Browsing Category
Malware
1711 posts
16 Fake ChatGPT Extensions Caught Hijacking User Accounts
A coordinated campaign of 16 malicious GPT optimisers has been caught hijacking ChatGPT accounts. These tools steal session tokens to access private chats, Slack, and Google Drive files.
January 27, 2026
Poland Thwarts Russian Wiper Malware Attack on Power Plants
Poland blocked a Russian wiper malware attack on power and heating plants, officials say, avoiding outages during winter and prompting tighter cyber rules.
January 27, 2026
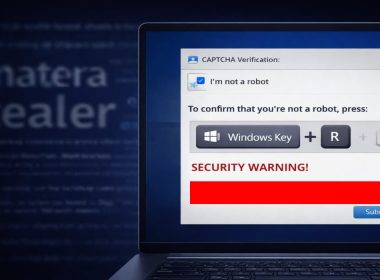
New Fake CAPTCHA Scam Abuses Microsoft Tools to Install Amatera Stealer
Another day, another fake CAPTCHA scam, but this one abuses Microsoft’s signed tools.
January 26, 2026
$6,000 “Stanley” Toolkit Sold on Russian Forums Fakes Secure URLs in Chrome
Say hello to Stanley, a new malicious toolkit that guarantees bypassing Google’s Chrome Web Store review process.
January 26, 2026
149M Logins from Roblox, TikTok, Netflix, Crypto Wallets Found Online
Another day, another trove of login credentials in plain text found online.
January 23, 2026
Venezuelan Nationals Face Deportation After Multi State ATM Jackpotting Scheme
According to authorities, both suspects were in the United States unlawfully.
January 23, 2026
VoidLink Malware Puts Cloud Systems on High Alert With Custom Built Attacks
Sysdig TRT analysis reveals VoidLink as a revolutionary Linux threat. Using Serverside Rootkit Compilation and Zig code, it targets AWS and Azure with adaptive stealth.
January 22, 2026
ClickFix to CrashFix: KongTuke Used Fake Chrome Ad Blocker to Install ModeloRAT
Huntress discovers 'CrashFix,' a new attack by KongTuke hacker group using fake ad blockers to crash browsers and trick office workers into installing ModeloRAT malware.
January 20, 2026
Hackers Exploiting PDF24 App to Deploy Stealthy PDFSIDER Backdoor
Resecurity has identified PDFSIDER malware that exploits the legitimate PDF24 App to covertly steal data and allow remote access. Learn how this APT-level campaign targets corporate networks through spear-phishing and encrypted communications.
January 19, 2026
Mastang Panda Uses Venezuela News to Spread LOTUSLITE Malware
Researchers have found a new spying campaign using news about Venezuela to trick US government officials. Learn how the LOTUSLITE virus sneaks into computers to steal secrets.
January 19, 2026