RansomHub ransomware group leaks alleged 487 GB of sensitive data stolen from Kawasaki Motors Europe (KME), following a cyberattack. The breach includes business documents and financial data, raising cybersecurity concerns for global firms.
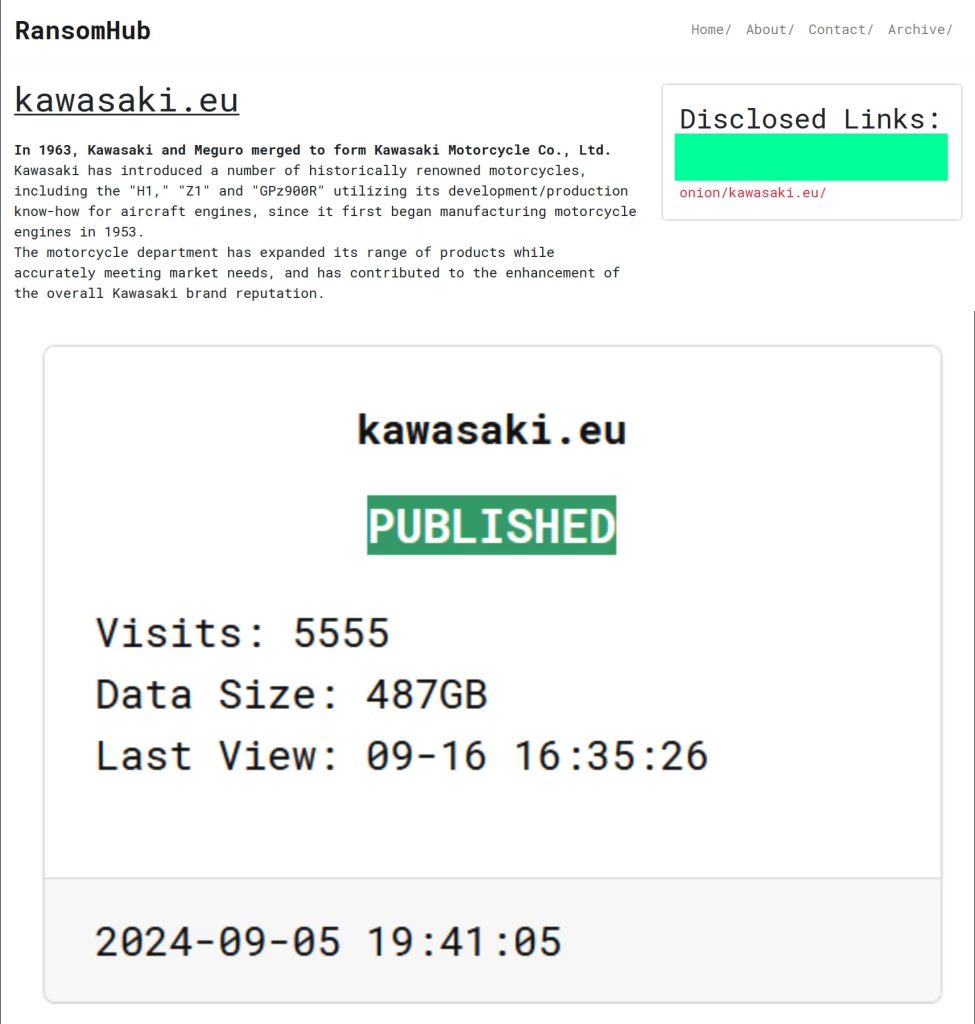
The notorious RansomHub ransomware group has leaked 487 gigabytes of data it allegedly stole from Kawasaki Motors Europe (KME). This cyberattack was publicly disclosed by Kawasaki last week, though the company emphasized that the attack had not been successful in its aims.
As a preventive measure, Kawasaki temporarily isolated its servers and initiated a thorough “cleansing process” to detect any potential infections. However, despite Kawasaki’s recovery efforts, RansomHub went ahead with the data release. On September 5, 2024, the group listed the stolen information on the dark web, utilizing its official dark web leak sites to dump the data.
As seen by the Hackread.com research team, among the exposed files are critical business documents, including financial information, banking records, dealership details, and internal communications.
A partial list of the leaked data includes directories titled “Dealer Lists,” “Financing Kawasaki,” “COVID,” “Trading Terms,” and more, with timestamps showing activity as recent as early September.
Kawasaki’s Response and Cybersecurity Strategy
While Kawasaki Motors Europe disclosed the breach to its customers, it appears that the company opted not to engage with the ransom demands. Jason Soroko, Senior Fellow at Sectigo, speculated that Kawasaki may have prioritized system restoration over paying the ransom.
He suggested that this decision reflects Kawasaki’s readiness to deal with the potential fallout of a data breach, emphasizing the importance of having strong cybersecurity systems in place to avoid financial damage through ransom payments.
“Kawasaki Motors Europe’s official statement claimed they could take the hit with the data versus the financial hit of paying the ransom, however, the RansomHub group released 487 GB of allegedly stolen data. This suggests, but does not prove, Kawasaki chose not to negotiate with the attackers, prioritizing system restoration and data cleansing.“
Soroko added that Kawasaki’s stance might serve as a model for other companies: instead of negotiating with cybercriminals, businesses should focus on recovery and work to fortify their systems against future attacks.
He also pointed out the need for organizations, especially in the United States, to enhance their cybersecurity infrastructure, prepare for such incidents, and collaborate with government authorities to better handle ransomware threats.
“Given RansomHub’s increased activity, US companies should bolster cybersecurity measures, prepare robust incident response plans, and avoid paying ransoms, aligning with government advisories. Staying informed about such threats and collaborating with authorities can mitigate risks and protect sensitive data,“ he explained.
The Role of RansomHub
RansomHub is a notorious player in cybercrime especially ransomware attacks, having made headlines recently for its involvement in other major breaches. Earlier this month, the group claimed responsibility for hacking Planned Parenthood and stealing 93 gigabytes of sensitive data.
This trend of increased activity exposes the growing threat posed by ransomware groups, which often target high-profile organizations in sectors ranging from healthcare to manufacturing.
RELATED TOPICS
- PythonAnywhere Cloud Platform Abused for Hosting Ransomware
- Qilin Ransomware Upgrade: Now Steals Google Chrome Credentials
- Russian Hackers Hit Mail Servers in Europe for Political, Military Intel
- Xplain Hack: Play Ransomware Leaks Sensitive Swiss Government Data
- Hackers hit Europe’s largest healthcare provider with Snake ransomware









