- Background Task Weaknesses: macOS Ventura’s Background Task Management has vulnerabilities that allow hackers to evade detection and install malware.
- Researcher’s Revelation: Patrick Wardle, a respected Mac security researcher, unveiled these vulnerabilities at the Defcon hacker conference.
- Monitoring Tool’s Purpose: Background Task Management is intended to detect and alert users to software persistence, ensuring data retention after restarts.
- Sophisticated Exploitation: Despite alerts and notifications, Wardle’s research shows that advanced malware can bypass the monitoring system, even without root access.
- Apple’s Response Awaited: Apple has yet to respond to these findings, raising concerns about the efficacy of macOS Ventura’s security enhancements.
Renowned Mac security researcher Patrick Wardle recently unveiled potential weaknesses within Apple’s macOS Ventura, shedding light on vulnerabilities in the Background Task Management mechanism. This revelation calls into question the efficacy of Apple’s latest monitoring tool designed to detect and mitigate malware.
During his presentation at the Defcon hacker conference held in Las Vegas, Wardle shared insights into how malicious actors can exploit macOS Ventura’s Background Task Management to bypass monitoring and potentially compromise user devices.
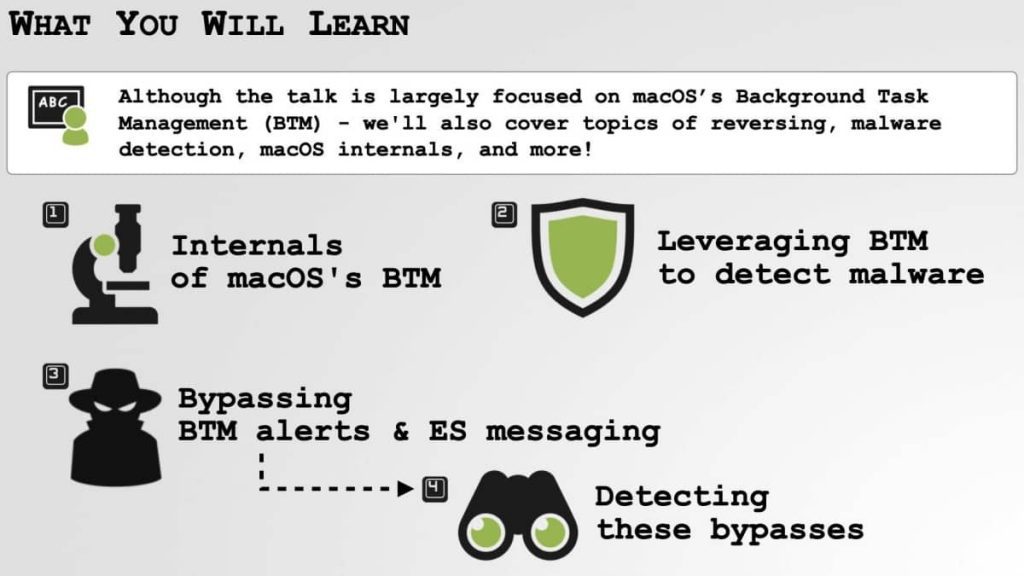
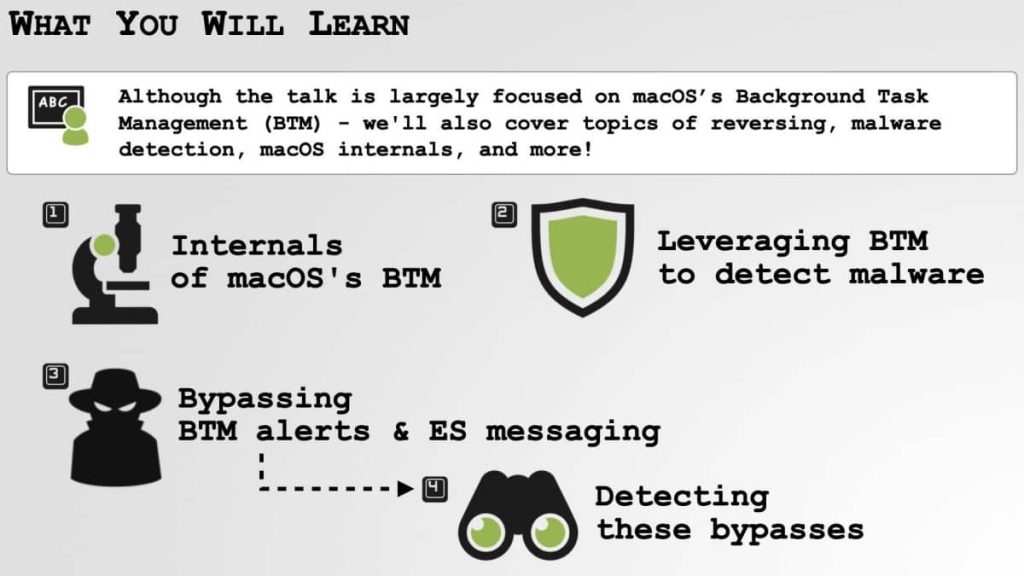
The Background Task Management tool, introduced with macOS Ventura, aims to detect instances of software “persistence,” which is when malicious software establishes itself on a device and remains active even after restarts. Such persistence is crucial for legitimate applications, ensuring users’ apps, data, and preferences are retained across device reboots.
However, Wardle’s findings suggest that the implementation of this monitoring tool is not foolproof. Apple added Background Task Management to send notifications to users and third-party security tools if a “persistence event” occurs, alerting users to unexpected or potentially malicious persistence. Despite this enhancement, Wardle’s research demonstrates that sophisticated malware can easily evade the monitoring mechanism.
Wardle’s research focused on pinpointing vulnerabilities within the Background Task Management’s structure. He highlighted that some bypass techniques require root access, effectively granting attackers full control over a compromised device, allowing them to manipulate persistence notifications and install malware without user awareness.
More concerning are two other bypass methods that don’t necessitate root access, exploiting flaws in how the alerting system communicates with the operating system’s core (the kernel) and leveraging the capability to put processes to sleep.
The security researcher’s findings reflect broader concerns about the efficacy of macOS Ventura’s security enhancements. Wardle emphasized that the rushed implementation of monitoring tools can give users a false sense of security, potentially overlooking critical security risks.
Apple has not yet responded to requests for comment regarding Wardle’s findings. Despite the vulnerabilities exposed, Wardle remains hopeful that these revelations will encourage Apple to refine its security measures further, ensuring a safer environment for Mac users.
MORE FINDINGS FROM PATRICK WARDLE
- Hackers Targeting Apple’s M1 Chip with Mac Malware
- Apple approved malware camouflaged as Adobe Flash Player
- How easily macOS user warnings can be bypassed by malware
- LockBit Ransomware Expands Attack Spectrum to Mac Devices
- Cryptocurrency users on Discord & Slack hit by MacOS malware
- Researcher creates app to notify users of evil maid attack on MacBook