Websites though being secured remains at a risk of getting attacked in one or the other way. Internet is coming up with a new attack almost every day, Phishing, Sniffing, Snooping, hijacking, identity hacking are to name a few.
Authentication hacking is one such type of attack. As we all know that authentication is very vital in terms of security of any kind of applications. For accessing any type of assets, one has to verify himself/herself by providing his/her usernames and passwords to get the authority to the applications or the data.
Authentication attack can be stealing of credentials (usernames and passwords) and hence accessing and stealing of important data or applications.
Normally, a HTTP transaction consists of following authentication protocols:
- Basic: – Basic access authentication uses the basic clear text username and password, base 64-encode (not that importantly decoded).
- Digest: – Digest authentication is a method in which a web server deals with user’s web browser by securing the credentials provided by the user by applying a hash function to the password before transferring it over the network.
- Form–based:- As the name itself suggests, Form based authentication uses an editable form which is to be filled up the user with his/her credentials and is processed in the back end with logical premises.
- NTLM: – NT (as in for Network) LAN (as in Large Area Network) Manager abbreviates as NTLM, is a work of Microsoft security protocols which supports authentication, integrity and confidentiality for users. It can be implemented within HTTP request/response headers.
- Negotiate: – Negotiate can be known as newer protocol from the Microsoft Family. It acknowledges the previously mentioned protocols to be dynamically accepted by the client and server. In addition, it supplies with Kerberos for clients of Microsoft Internet Explorer Version 5 and higher.
- Client–side Certificates: – With its immense fame, SSL/TLS certificates has gained a worldwide appreciation as Client side Certificates. It secures the online transaction, online communications through authentication token and cryptographic protocols.
- Microsoft Passport: – Microsoft Passport is a cookie based authentication service. It provides a single logon as well as core profile services for the member users. Passport uses a key which is shared between Microsoft and the Partner site.
All the authentication protocols work on the HTTP and/or on SSL/TLS implanting the credentials in the request/ response traffic. Authentication attack cannot be claimed as technical security fault in the Operating System or the server. It merrily relies on the security measures taken to preserve the complex passwords and severity of the attack from a hacker.
Where a vulnerable site will lead you to?
Authentication attack as mentioned above is mere a breaking in to the system by hacking the actual credential and faking to be a valid user for corrupting the system or stealing of the data.
If attacker gains the entry into the system as a user he/she may get a limited access privileges to the data while if he/she gains access as an administrator with universal privilege, you can image what damage he/she can cause to your system or business.
Tools prove to be the backbone of the hackers:
Howsoever smart the hacker must be, it is very important to fill in the exact matches of the usernames as well as the passwords. Once a hacker knows about the user with the high privilege, he/she would not be far away from guessing out the correct password. And now with available tools and techniques, it is not that difficult to guess the password for any hacker.
Below is a list of the combinations of the usernames and password guesses:
|
Usernames Guesses |
Password Guesses |
| Root, administrator, admin | , root, administrator, admin, password, |
| operator, webmaster, backup | , operator, webmaster, backup |
| guest, demo, test, trial | , guest, demo, test, trial |
| member, private | member, private |
| , , password | |
| , |
These were some of the guessable usernames and passwords. If a hacker fails in guessing the passwords then the tools like WebCracker and Brutus comes for help.
Tools like WebCracker and Brutus tries to enter in to the system with their pre installed lists of usernames and passwords, dictionary attacks and brute-force attacks.
How to determine the page’s authentication?
Authentication tester is a technique which helps you test the page’s authentication. One such authentication tester is Acunetix Web Vulnerability Scanner. It will automatically test all the pages which may require authentication.
How to prevent an authentication attack?
If you want make sure that no attack has happened, you can make use of automated tool that will display the returned error codes and page information from the host web server. Ensure the security by enforcing any error page or unexpected request to generate a HTTP 200 OK response, rather than various 400 type errors. This will confuse the attacker as to differentiate from valid and invalid attempts.
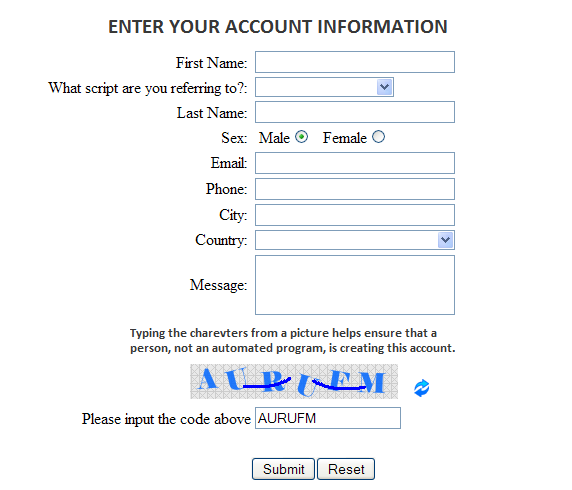
To avoid the brute force authentication attack, one can add some random content on the page displayed to the client browser. Also the client should be able to submit the random content as part of authentication process. One way to do this is to present the random content in a graphic GIF, JPG or PNG format using colors and fonts randomly each time.
For example:
Using Web tools like Acunetix Vulnerability scanners will help preserve your data as it checks for the SQL injections and Cross site scripting at the same time.
Scan your website with GeoTrust Web Site Anti-Malware Scan, It helps find malware (if any) and also demolish it. Web Site Anti-Malware Scan monitors the website to help clean up the infected website. It supplies with on-demand scan and instant alerts.
All you need to do is to remain a little bit aware and to use the best security practices.