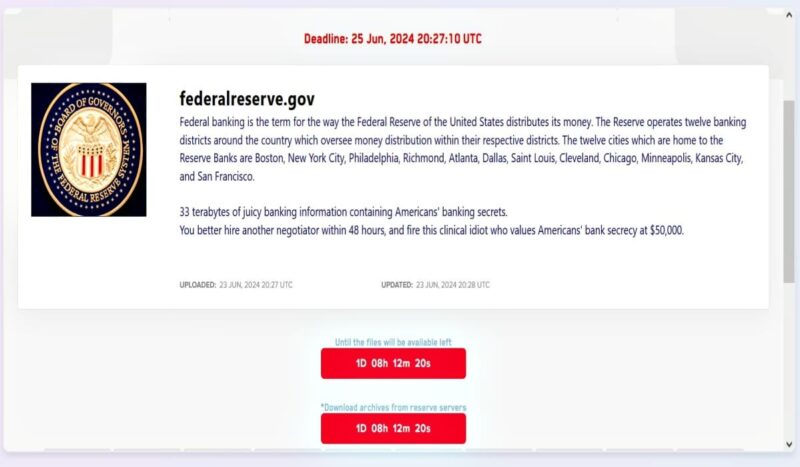
The notorious LockBit ransomware gang claims to have breached the Federal Reserve Board (Federalreserve.gov), the central banking system of the United States, and is holding 33 terabytes of data for ransom.
Although these claims sound far-fetched, the ransomware gang has warned the US government of a June 25, 2024, deadline, after which the allegedly stolen data could be leaked to the public.
At the time of writing, the type of data extracted by LockBit is unclear. However, as seen by Hackread.com, a statement from the cybercrime enterprise on its new dark web leak site hints at “33 terabytes of juicy banking information” containing “American banking secrets.” Another statement by the ransomware group suggested that there are ongoing negotiations between them and the US government.
“33 terabytes of juicy banking information containing Americans’ banking secrets. You better hire another negotiator within 48 hours, and fire this clinical idiot who values Americans’ bank secrecy at $50,000.”
LockBit Ransowmare
The statement from LockBit appears to be a taunt directed at the US Federal Reserve, suggesting dissatisfaction with the current negotiator, if any, handling the ransom negotiations.
LockBit Claims and Realities
LockBit is notorious for its high-profile data breaches, including incidents involving Boeing, ICBC Bank, Bangkok Airways, and others. A recent report from the NCC Group revealed that LockBit is the most active ransomware gang, even after its infrastructure was seized and its alleged leader was exposed as Dmitry Yuryevich Khoroshev by law enforcement authorities.
Despite this, the group is known for claiming high-profile targets, which are often dismissed by the companies involved. For instance, in April 2023, the group announced it had breached Darktrace, a prominent Cambridge-based cybersecurity company. These claims were swiftly dismissed by the company.
In June 2022, the group claimed to have breached Google-owned Mandiant cybersecurity. However, the company did not find any evidence of a data breach.
Nevertheless, the current situation is that the group has claimed Federalreserve.gov as its new victim. Hackread.com is monitoring the situation and has reached out to the US Cybersecurity and Infrastructure Security Agency (CISA) for comment. Stay tuned!