Microsoft cybersecurity experts have identified a vulnerability flaw affecting ASP.NET applications, putting thousands of web servers at risk. The issue originates from developers using publicly available ASP.NET machine keys in their configurations; keys that hackers are now exploiting to execute ViewState code injection attacks.
A recent attack in December 2024 used this vulnerability to deliver Godzilla, a dangerous post-exploitation framework capable of executing commands, injecting shellcode, and maintaining persistent access to compromised servers. Microsoft warns that over 3,000 publicly disclosed machine keys could be weaponized for similar attacks.
Why This Matters
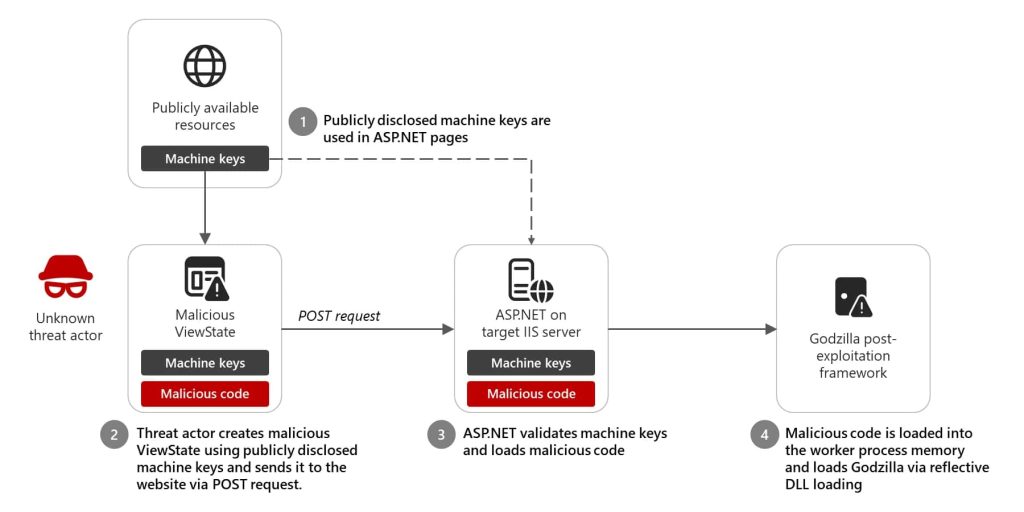
ASP.NET machine keys are meant to protect web applications by encrypting and validating ViewState data, ensuring that attackers cannot tamper with it. However, some developers have mistakenly copied these keys from online resources, unknowingly allowing hackers to generate and inject malicious ViewState data into their servers.
Once a hacker has access to the right machine key, they can craft a malicious payload and send it to a vulnerable website. The server, trusting the key, decrypts and executes the attacker’s code—leading to full remote code execution.
What Happened in December 2024?
An unidentified hacker took advantage of a publicly known ASP.NET machine key to deploy Godzilla, a post-exploitation tool that provides remote access to compromised servers. The attack began with injection, where the attacker sent a malicious ViewState payload using a leaked machine key.
Once received, the server decrypted and executed the code, unknowingly running the attacker’s instructions. This led to Godzilla deployment, where the payload triggered the execution of assembly.dll, loading the framework and allowing further exploitation.
Microsoft’s Response
According to Microsoft’s blog post, the company has removed machine key samples from public documentation to discourage bad security practices. The company has also issued new detection alerts via Microsoft Defender for Endpoint to flag any usage of publicly disclosed machine keys.
If your system is compromised, simply rotating the machine keys may not be enough. Microsoft advises a full forensic investigation, as attackers may have installed backdoors or additional malware.
Tim Mackey, Head of Software Supply Chain Risk Strategy at Black Duck commented on the new development stating, “This misconfiguration allows attacks by using ViewState payloads encrypted with publicly available keys, often from demo code. Developers should replace sample keys, but some copy them without understanding the risk. Hardcoded keys in production signal poor configuration. Checking against Microsoft’s public key list helps, but DevOps teams should also use tools to detect and remove hardcoded secrets.”
Protecting Yourself
To protect your web servers from attacks, start by replacing any publicly available machine keys if they were copied from online sources. Next, rotate and secure your keys by generating new ones and applying them consistently across all servers in your web farm.
Additionally, encrypting machine keys in the web.config file will help prevent exposure. Monitoring for suspicious activity is also essential. Microsoft Defender now detects publicly disclosed ASP.NET machine keys, and enabling attack surface reduction rules can help block web shell attacks.
Upgrading to ASP.NET 4.8 enhances security by incorporating Antimalware Scan Interface (AMSI) support. Finally, conducting a security audit is important. If a machine key has been exposed, assume a breach, investigate thoroughly, and check for unauthorized access.