipulators. Krebs reveals that Saim Raza “for the past decade has peddled a popular spamming and phishing service variously called “Fudtools,” “Fudpage,” “Fudsender,” “FudCo,” etc.” Here FUD stands for Fully Un-Detectable.
The dismantling of HeartSender represents yet another victory in the ongoing fight against cybercrime, disrupting a key source of malicious tools and potentially preventing further harm to countless individuals and organizations.