The issue of GitHub data protection is increasingly discussed among developers on platforms like Reddit, X, and HackerNews. This year alone, GitHub has been in the news multiple times due to malware incidents, high-severity vulnerabilities, and data deletion events, all of which pose risks to users’ data.
How can developers secure their GitHub environments? While widely recommended practices include least-privilege access controls, routine testing, API authentication, frequent rotation of access tokens, and using SSH keys, backups deserve particular focus. Establishing a reliable GitHub backup system is essential for safeguarding data effectively.
Why back up your GitHub account?
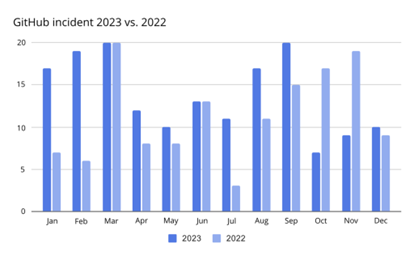
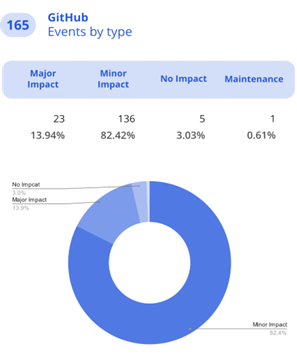
According to The State of DevOps Threats Report by GitProtect.io, the number of incidents that impacted GitHub users in 2023 grew by over 21%. And around 13.94% of events that took place had a major impact on the service.
If you check Q1 and Q2 of 2024, you will see that there have already been 70+ incidents that influence GitHub users in various ways. Just to note, in 2023 there were 160+ different incidents, starting from major impact to maintenance.
Why is it important to back up your GitHub environment? Anything can happen, and it’s always wise to prepare for worst-case scenarios. In such cases, having a backup can help by:
- Protect GitHub repositories and metadata against outages and other unpredictable threats, as it allows the restoration of a copy to another location and ensures workflow and business continuity,
- Safeguard against human errors, like accidental deletion of files,
- Ensure data recoverability in case of a ransomware attack, as backup is the final line of protection,
- Fulfill the Shared Responsibility Model which defines the roles and responsibilities of GitHub and its users. Here it’s worth mentioning that GitHub data protection is the user’s duty. In GitHub Terms of Service, it’s written: “You are responsible for keeping your Account secure while you use our Service. We offer tools such as two-factor authentication to help you maintain your Account’s security, but the content of your Account and its security are up to you.”
- Meet security compliance and data retention requirements, as the majority of security protocols and compliance regulations require organizations to have longer retention times, backup, and Disaster Recovery guarantees. GDPR, HIPAA, PCI DSS, FedRAMP, ISO/IEC 27001, FINRA, HITECH, NIS 2 Directive, etc. – they all require organizations to have a backup.
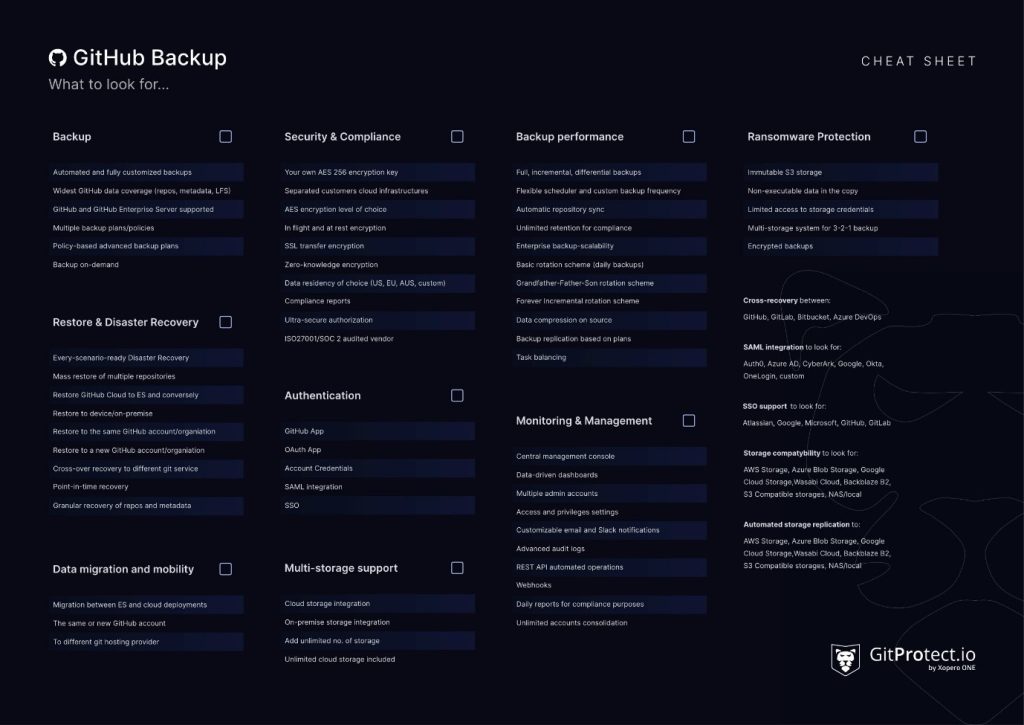
Top 10 tips to make sure your GitHub backup plan is effective
Considering all the threats, an effective backup plan should help to foresee any disaster scenario and guarantee that all the GitHub account data won’t be lost.
Tip 1: Full data coverage
Efficient backup should include all the repositories, and metadata, such as issues, pull requests, issue comments, webhooks, wiki, labels, deployment keys, projects, pipelines, and Git LFS. It will help to ensure complete repo integrity and full data protection.
Tip 2: Backup automation
It’s important to have the possibility to automate backup processes by scheduling backup policies at the most appropriate time and frequency. For example, set up a backup plan that triggers a copy every 4 hours.
Tip 3: Various backup performance schemes
Not to overload your storage, you should have the option to define different rotation and performance schemes for every backup copy you set up. They may be full, incremental, or differential backup copies.
Tip 4: Multi-storage consistency
By having a few copies in different storage locations, you can eliminate any risk of a disaster and meet the 3-2-1 backup rule which requires to have at least 3 backup copies in 2 or more storage locations, with 1 offsite.
Moreover, when it comes to storage destinations, you should be able to back up your repository and other related data to both local and cloud storage instances.
Tip 5: Backup replication
Having a few copies in various locations isn’t enough. You should make sure that you can enable replication between backup storage destinations. In this case, all the copies will be consistent and in the event of failure, you will be able to restore your data from any of the storage instances if one of them fails to run.
Tip 6: Long-term retention
Retention is closely related to compliance and data recovery from any point in the past. By default, GitHub stores build logs for 90 days. However, it might be not enough for those organizations that operate in regulated industries or require much longer retention times.
A backup solution should help solve this issue by allowing long-term or even unlimited retention. Thus, an organization will be able to recover its data from any point in time, for example, from 3 or 5 years prior.
Tip 7: Transparent management and monitoring
Not all team members should have the same access to backups. Hence, the backup software should allow you to set various roles and assign different responsibilities to your team members. For example, there may be those, who are either responsible for setting up GitHub backups, triggering recovery in case of a failure, only viewing backup performance, or system administrators who can operate without restrictions.
What is more, you should always get notifications when your backup or restore was performed with details and statuses. There can be different ways of notifications – email, Slack, webhooks as well as a dedicated console with all data-driven information, tasks, SLA, and compliance reports.
Tip 8: In-flight and at-rest encryption
Your GitHub repo and metadata should be protected at every stage – in-flight, during the transmission, and at rest. Moreover, as an additional security measure, you should be able to set your personal encryption key.
Also, your device should have no information about the encryption key, it should receive it only during the backup performance to keep up with the zero-encryption approach.
Tip 9: Ransomware protection
As backup is a final line of defence, it must be ransomware-proof. Immutable storage that helps keep data in a non-executable format, every-scenario-ready Disaster Recovery, encryption should be arranged and work as a clock to ensure your GitHub data protection and recoverability. Moreover, backup software should guarantee secure access authorization, for example, via SAML SSO protocols.
Tip 10: Restore and Disaster Recovery
Having a consistent GitHub backup should mean that you can restore your data in any event of failure – ransomware attack, service outage, infrastructure downtime, etc. The backup solution should allow you to restore your data fully or granularly – only selected metadata or repositories.
Regarding the restore destinations, the solution should also foresee any event of failure. Thus, you should have the option to recover your GitHub data to the same or a new GitHub account, to your local machine, or cross-over recovery to another Git hosting platform, like GitLab, Bitbucket, or Azure DevOps.
What’s more, during the recovery process, you shouldn’t overwrite the existing data but have the opportunity to restore it as a new file.
Is my GitHub backup effective?
To ensure that your backup processes are efficient, your backup should respond to the mentioned tips.
However, how to build your backup strategy for your GitHub environment is the question you should answer taking into account your security and compliance requirements, the size of your GitHub ecosystem, the evaluation of data loss risks, and others.
You can go with the “Download zip” files and folders option or backup scripts, however, they won’t ensure automation, proper protection against ransomware, and restore capabilities. In this case, all the responsibility over GitHub data protection is on your side.
Alternatively, you can use a dedicated backup software, like GitProtect.io for GitHub, that will help you both share your duties over GitHub data protection and ensure your data is accessible and recoverable in any disaster scenario. With scheduled automated backup procedures, full data coverage, data residency of your choice, ransomware protection, and advanced disaster recovery measures, the backup provider brings peace of mind that every line of your source code is secured.
RELATED TOPICS
- How To Safeguard Your Data With Cloud MRP System
- How to Hide Tables in SQL Server Management Studio
- How to Recover Deleted Emails from Exchange Server?
- Cloud Solutions Transform Software Quality Assurance
- How to Choose the Best Analytics Tools for Mobile Apps
- How To Craft The Perfect Data Loss Prevention Strategy
- How to Install Microsoft Exchange Updates with Reliability
- Insights on Google Cloud Backup, Disaster Recovery Service