Recently, Yigal Unna, Director General of the Israel National Cyber Directorate (INCD) claimed that they saw zero successful cyber-attacks against Israeli “critical national infrastructure” in 2019. Such a statement would no doubt incite great patriotism in the unacquainted Israelite but is far from true.
We can say so through a couple of facts. Firstly, it is a widely accepted notion in the cybersecurity industry that anything can be hacked no matter who’s behind it. Secondly, Eitan Caspi, a security researcher exposed certain vulnerabilities found in Israeli government websites last week.
He did so through an online SSL checker tool by Qualys which basically lets you know how well configured an SSL certificate is and whether it is implemented correctly. This is very important as the mere presence of a certificate does not make the site secure, other crucial parameters are also involved which includes protocol support, key exchange, and cipher strength.
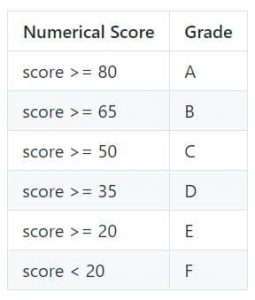
The tool assesses these to calculate a numerical score which then is translated to a grade.
Therefore, out of the 17/21 domains analyzed successfully:
- 5 of them were found to have an F grade in SSL tests performed with the reason being that the site’s domain name was not found in the site’s certificate in the first place,
- 5 were found with certificates that are not trusted and hence granted a T grade,
- 6 were given a B grade,
- Only 1 was given an A grade.
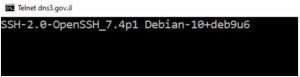
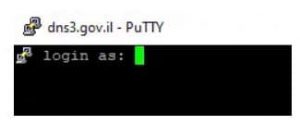
According to Eitan’s blog post, the rest of the 4 domains were not assessed due to a server connection error. These give us a good picture of the sad state of affairs of the security of the websites. However, deeper issues were found. On one of the servers at dns3.gov.il with IP address 62.219.20.20, a reply was received on port 22 which is used to manage UNIX servers.
This allowed him to try to log in.
On Friday at 31 January at 4:28 PM, he reported this to the Israeli National Computer Response Emergency Team (CERT) along with alerting a couple of senior people in the government’s information security department. About 5 hours later at 9:30 PM, upon rechecking, it was found that the port was closed – the issue fixed. A fast response indeed.
I have much criticism about the Israeli government’s information security status and activity. Lots of PR and marketing for being a “Cyber Nation” but it is true mostly for the selling of knowledge, services, and products. Not so much doing the “dirty work” of protecting the Israeli Internet-facing IT, including the one of the Israel government itself, Eitan’s wrote in their blog post.
The second main issue was that the SSH server being used was found to be 7.4p1 which was released in December 2016. This means that since then, it has not been updated to bring in crucial security fixes and regular updates to the current version 7.9, something even an Android user cannot afford for his smartphone(new trojan gifts every day), let alone a government.
In light of all of this, it is vitally important that not only this particular government but others globally also take necessary precautions to upgrade their security. Not only the opposite can result in commonly found embarrassment for them but also hurt its interests.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.