Summary:
- Malware exploits a legitimate Avast Anti-Rootkit driver to gain kernel-level access.
- Driver is used to terminate critical security processes and seize control of the system.
- BYOVD (Bring Your Own Vulnerable Driver) protection mechanisms can prevent driver-based attacks.
- Expert rules can be deployed to identify and block vulnerable drivers.
Cybersecurity researchers at Trellix have identified a malicious campaign that exploits a legitimate Avast Anti-Rootkit driver, aswArPot.sys, to disable security software and take control of infected systems.
How the Attack Works:
The malware, dubbed “kill-floor.exe,” begins by dropping the aswArPot.sys driver into an apparently harmless Windows directory, disguising it as “ntfs.bin.” It then registers the driver as a service, granting the malware kernel-level access – the highest level of system privilege allowing it to terminate critical security processes and take control of the system.
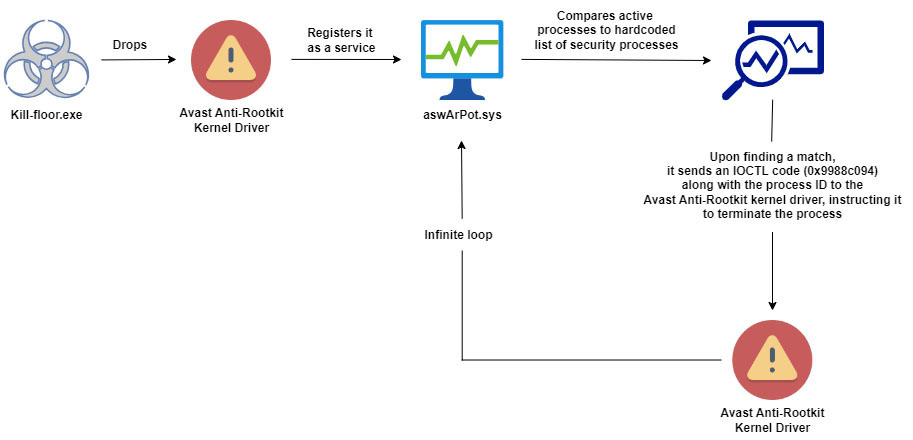
The malware contains a hardcoded list of 142 security applications it targets for termination. The malware continuously monitors active processes and compares them against this list. When a match is found, the malware uses the Avast Anti-Rootkit driver to terminate the security process.
Simply put: The Avast driver, meant to remove malicious rootkits, unintentionally disables legitimate security software. Malware takes advantage of this trusted driver to avoid detection and work quietly within the system.
Technical Look
Trellix’s technical analysis of the Avast driver revealed the specific function, “FUN_14001dc80,” responsible for terminating the security processes. This function utilizes standard Windows kernel functions (KeAttachProcess and ZwTerminateProcess) to carry out the termination, further masking the malicious activity as normal system operations.
Protecting Yourself
To prevent such driver-based attacks, Trellix recommends the use of BYOVD (Bring Your Own Vulnerable Driver) protection mechanisms. These mechanisms can identify and block specific vulnerable drivers based on their unique signatures or hashes.
Once these rules are integrated into your antivirus solution, organizations can prevent malware from exploiting legitimate drivers, elevate privileges, or disable security measures. Trellix has also provided a specific BYOVD expert rule to detect and block the malicious use of the aswArPot.sys driver.









