The vulnerability in Shazam was identified in 2019 but the details of it were only revealed last week.
Can’t find out what’s the name of that song on television? You know who’ll help – Shazam. Recently though, a vulnerability found in the popular app which could allow a malicious actor to know a victim’s location has come to light.
The vulnerability affected more than 100 million users at the time having the potential to compromise the physical security of these users marking its severity.
Termed as CVE-2019-8791 and CVE-2019-8792; the vulnerability was discovered by a British IT security researcher Ashley King. It is noteworthy that the issue was also found back in 2018 whereafter it was reported in December the same year to the company.
However, due to Shazam having been acquired then by Apple, Ashley was asked to take up the issue with Apple which led the flaw to be finally patched on March 26, 2019, both on iOS and Android without any reward being handed out to him.
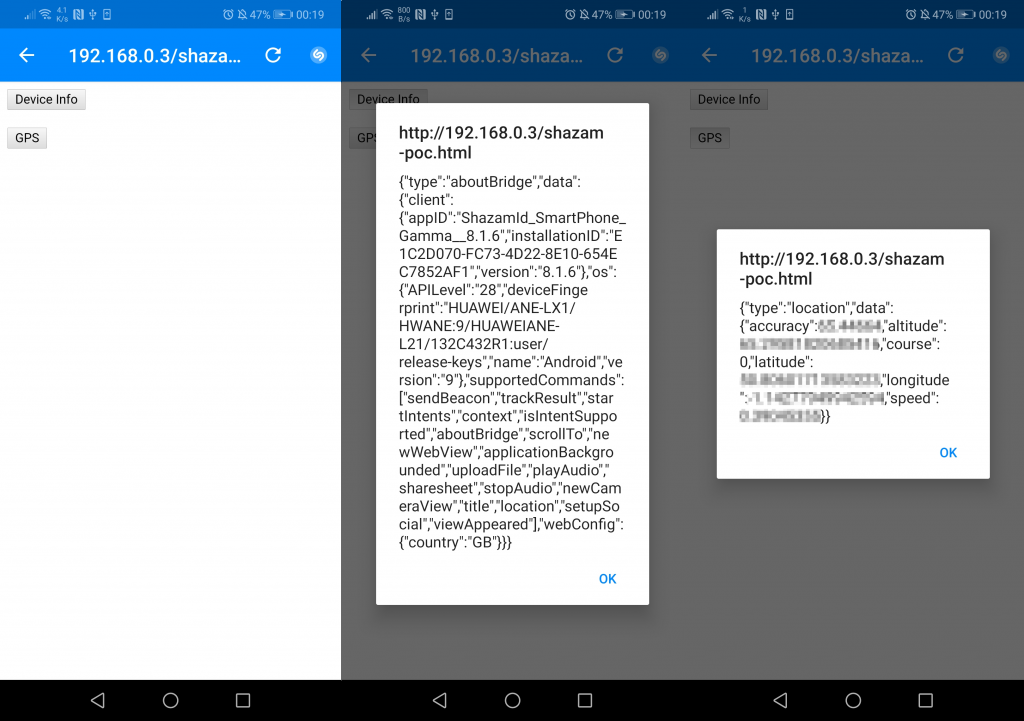
Talking about the vulnerability, how it worked was that an attacker could send a malicious link to their intended victim. If the victim opened it, this would automatically open the Shazam app and execute the malware resulting in the victim’s location data being sent to the attacker.
See: Hundreds of Android Gaming Apps are Tracking Your TV Viewing Habits
Explaining the technicality behind which type of link could be used, the researcher states in a blog post that:
Shazam uses deeplinks throughout the app as part of its navigation. I found that a particular exported deeplink (which was responsible for loading a website inside an webview) was not validating its parameter, allowing external resources to be in control.
This webview included a few javascript interfaces that allowed content to communicate with the Android & iOS API’s making it possible to pull back device specific information and the last known precise location of the user.
To conclude, according to Ashley, both Google Play Security Rewards Program and Apple itself did not see the vulnerability as being severe enough at the time even though it was patched.
See: Google collects Android location data even if location service is off
This just shows us the difference in priorities that may lie between the cybersecurity community and the people on the other side of the fence marking a division. In the future, we may see it continue knowing how corporate view user privacy.
Did you enjoy reading this article? Don’t forget to like our page on Facebook and follow us on Twitter!