A vulnerability in Microsoft Bookings can expose your organization to serious security risks. Learn how attackers can exploit this flaw to create convincing impersonations, launch phishing attacks, and compromise sensitive data.
Information security-oriented firm Cyberis has discovered a new vulnerability in Microsoft Bookings which allows attackers to create highly convincing impersonations of key personnel within an organization, purchase TLS certificates or transfer domain names/services relying on email verification such as Cloudflare, and hijack accounts.
For your information, Microsoft Bookings is a tool used for scheduling appointments. The issue lies in an otherwise harmless feature: Shared Booking Pages. By default, users with appropriate Microsoft 365 licenses can create these pages. When a user creates a Shared Booking Page, it automatically generates a corresponding account within Entra, which is Microsoft’s identity and access management platform.
According to a blog post published by Cyberis’ director Geoff Jones, the issue lies in account creation is problematic due to several factors. Firstly, the default setting allows any user with an appropriate Microsoft 365 license to create Shared Booking Pages, bypassing standard security protocols, where administrators typically have the sole authority to create new accounts.
Secondly, the system automatically generates email addresses based on the Booking Page name, often following a predictable format (e.g., “FirstnameLastname” becomes “FirstnameLastname@”). Attackers can exploit this predictability to create email addresses resembling legitimate users, enabling phishing and identity theft.
These accounts also have full email functionality, allowing them to send and receive emails both internally and externally, leading to malware distribution, phishing attacks, and compromising of sensitive information.
Jones further explains that these accounts are not readily visible in standard administrative tools like the Exchange Admin Center, which makes it difficult for administrators to detect and manage them. This hidden feature expands the organization’s attack surface, making it more vulnerable to account hijacking.
Account hijacking can involve reusing former employee email addresses, creating Booking Pages with matching email addresses, resetting passwords for external services, or verifying domain ownership for SSL certificates.
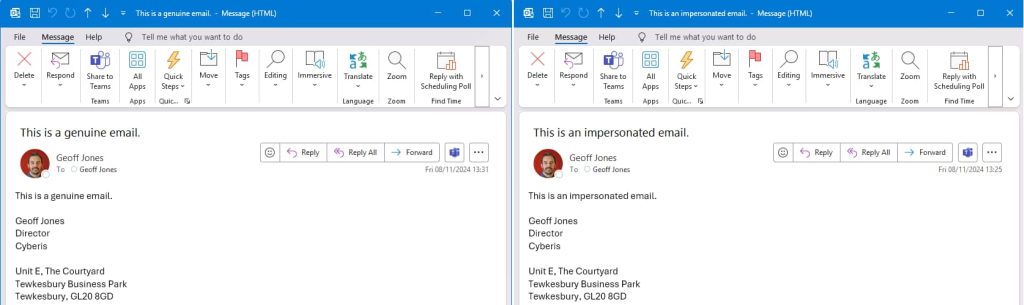
As per Jones, attackers can exploit Bookings in Microsoft 365 to impersonate someone with higher authority by creating a shared booking page mimicking a high-profile target, such as the CEO, and generate a convincing email address. For instance, geoff.jones@cyberis.com becomes geoffjones@cyberis.com.
Additionally, they can create legitimate-looking emails, add a profile picture or signature identical to the target, and launch highly believable phishing attacks against other employees. They can bypass detection mechanisms and target individuals with more access to sensitive information within the organization.
The vulnerability extends beyond impersonating existing employees. Attackers can create Booking pages with email addresses matching those of former employees, potentially reset passwords and gain access to external services linked to the email address, and verify domain ownership by obtaining SSL certificates through email validation mechanisms.
To mitigate the risk of attackers exploiting Microsoft Booking’s vulnerabilities, organizations should identify hidden mailboxes, restrict booking access, monitor incoming accounts, review permissions, and secure high-value email addresses. These steps, combined with a proactive approach to security configuration, can reduce the risk of attackers exploiting Microsoft Booking’s vulnerabilities.
RELATED TOPICS
- Hackers Could Exploit Microsoft Teams on macOS to Steal Data
- Hacker Leaks Thousands of Microsoft and Nokia Employee Details
- Russian Midnight Blizzard Breached UK Home Office via Microsoft
- NAKIVO Backup Solution for MSPs: Data Protection for Microsoft 365
- ZDI Slams Microsoft for Not Crediting It in Last Week’s Patch Tuesday