A new Android malware called Trojan Ajina.Banker is targeting Central Asia – Discover how this malicious malware disguises itself as legitimate apps to steal banking information and intercept 2FA messages. Learn about the tactics used by the attackers and how to protect yourself from this growing threat.
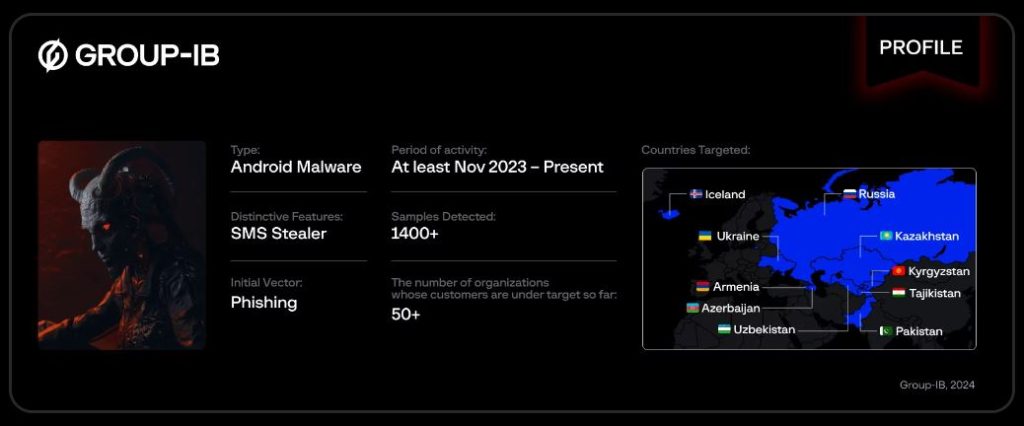
Central Asia has become the target of a malicious new campaign distributing Android malware dubbed “Ajina.Banker.” Discovered by Group-IB in May 2024, Ajina.Banker has been wreaking havoc since November 2023 and around 1,400 unique variants of the malware were identified by researchers.
The malware is named after a malevolent Uzbek mythical spirit known for deception, shape-shifting, and chaos. Ajina.Banker targets unsuspecting users by masquerading as trusted applications like banking services, government portals, and everyday utilities “to maximize infection rates and entice people to download and run the malicious file, thereby compromising their devices.”
The malware primarily spreads through social engineering tactic on messaging platforms like Telegram. Attackers create numerous accounts to distribute malicious links and files disguised as enticing offers, promotions, or even local tax authority apps. Users lured by the promise of “lucrative rewards” or “exclusive access” unknowingly download and install the malware, compromising their devices.
The attackers also employ a multi-pronged approach, sending messages with just the malicious file attached, exploiting user curiosity. Additionally, they share links to channels hosting the malware, bypassing security measures in place on some community chats.
Ajina used themed messages and localized promotion strategies to create a sense of urgency and excitement in regional community chats, urging users to click on links or download files without suspecting malicious intent. These campaigns were conducted across multiple accounts, sometimes simultaneously, indicating a coordinated effort.
While primarily targeting users in Uzbekistan, Ajina.Banker’s reach extends beyond borders. The malware collects information on installed financial applications from various countries, including Armenia, Azerbaijan, Iceland, and Russia. Additionally, it gathers SIM card details and intercepts incoming SMS messages, potentially capturing 2FA codes for financial accounts.
The malware exhibits a concerning level of adaptability. The analysis reveals two distinct versions – com.example.smshandler and org.zzzz.aaa – suggesting ongoing development. Newer versions showcase additional functionalities, including the ability to steal user-provided phone numbers, bank card details, and PIN codes.
Group-IB’s investigation suggests Ajina.Banker operates on an affiliate program model. A core group manages the infrastructure, while a network of affiliates handles distribution and infection chains, likely incentivized by a share of the stolen funds.
To protect yourself and your devices from Ajina.Banker and similar threats, be cautious of unsolicited messages and downloads, stick to trusted app stores like Google Play Store, scrutinize app permissions, install security software, and stay updated on the latest malware threats and best practices for mobile security.
Rocky Cole, Co-Founder and COO of mobile device security company iVerify shared his comments about this cunning new campaign with Hackread.com:
“Credential theft is the number one action being taken by threat actors. It’s so easy to steal credentials on phones where smaller screens, lower attention spans, lack of training, and the mixing of personal and professional use cases put people at risk. This new Android malware is just a continuation of that trend and a prime example of why phones should be running EDR platforms to detect malicious APKs and social engineering attempts.”