Russian GRU-linked hackers exploit known software flaws to breach critical networks worldwide, targeting the United States and the United Kingdom, and key sectors since 2021.
A hacking group with links to Russian intelligence has been silently compromising computer networks worldwide, including those in the United States and the United Kingdom, by taking advantage of known security vulnerabilities in widely used software.
This was revealed by Microsoft’s Threat Intelligence team on Wednesday, which has been tracking the activities of a subgroup within “Sandworm,” (aka Seashell Blizzard, UAC-0133, Blue Echidna, Sandworm, PHANTOM, BlackEnergy Lite, and APT44.), a hacking group tied to Russia’s GRU military intelligence unit. This subgroup, which Microsoft calls the “BadPilot campaign,” has been breaching networks since at least 2021 by exploiting vulnerabilities in internet-facing systems.
The hackers have been targeting a variety of sectors including energy, oil and gas, telecommunications, shipping, arms manufacturing, and even government organizations. Initially, their focus was on Ukraine, Europe, and parts of Asia and the Middle East. However, since early 2024, they have expanded their operations to include the U.S. and the U.K.
Their methods involve exploiting publicly known vulnerabilities in software like ConnectWise ScreenConnect, used for remote IT management, and Fortinet FortiClient EMS, a security software. By gaining an initial foothold through these weaknesses, the hackers can then move deeper into the network, steal credentials, and ultimately gain control of valuable systems. Here are the security vulnerabilities that Microsoft found being exploited by the group:
- OpenFire (CVE-2023-32315)
- JBOSS (exact CVE is unknown)
- Microsoft Outlook (CVE-2023-23397)
- Microsoft Exchange (CVE-2021-34473)
- Zimbra Collaboration (CVE-2022-41352)
- JetBrains TeamCity (CVE-2023-42793)
- Fortinet FortiClient EMS (CVE-2023-48788)
- Connectwise ScreenConnect (CVE-2024-1709)
Microsoft believes that while some of the targets seem random, these widespread breaches give Russia options to respond to changing strategic goals. Since the start of the war in Ukraine, Russian-aligned hackers have been increasingly targeting international organizations that provide support to Ukraine or are of geopolitical importance. The subgroup is also thought to be connected to destructive cyberattacks in Ukraine since 2023.
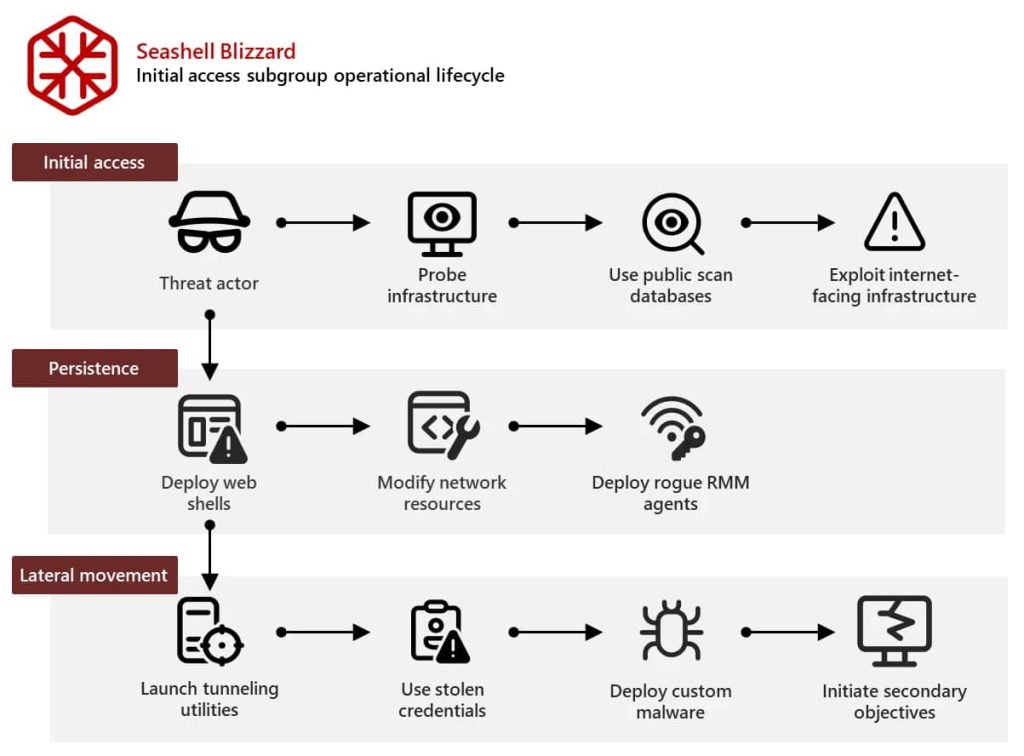
Microsoft’s research reveals that this subgroup is not just about gaining access; it’s about maintaining it. Once inside a network, they deploy tools such as remote management software (RMM) and web shells to ensure long-term control.
For instance, by installing legitimate RMM agents like Atera Agent and Splashtop Remote Services, they can mimic authorized activity, making detection more challenging. The group is also known for web shell deployment, credential harvesting and DNS manipulation
Additionally, the use of custom utilities like ShadowLink, a tool that configures compromised systems as hidden services on the Tor network, further complicates efforts to trace their activities.
Who Is Sandworm?
Linked to Russia’s military intelligence agency GRU, specifically Unit 74455, Sandworm is notorious for conducting disruptive cyberattacks. Their history includes incidents like the NotPetya attack in 2017, which caused billions in damages worldwide, and the FoxBlade operation in 2022, targeting Ukraine’s infrastructure.
Industry experts are raising alarms about the implications of these findings. “This discovery is alarming for UK organisations as it highlights how Russian state-sponsored actors are exploiting CVEs to infiltrate networks, conduct surveillance and launch attacks,” warns Simon Phillips, CTO of SecureAck.
Even though the subgroup exploits publicly known vulnerabilities, their post-compromise tactics are becoming more advanced. The emergence of BadPilot only makes it harder to detect the activities of these already well-equipped and highly skilled Russian hackers.
That’s why organizations of all sizes must stay alert and aware of this and other cybersecurity threats. Employee training and additional security measures can help prevent breaches, even if they can’t completely stop Seashell Blizzard.