Ticketmaster hackers leak 30,000 ticket barcodes for top upcoming events, including music concerts. They also share a DIY counterfeit tutorial on making physical tickets from the leaked barcodes and other ticketing data.
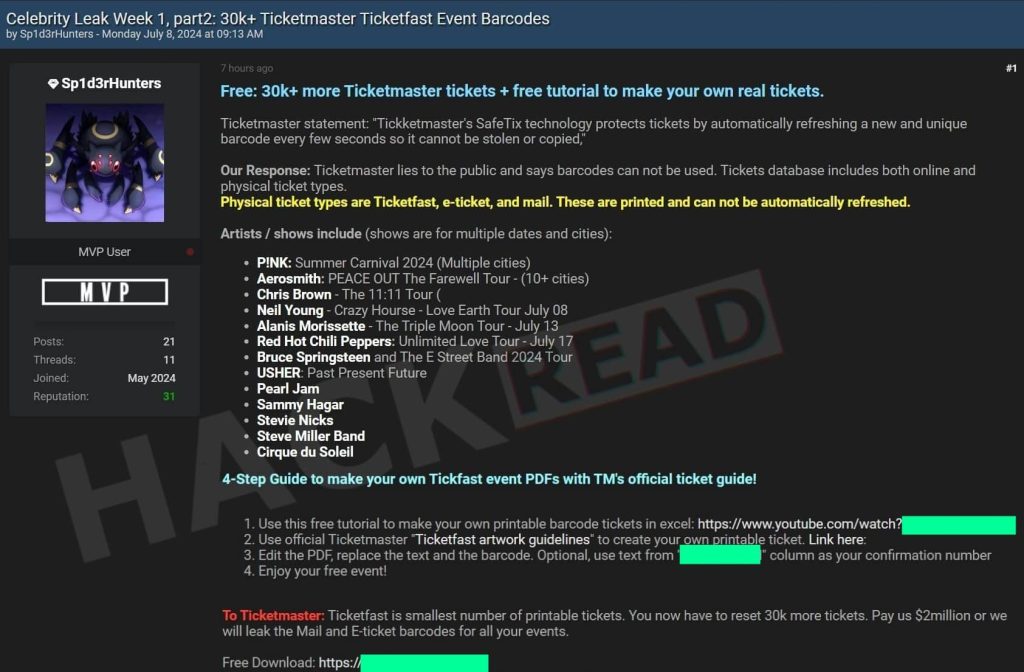
Ticketmaster hackers have leaked 30,000 additional ticket barcodes for some of the top upcoming events and concerts featuring popular artists and music bands.
It is also worth noting that on July 4 and 5, 2024, as exclusively reported by Hackread.com, ShinyHunters and Sp1d3rHunters, who are two different individuals but are affiliated with the group behind the Ticketmaster data breach, leaked 44,000 and 170,000 ticket barcodes related to Taylor Swift’s The Eras Tour. With these leaks, the total number of leaked ticketing data goes up to 640,000.
The latest 30,000 data leak includes ticketing and barcodes related to the following events and artists:
- Pearl Jam
- Sammy Hagar
- Stevie Nicks
- Steve Miller Band
- Cirque du Soleil
- USHER: Past Present Future
- Chris Brown – The 11:11 Tour
- P!NK: Summer Carnival 2024 (Multiple cities)
- Aerosmith: PEACE OUT The Farewell Tour – (10+ cities)
- Neil Young – Crazy Horse – Love Earth Tour July 08
- Alanis Morissette – The Triple Moon Tour – July 13
- Red Hot Chili Peppers: Unlimited Love Tour – July 17
- Bruce Springsteen and The E Street Band 2024 Tour
What Exactly is in This Data Leak?
The ticket industry is a complicated one. Although Hackread.com has over a decade of experience in data breach analysis, things can be tricky sometimes. Therefore, we used ChatGPT-4o to analyze a small sample from the leak. Here’s what it found:
The leak of Ticketmaster ticketing data, including barcodes, is indeed bad news for Ticketmaster and its customers. Here's an analysis:
What is in the Leak
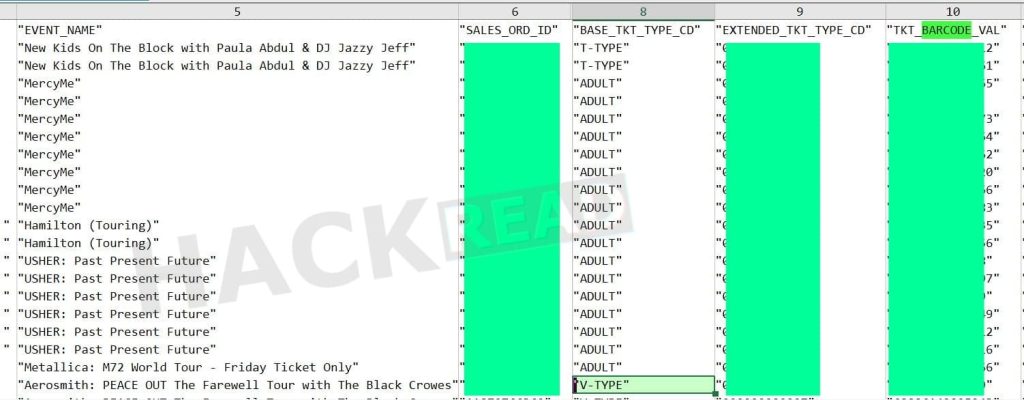
The provided data includes:
1: Ticket Barcodes: Unique ticket barcode values.
2: Event Details: Start time, event key, event ID, event name, venue details, etc.
3: Sales Order Information: Sales order ID, transaction ID, ticket type codes.
4: Seating Information: Section name, row number, seat number.
5: Venue Info: Venue ID, venue name, address, city, state, country, postal code.
6: User and Session Information: Browser ID, web session cookie values.
Potential Risks and Implications
Ticket Forgery and Resale:
Barcode Duplication: The leaked barcodes can be duplicated to create counterfeit tickets. Fraudsters could print fake tickets using these barcodes and sell them to unsuspecting buyers.
Loss of Revenue: Counterfeit tickets can lead to revenue loss for both Ticketmaster and event organizers.
Overcrowding and Security Risks: Events could face overcrowding if counterfeit tickets are used, leading to security and safety issues.
Verification Challenges: Ensuring the authenticity of tickets at event entry points will become more challenging, potentially causing delays and operational disruptions.
Increased Costs: Implementing measures to mitigate the impact of the leak, such as reissuing tickets or enhancing verification processes, will incur additional costs.
This leak is a significant issue for Ticketmaster, requiring immediate and comprehensive action to mitigate the risks and prevent future occurrences.
Can Anyone Use These Tickets?
Well, kind of. The online tickets could be impossible to use, but apparently, the physical copies of tickets can be used without any hurdles. Last week, Ticketmaster told Hackread.com that there is no way to use these tickets because the company uses a technology called “SafeTix,” which protects tickets by automatically refreshing with a new and unique barcode every few seconds, making it impossible to reuse.
However, the company did not mention anything about physical copies of tickets, which hackers have pointed out in their latest counterstatement, announcing that they have extracted physical tickets as well.
“Our Response to Ticketmaster’s claims is Ticketmaster lies to the public and says barcodes can not be used. The ticket database we have includes both online and physical ticket types.”
Hackers
What’s worse for Ticketmaster is that the hackers have also shared a four-step tutorial explaining how to make your own real tickets using the leaked information. This includes a YouTube video, Ticketmaster’s TicketFast artwork guidelines, and a link to the Ticketmaster site explaining printing guidelines for their tickets. Hackread.com will not share the complete tutorial due to security reasons.
Who is Behind the Ticketmaster Data Breach?
The original Ticketmaster data breach saw claims from the ShinyHunters hacker group of stealing 560 million user records and a ransom demand of $1 million—an offer that Ticketmaster denies it ever facilitated or has any plans to accept.
Last week, the ransom demand increased to $8 million after ShinyHunters revealed (in a now-deleted post on Breach Forums) that the stolen data was larger than previously anticipated, making it more valuable than ever. This includes the following information:
- 980 million sales orders
- 680 million orders detail
- 1.2 billion party lookup records
- 440 million unique email addresses
- 4 million uncased and deduped records
- 560 million AVS (Address Verification System) detail records
- 400 million encrypted credit card details with partial information
But who is the threat actor or group behind the Ticketmaster data breach? According to two known cybersecurity researchers who shared exclusive information on the basis of anonymity, ShinyHunters is not behind this data breach but is merely affiliated with a high-profile, financially motivated threat group that is the actual actor behind the breach.
The name of the threat group cannot be shared at this time due to security reasons and for reasons Hackread.com would rather not disclose until authorities do so on their own. On the other hand, sources also told Hackread.com that Sp1d3rHunters is also not involved in the breach; their main role is to post about the breach on different forums to attract as many potential buyers as possible.
Nevertheless, it’s another day with more bad news for Ticketmaster. If you are a Ticketmaster user, make sure to change your account password and keep an eye on any suspicious activity.