The researchers managed to identify and report the presence of Joker malware in 8 apps on Google Play Store.
In the past three years, the Joker malware has made headlines quite frequently by invading applications available on Google Play Store. The malware infects the user’s device after the infected application is downloaded and keeps collecting data secretly.
This time again, it is spotted by Quick Heal Security Labs in eight apps on Google Play Store. The researchers notified Google about this issue, after which the company removed all the infected apps.
Which Apps are Laced with Joker Malware?
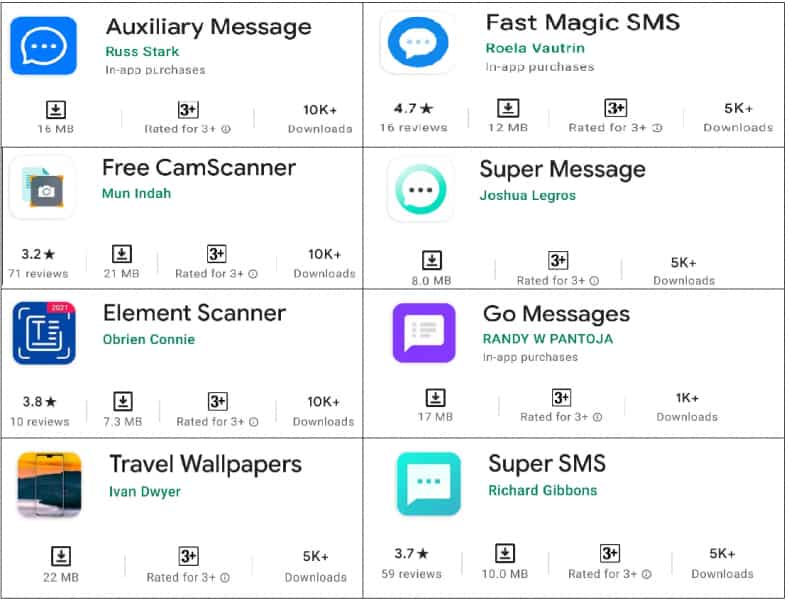
In total, eight applications were found to be infected with the Joker Trojan virus. The following android apps must be removed immediately if you have downloaded them:
- Auxiliary Message
- Fast Magic SMS
- Free CamScanner
- Super Message
- Element Scanner
- Go Messages
- Travel Wallpapers
- Super SMS
The Notorious Joker Trojan
This dangerous malware steals information from the contact list, SMS messages, and device info from the victim’s device and quietly interacts with advertisement sites. It also subscribed the victim to premium services.
Beware of Joker Malware
In the present scenario, as reported by Quick Heal, when the infected application is launched after downloading, it requests notification access to get notification data. It then takes SMS data from the notification and then asks for Contacts access.
When the access is provided, the app requests phone call permission and continues to work in the background without letting the victim suspect anything.
Additionally, it secretly downloads two payloads, one of which is downloaded from a Bitly shortened URL link (bitly/3hT17RL). It is present in the original app on Google Play Store.
The next payload is downloaded from skullalioss-me-east 1aliyuncs.com/realease.mp3. This is the Joker malware payload and contains the code for notification access and the onReceive method.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.