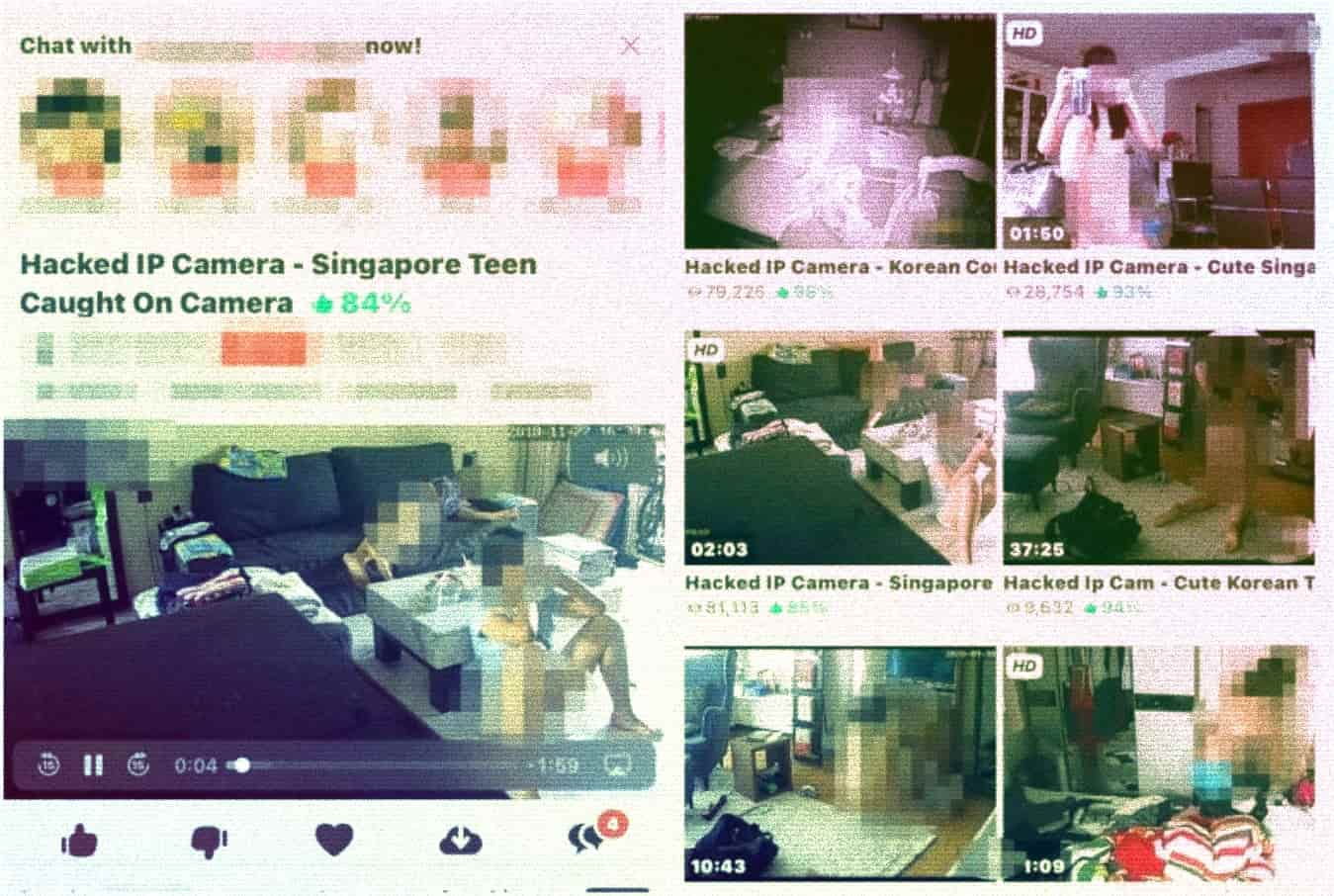
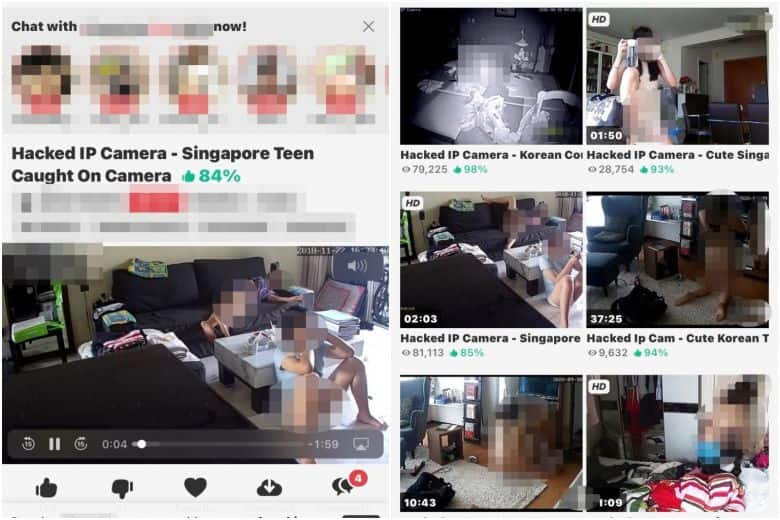
These clips were recorded from home security cameras featuring people’s daily and even personal lives.
As of 2019, there were over 770 million security cameras around the world, and when it comes to the Internet of Things (IoT) devices, in total, there are over 28 billion IoT devices currently connected to the Internet.
While security cameras play a vital role in remotely monitoring children, the elderly, and pets, etc., they are also a lucrative target for cybercriminals especially when a huge number of these devices are known to be vulnerable and exposed to public access.
Keeping that in mind; it has been reported that cybercriminals were able to hack thousands of home Internet Protocol (IP) cameras, record live footage, and upload them on explicit and x-rated websites.
According to authorities, these clips featured victims in compromising positions, such as some undressing, using toilets, couples, mothers breastfeeding, and even children.
The victims of this scam belong to countries like Singapore, Canada, South Korea, and Thailand, the report suggests.

Apparently, 3 Terabyte (TB) worth of recorded clips have not only been uploaded but also sold to interested parties or offered as lifetime access for a one-time subscription fee of US$150.
A closer check of the videos revealed that a group dedicated to hacking IP cameras was behind the hacking. The group, which can be found on the social messaging platform Discord, has almost 1,000 members across the globe A 700MB “sample”, containing about 4,000 videos and pictures from the hacked footage, is provided free, The News Paper said
Hackread.com can confirm that some clips also featured underage school girls watching TV or doing homework based on school books around them.
This should not come as a surprise as back in 2014 Hackread.com published an in-depth report on a website showing live footage from hundreds of thousands of exposed private security cameras.
The website which is still online now features surveillance footage from businesses, malls, offices, warehouses, parking lots, but most importantly cribs, bedrooms, living rooms, and kitchens.
Why security cameras are vulnerable or easy to hack?
To answer this, we must look at how security cameras work. Every time one is installed, users need some remote way in order to access their footage either in real-time or later for play-back. The access mechanisms can be divided into two networking protocols, namely port forwarding and peer to peer(P2p).
In port forwarding through the use of Universal Plug and Play (UPnP) technology, the camera can be accessed by a port on the external IP address. If there is no authentication method, anyone who knows the IP address of the device can access the footage and other privileges depending on the manufacturer’s setup.
Secondly, in P2P, the device itself communicates with the manufacturer’s servers for administration and other functions without port forwarding leaving no need for port forwarding.
How to protect your security camera from hackers?
These security cameras are supposed to offer security, not provide surveillance footage for anyone to view. It is definitely creepy to think security surveillance footage meant for protection could turn into an invasion of privacy. However, if you want to save yourself from such a situation, as a first step, just change the default password of your security camera.
Furthermore, one can also add other measures such as whitelisting only one’s own device’s MAC addresses, choosing vendors with a focus on security, enabling two-factor authentication, and finally using an encrypted connection to access the admin panel.
Finally, If you’re not a technically interested user, checking if your public IP address is compromised through a search engine like Shodan can also help for the immediate time being helping you decide your next course of action.
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.










Anyone who is not familiar with network security contemplating installing cameras inside their home should contact an MSP before doing so. Failure to secure the cameras properly, unfortunately, could result in what has happened in your article.