Security experts at Dr. Web have warned Android users to be careful with a new Trojan that is stealing credit card details while making a transaction on Google Play store. It is currently targeting Russian users but a little bit of modification can let the criminals target people around the world.
The Trojan comes in the shape of a fake Adobe Flash Player, once installed and run, it asks for administrator privileges on the Android device after every 0.1 seconds. It does it by the continuously irritating user to grant it the admin privileges through a non-stop popup message. It will keep on asking until the user finally lets the Trojan take over the admin panel.
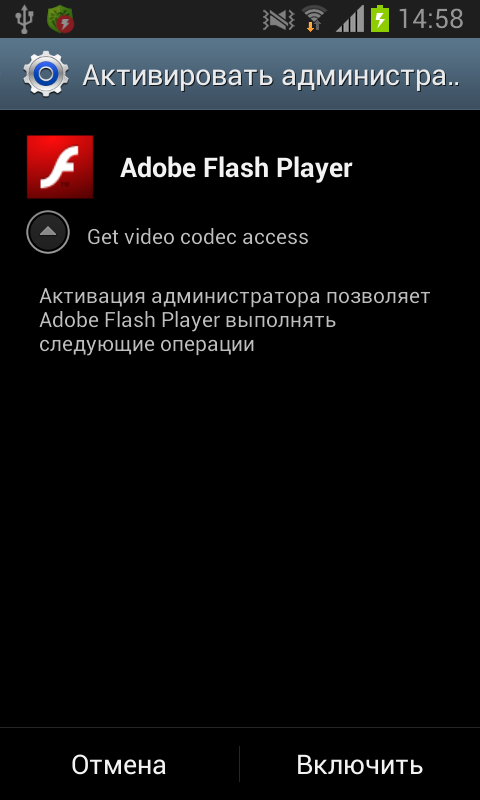
Dubbed as Android.BankBot.21, once the Trojan gets access to admin section; it checks if there is an active Google Play app window.
If one is present, the malware displays a standard credit card information form used to associate a credit card with an account, the researchers note. All the submitted information, such as the card number, expiration date, and CVC code, and the address and phone number of the cardholder, is transmitted to the attacker’s server.
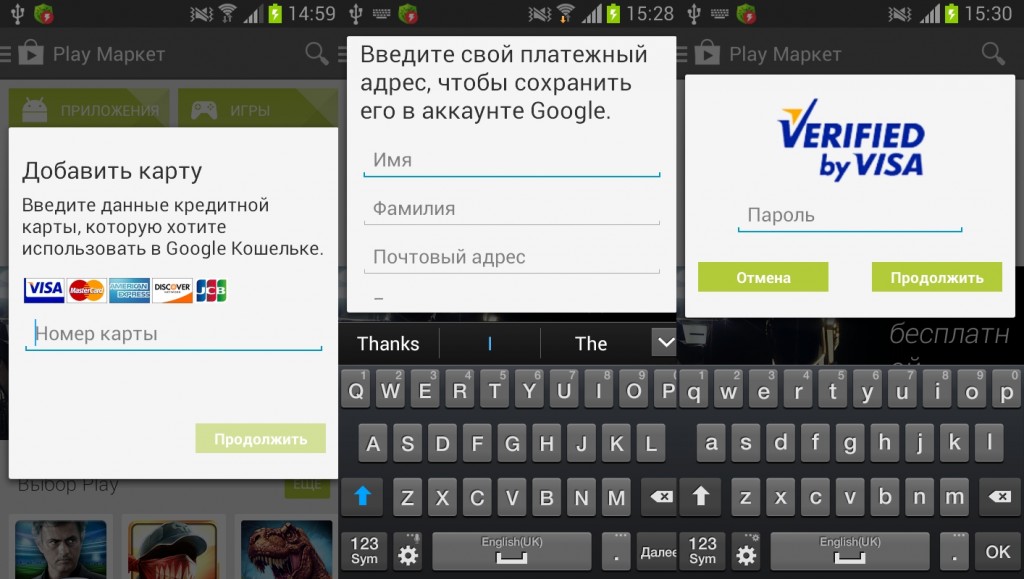
The BankBot Android Trojan also collects sensitive information from the infected device such as credit card number, CVC number, its expiration date and user’s home address. It is also able to collect device specs such as a list of installed apps, OS version, IMEI, and phone model and send it to the hacker.
Last but not the least, the BankBot Android Trojan can also take over the phone’s SMS function and send messages to any number at any time. We at HackRead advise Android users to be careful of the fake flash player and don t fall for tricks used by cybercriminals.