A year-long malware campaign targets Roblox developers using fake NPM packages mimicking “noblox.js” to steal data. Despite takedowns, new threats continue to emerge.
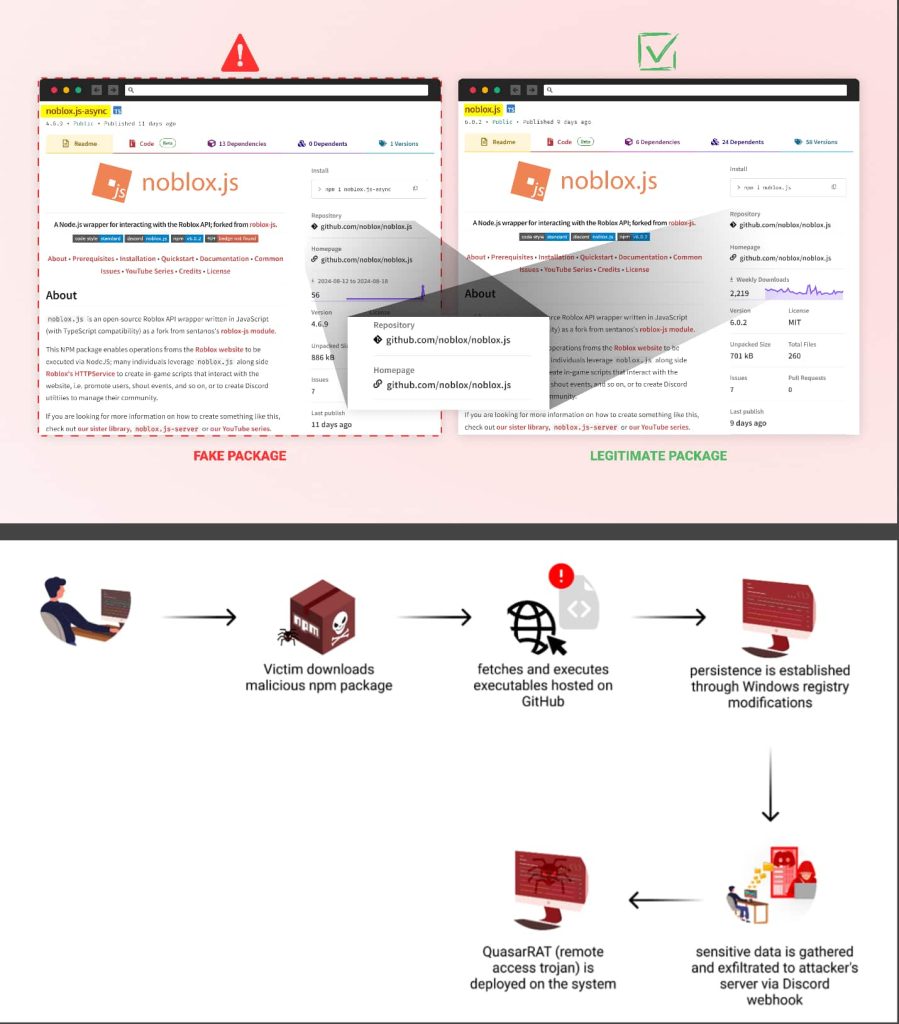
A persistent malware campaign has been targeting Roblox developers through malicious NPM packages for over a year, according to a recent report from Checkmarx. The attackers have published dozens of packages mimicking the popular “noblox.js” library, with the aim of stealing sensitive data and compromising systems.
The campaign, which began in August 2023, has continued despite multiple package takedowns, with new malicious packages still appearing on the NPM registry at the time of publication. The attackers have used techniques such as brandjacking, combosquatting, and starjacking to create a convincing appearance of legitimacy for their malicious packages.
The malware’s capabilities include Discord token theft, system information harvesting, system persistence, and the deployment of additional payloads such as Quasar RAT. The malware also employs a sophisticated persistence technique by manipulating the Windows registry, causing it to execute every time a user opens the Windows Settings app.
Despite the removal of the identified malicious packages from NPM, the attacker’s GitHub repository containing malicious executables remains active, paving the way for future attacks.
The attackers have used a sophisticated approach to craft an illusion of authenticity around their malicious packages. They have combined brandjacking and combosquatting, two methods that fall under the broader category of typosquatting, to create the illusion that their packages are either extensions of or closely related to the legitimate “noblox.js” library.
The attackers have also used starjacking, a popular method used to fake package stats. In this instance, the malicious packages were linked to the GitHub repository URL of the genuine “noblox.js” package, falsely inflating their perceived popularity and trustworthiness.
According to Checkmarx’s report, the malware also employs tactics to disguise itself within the package itself. The attackers have meticulously mimicked the structure of the legitimate “noblox.js” but introduced their malicious code in the “postinstall.js” file. They have heavily obfuscated this code, even including nonsensical Chinese characters to deter easy analysis.
The malicious code exploits NPM’s postinstall hook, ensuring automatic execution when the package is installed. This hook is designed for legitimate setup processes but becomes a gateway for running the obfuscated malware without the user’s knowledge or consent.
The malware searches for Discord authentication tokens in multiple locations and validates them to ensure only active ones are exfiltrated. It also aggressively undermines the system’s security measures, targeting Malwarebytes and Windows Defender.
The malware expands its capabilities by downloading two additional executables from the attacker’s GitHub repository. These files are then saved to the “C:\WindowsApi” directory with randomized names, likely to help the malicious files blend in with legitimate system files.
To ensure long-term access, the malware manipulates a Windows registry key to ensure it runs consistently on the infected system. It also collects various types of sensitive information from the infected system and sends it to the attacker’s command and control server using a Discord webhook.
The final stage involves deploying QuasarRAT, a remote access tool that gives the attacker extensive control over the infected system. The attacker maintains a second repository named “noblox-spoof”, which appears to house the latest malicious npm package content, directly referencing the target of this campaign.
The most recent malicious packages impersonating the popular noblox.js library have been taken down after being reported to npm’s security team. However, the threat is not entirely neutralized, and the attacker’s continued infrastructure presence and persistence pose an ongoing threat.
Developers are strongly advised to remain vigilant, verifying the authenticity of packages, especially those resembling popular libraries like noblox.js, to protect themselves and their users from such sophisticated supply chain attacks.