Boeing mentioned that the cyberattack primarily affected its information systems, particularly within its parts business. However, the company did not confirm whether it was a ransomware attack or it paid a ransom to Lockbit.
Boeing confirmed on November 2, 2023, that it was the target of a cyberattack that occurred in late October 2023. The attack affected some of Boeing’s information systems, mainly in its parts business. Boeing is actively working with law enforcement and cybersecurity experts to investigate the incident and recover any impacted data.
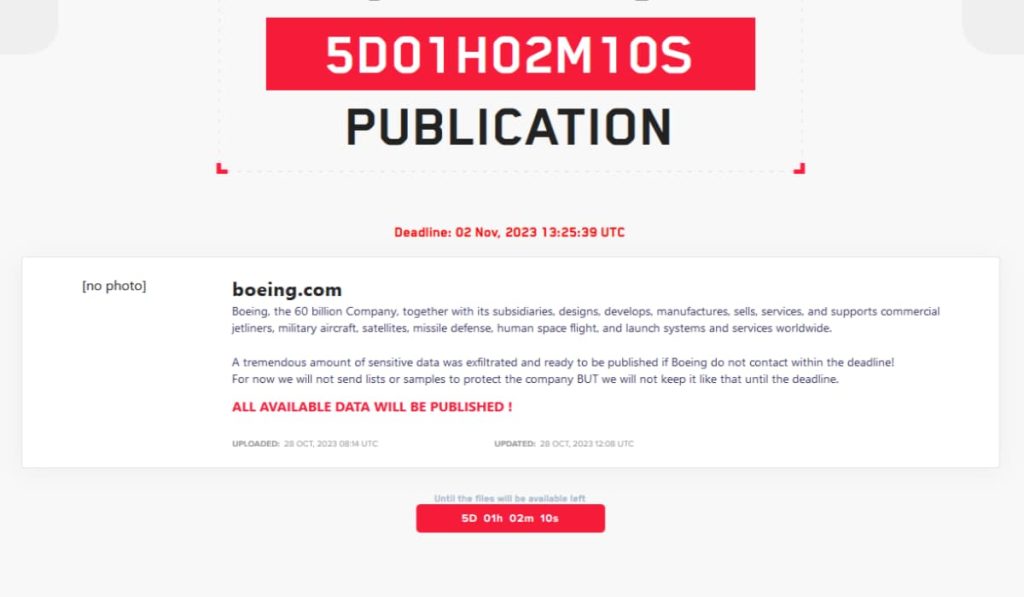
The acknowledgement came after the Lockbit ransomware group claimed responsibility for a ransomware attack on Boeing a few days earlier. The Lockbit group is known for encrypting a victim’s data and demanding ransom for decryption. They had mentioned Boeing as their new target on their dark web blog but later removed the post, suggesting negotiations were underway.
Speculation arose about whether Boeing was actually breached by the group. Some experts, like Jon DiMaggio, suggested that the LockBit Group might be in decline or compromised, but Boeing’s confirmation indicates the group is still active.
While discussing the LockBit ransomware group, vx-underground, an online repository for malware samples tweeted that, “Lockbit is not simply a group of individuals operating from a basement. They consist of administrators, developers, money launderers, and notably collaborate with affiliates and other threat groups.”
Ironically, the cyberattack on Boeing occurred just after the US announced an alliance of 40 countries to combat ransomware threats, emphasizing a stance against paying ransom to threat actors.
Boeing has not disclosed whether a ransom was paid. However, the company assured that it is working to restore affected systems without disrupting its business operations.
William Wright, CEO of Closed Door Security, suggested the cyberattack might have exploited a zero-day vulnerability. He stressed the importance of Boeing conducting thorough forensics into the attack promptly.
“Based on the information available, it looks like the incident was executed via a zero-day vulnerability. Which vulnerability remains to be seen, and we also don’t know if other criminal gangs are actively exploiting it as well,” Wright argued. “The sooner Boeing carries out its forensics into the attack the better.”
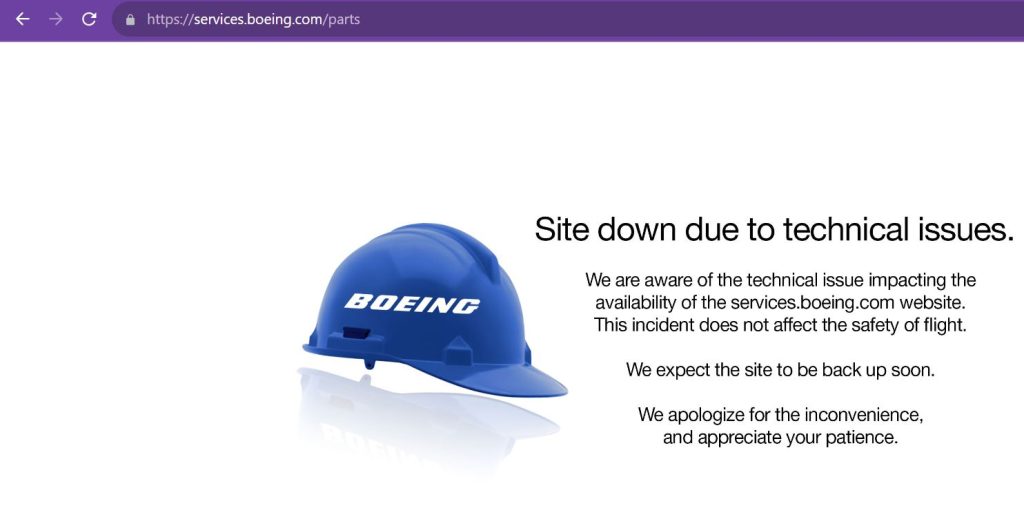
The story is still developing, so expect more updates soon. However, at the time of publishing this article, Boeing’s parts and distribution domain was offline due to technical issues.
This incident isn’t the first time Boeing faced a cyber attack. In March 2018, a malware attack introduced the notorious WannaCry ransomware. In March 2020, the DoppelPaymer ransomware targeted several prominent companies, including SpaceX, Tesla, and a parts manufacturer associated with Boeing.
RELATED ARTICLES
- Bangkok Airways hit by Lockbit ransomware; leaks 103GB of data
- Accenture claims to fight off LockBit ransomware gang with backup
- LockBit ransomware gang blames victim for DDoS attack on its website
- LockBit 3.0 Posts Dubious Claims of Breaching Darktrace Cybersecurity Firm
- Cyber Security Giant Mandiant Denies Hacking Claims By LockBit Ransomware