REvil hackers are now demanding $7.5 million ransom from the targeted food distributors.
Last week, the US president Trump was hit with alarming claims of his data being in the hands of the cybercriminals group and operator of REvil ransomware. Targeting a US-based law firm named Grubman Shire Meiselas & Sacks (GSM); the attackers threatened to leak it unless they were paid $42 million.
However, just recently in a classic U-turn, they have stated that the data has been sold to a buyer on the dark web and due to their policy of only letting the buyer retain a copy, they will not be leaking it.
Many believe that they never had any harmful data on Trump in the first place.
https://twitter.com/underthebreach/status/1262482026567012354
However, this marks their shift to now auctioning data belonging to Madonna instead as revealed in their blog post. This time, the auction starts from $1 million governed by the same guidelines used before as shown in the photo album later in the article.
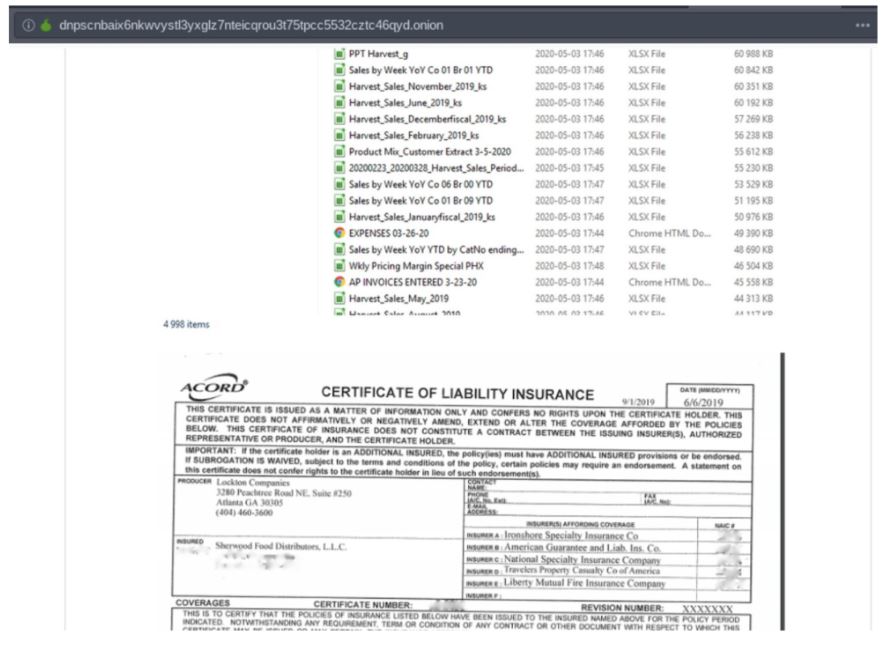
Yet, this is not all. Just about a couple of days ago, as reported by DarkOwl, we saw another announcement on the “Happy Blog” revealing that in their latest attack, the hackers have targeted two large food distributors, namely Harvest Food Distributors and its parent company, Sherwood Food Distributors.
Both of these have various supermarket chains as their clients including but not limited to three large ones, namely Kroger, Albertsons, and Sprouts. Hence, at stake is not only the data of the food distributors themselves but also their client chains.
For this, the attackers have demanded a sum of $7.5 million, lesser than their most recent heist on Grubman but a substantial sum nonetheless.
The data exposed is believed to include 2300 files composed of the following:
- Cash flow analysis details
- Sub-distributor information
- Detailed insurance information
- Scanned images of the drivers’ licenses they use as a part of their logistical network.
On the other hand, through the above notice, we also came to know that Sherwood hired a ransomware mitigation company named Coveware, the same one that was also used by Grubman. The attackers termed the actions of this firm as “unprofessional” and even went on to publish screenshots of their conversations:
Concluding, as seen, Sherwood seems willing to pay but we don’t really know at the moment what the final outcome will be owing to the displeasure of the attackers over negotiations.
For firms wanting to keep their cybersecurity strong, it is highly recommended that they take an approach of asking themselves that “when” a specific attack will happen rather than “if” it will happen. This involves hiring an external cyber security firm that can independently evaluate one’s security systems and hence serve as a constant check.
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.