Cybersecurity researchers at Fortinet’s FortiGuard Labs have discovered a new threat called Vcurms malware targeting popular browsers and apps for login and data theft. They urge security updates and caution with emails.
Fortinet’s FortiGuard Labs recently uncovered a new cybersecurity threat: a malware known dubbed “Vcurms.” The attackers behind Vcurms malware have employed sophisticated tactics, using email as their command and control center and leveraging public services such as AWS and GitHub to store the malicious software. Additionally, they have employed a commercial protector to evade detection, indicating a concerted effort to maximize the malware’s impact.
Targeting Java Platforms
This campaign primarily targets platforms with Java installed, posing a risk to any organization utilizing such systems. The severity of the threat cannot be understated, as successful infiltration grants attackers full control over compromised systems.
Tactics and Techniques: Spreading Vcurms
The modus operandi of the attackers involves luring users to download a malicious Java downloader, which serves as a vector for spreading Vcurms and STRRAT, a trojan previously found to be posing as fake ransomware infection to steal data. These malicious emails typically masquerade as legitimate requests, urging recipients to verify payment information and download harmful files hosted on AWS.
Phishing Traits
Once downloaded, the malware exhibits classic phishing traits, employing spoofed names and obfuscated strings to disguise its nefarious nature. Notably, it utilizes a class named “DownloadAndExecuteJarFiles.class” to facilitate the downloading and execution of additional JAR files, further expanding the attacker’s foothold.
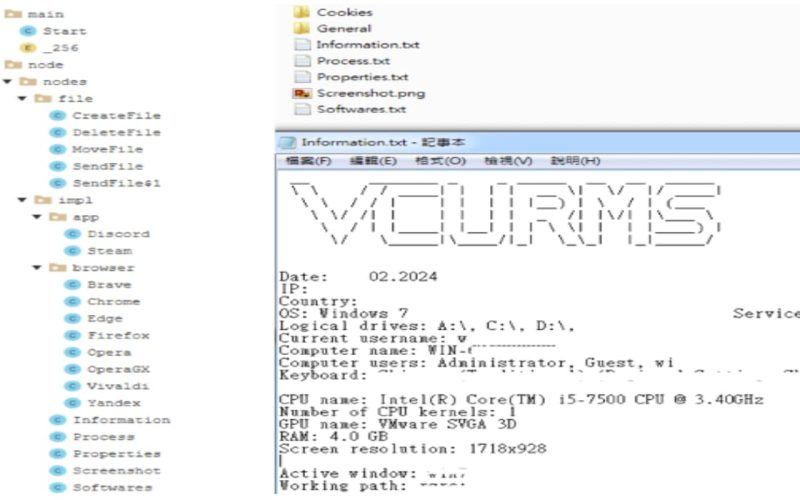
The Remote Access Trojan (RAT) component of Vcurms communicates with its command and control center via email, demonstrating a concerning level of sophistication. It establishes persistence by replicating itself into the Startup folder and employs various techniques to identify and monitor victims, including keylogging and password recovery functionalities.
Targeting Popular Browsers and Apps
Furthermore, the malware employs advanced obfuscation techniques, such as the Branchlock obfuscator, to evade detection and analysis. Despite these challenges, cybersecurity researchers continue to develop methods for deobfuscating and understanding the inner workings of Vcurms.
Vcurms also exhibits notable similarities with the Rude Stealer malware but distinguishes itself through its unique transmission methods and targeted data acquisition. It prioritizes stealing sensitive information from popular browsers like Chrome, Brave, Edge, Vialdi, Opera, OperaGX, Firefox, etc. and applications, including Discord and Steam.
In response to this threat, FortiGuard Labs in their blog post, recommend proactive measures, including the deployment of updated security solutions and network segmentation. Additionally, maintaining vital password practices and exercising caution when handling email attachments are crucial steps in mitigating the risk of Vcurms infection.
Commenting on this, Jason Soroko, Senior Vice President of Product at Sectigo, emphasizes the importance of authentication methods in combating malware attacks.
“Malware writers are benefiting from the cloud and that shouldn’t surprise anyone. RAT malware typically harvests whatever it can, and the new VCURMS and STRRAT remote access trojans seem to have one or more keyloggers,“ Jason warned. “This technique has been around for quite some time and is yet another example of why stronger authentication methods than simply a username and password are necessary.“
Related News
- ToxicEye RAT hits Telegram app to spy, steal user data
- Fake Skype, Zoom, Google Meet Sites Infecting Devices with RATs
- AsyncRAT Infiltrates Key US Infrastructure Through GIFs and SVGs
- BRATA Android malware factory resets phones after stealing funds
- New Bifrost RAT Variant Targets Linux Devices, Mimics VMware Domain