Cybersecurity experts uncover the Lummac Stealer malware, disguised as an OnlyFans “Checker” tool, targeting hackers. The tool also targets Disney+ and Instagram hackers.
Cybersecurity experts at Veriti’s cyber research team have discovered a Lummac Stealer, also known as LummaC2 Stealer operation that cleverly flips the script on would-be OnlyFans hackers, turning them from hunters into the hunted.
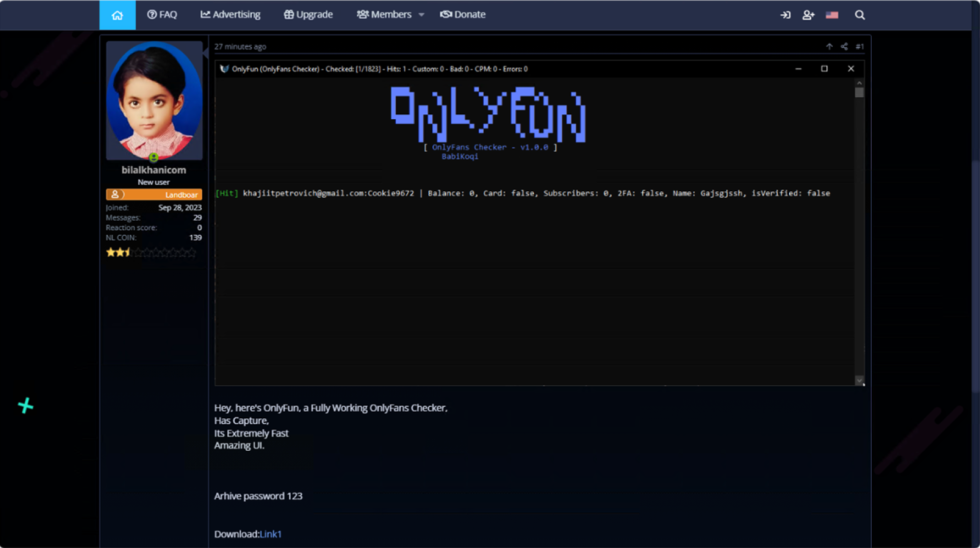
The operation centers around a user, going by the name “Bilalkhanicom“ on a notorious hacking forum, who offered a “Checker” tool claiming that it would allow users to supposedly “check” OnlyFans accounts for valuable information. However, this “checker” turned out to be malware, specifically a strain known as Lummac stealer.
As a result, instead of gaining access to Only Fan account information or illicit content, those who downloaded the tool were infected with Lummac Stealer. For your information, the malware can steal passwords and financial information to browsing history and cryptocurrency wallets.
In January 2024, Lumma was discovered to be spreading through cracked software distributed via compromised YouTube channels. Earlier, in November 2023, researchers had identified a new version of LummaC2, called LummaC2 v4.0, which was stealing user data using trigonometric techniques to detect human users.
According to Veriti’s research shared with Hackread.com ahead of publication on Wednesday, Bilalkhanicom is also using similar tactics to target those interested in hacking other platforms, including Disney+, Instagram, and even botnet networks.
The malicious installers are uniquely named to align with the interests of hackers based on the services they aim to exploit. For example, to target Disney+ users, Bilalkhanicom offers a checker tool called “DisneyChecker.exe.”
Similarly, for Instagram, the tool is named “InstaCheck.exe,” and for botnet enthusiasts, it is labelled “ccMirai.exe,” referencing the notorious Mirai malware botnet, infamous for orchestrating large-scale, crippling DDoS attacks worldwide.
As for Bilalkhanicom, their origin at this time remains unknown however researchers have identified folder names within the malware’s architecture that hint at influences from across the globe, from East Asia, Africa to Latin America, and even Celtic mythology.
“Our researchers uncovered a potential geopolitical link hidden in the malware’s architecture. The folder names used in the malware’s file structure paint a picture of global influences: “Hiyang” and “Reyung” whisper of East Asian connections “Zuka” echoes African influences “Lir” invokes Celtic mythology “Popisaya” hints at Indigenous Latin American roots.”
Veriti Research
I hereby confirm. https://t.co/1q4cARQLDM pic.twitter.com/GEBzqJeaSs
— Waqas (@WAK4S) December 31, 2023
NOT the first time
This is not the first time OnlyFans has been used as bait. In June 2023, a malicious campaign targeting smartphone users employed fake OnlyFans content to distribute DcRAT malware. The attackers lured victims by exploiting their interest in adult-oriented material, specifically targeting those who engaged with explicit OnlyFans content.