Threat analysts have identified a new and emerging threat: a variant of the SystemBC RAT (Remote Access Trojan) that is now actively targeting Linux-based platforms. This development puts corporate networks, cloud infrastructures, and IoT devices at risk.
The latest version of SystemBC RAT is more stealthy and harder to detect, using encrypted communication to stay hidden while letting attackers move freely through compromised systems.
SystemBC RAT: From Windows to Linux
SystemBC is a Remote Access Trojan (RAT) commonly used in cyberattacks to provide attackers with remote control over infected systems.
Initially a Windows-only threat, it has now expanded to Linux, making it even more dangerous as Linux-based servers are widely used in enterprise environments.
What Makes the Linux Version of SystemBC RAT Dangerous?
Let’s look at how this malware operates and why it poses a serious threat to Linux-based systems.
Encrypted Communication with C2 Servers
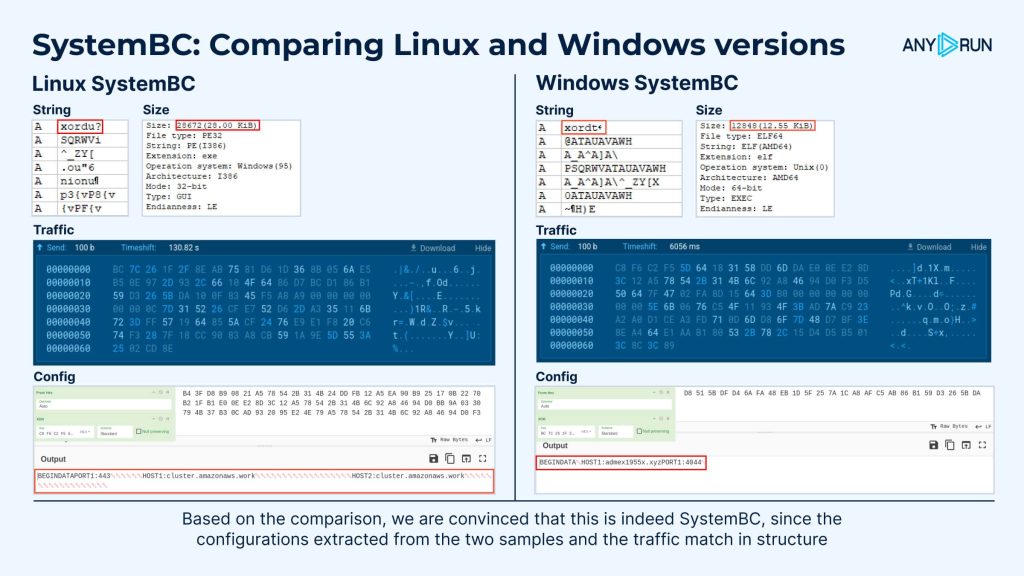
The SystemBC RAT for Linux maintains encrypted communication with C2 servers using the same custom protocols as its Windows counterpart.
This allows attackers to keep a stable connection across a unified infrastructure of both Windows and Linux implants, making it easier to control infected machines without raising suspicion.
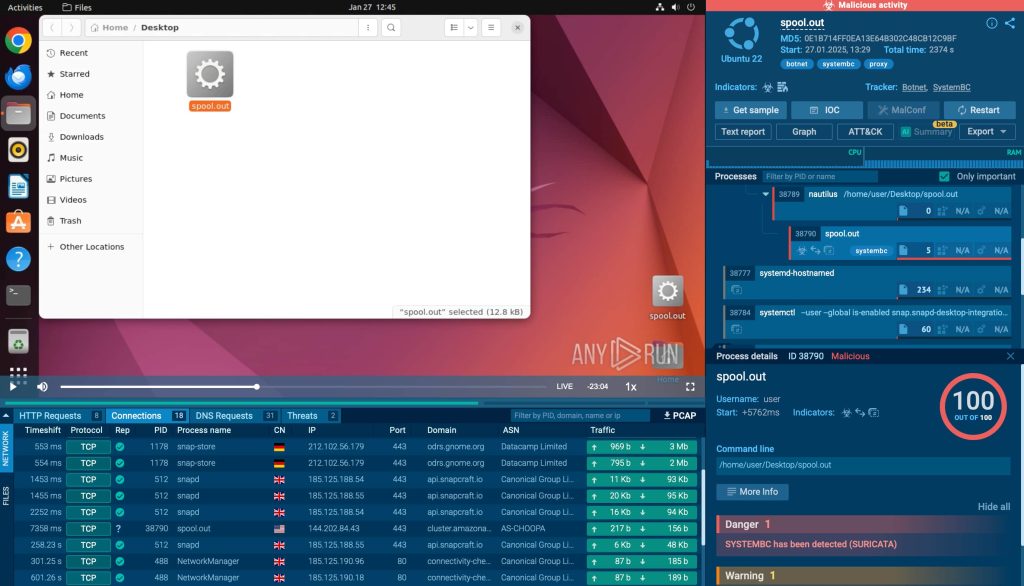
While SystemBC RAT is designed to keep its C2 communication encrypted and hidden, it becomes fully visible inside an ANY.RUN analysis session. By running a real sample in the sandbox, security teams can see the malware’s network connections, file modifications, and process activities in real time.
Below the Linux Virtual Machine window, all network connections and system modifications related to this specific attack are clearly displayed.
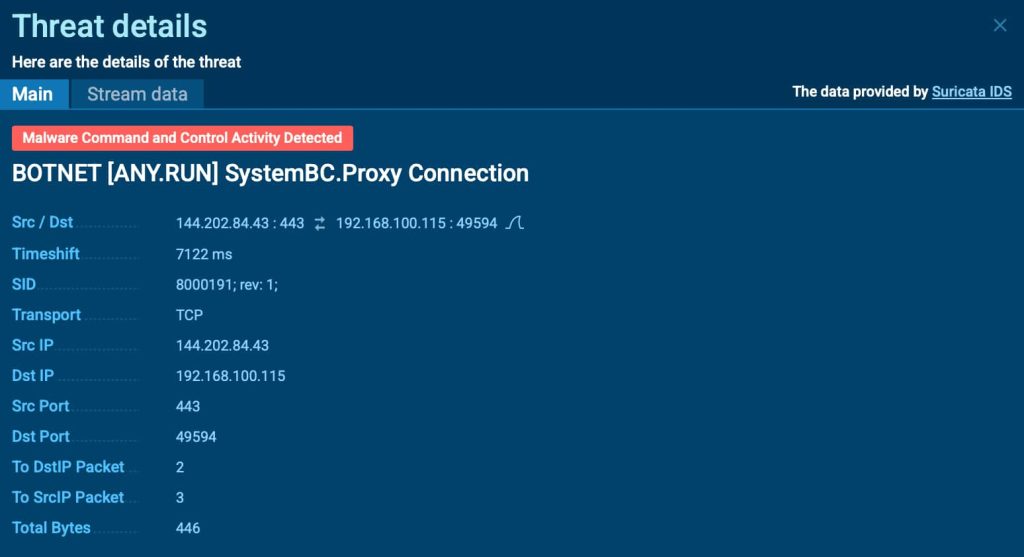
In the Threats section, we can see that an alert was triggered by the Suricata rule: “Malware Command and Control Activity Detected – BOTNET SystemBC.Proxy Connection.” This immediate detection allows analysts to track the infection process and understand how the malware operates.
| Equip your team with real-time threat analysis to detect and respond to malware faster. Start your 14-day free trial with ANY.RUN! |
Proxy Implant for Lateral Movement
The malware operates as a proxy implant, meaning it can facilitate lateral movement within a compromised network without deploying additional, easily detectable tools. This makes it a powerful weapon for attackers who seek persistence and deeper infiltration within corporate infrastructures.
Evasion of Traditional Detection
One of the most concerning aspects is that security vendors struggle to detect this version as belonging to the SystemBC family. This stealthy approach allows the RAT to remain undetected for extended periods, making it a persistent threat.
Sandbox and Virtualization Evasion
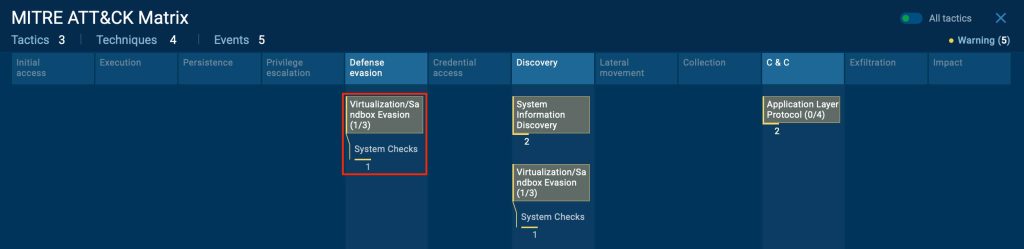
Besides signature-based evasion, SystemBC also detects virtualized environments to resist dynamic analysis. In a real ANY.RUN analysis session mentioned above, the MITRE ATT&CK framework flags reveal “Virtualization/Sandbox Evasion- System Checks,” showing that the malware actively performs system checks to determine if it’s running inside a security sandbox or virtual machine.
By identifying these environments, SystemBC can alter its behaviour or terminate execution, helping attackers bypass automated malware analysis tools while remaining fully operational on real infected systems.
Integration with Other Malware Strains
SystemBC is rarely deployed on its own. It often works alongside other malware to expand an attack’s impact. In Windows attacks, it has been observed delivering ransomware like Ryuk and Conti, as well as banking trojans and infostealers.
With its new Linux variant, similar threats will likely follow, putting enterprise servers and cloud environments at greater risk of data theft, ransomware encryption, and persistent backdoor access.
Unmasking Hidden Threats Before They Strike
Cyber threats are getting smarter, and businesses can’t afford to play catch-up. With SystemBC RAT now hitting Linux, attackers have a new way to hide C2 traffic, move through networks unnoticed, and drop additional malware. Traditional security tools often miss these stealthy tactics, leaving corporate networks, and critical infrastructure at risk.
However, with tools like ANY.RUN interactive sandbox, hidden doesn’t mean unstoppable. Your security team can:
- Analyze threats safely in a controlled environment.
- Respond faster, containing threats before they spread and cause real harm.
- Spot evasion techniques before they do damage, exposing how threats slip past defences.
- Extract key IOCs, strengthening your threat intelligence and prevention strategies.
- See hidden malware behaviours in real-time, from network traffic to system changes.