Cybersecurity firm ESET uncovers PlushDaemon, a previously unknown APT group targeting South Korea, deploying a SlowStepper backdoor. This article analyses the attack techniques, the capabilities of the SlowStepper malware, and the growing threat posed by this sophisticated APT group.
Cybersecurity firm ESET has identified a new China-aligned Advanced Persistent Threat (APT) group, dubbed “PlushDaemon,” behind a cyber espionage operation targeting South Korea.
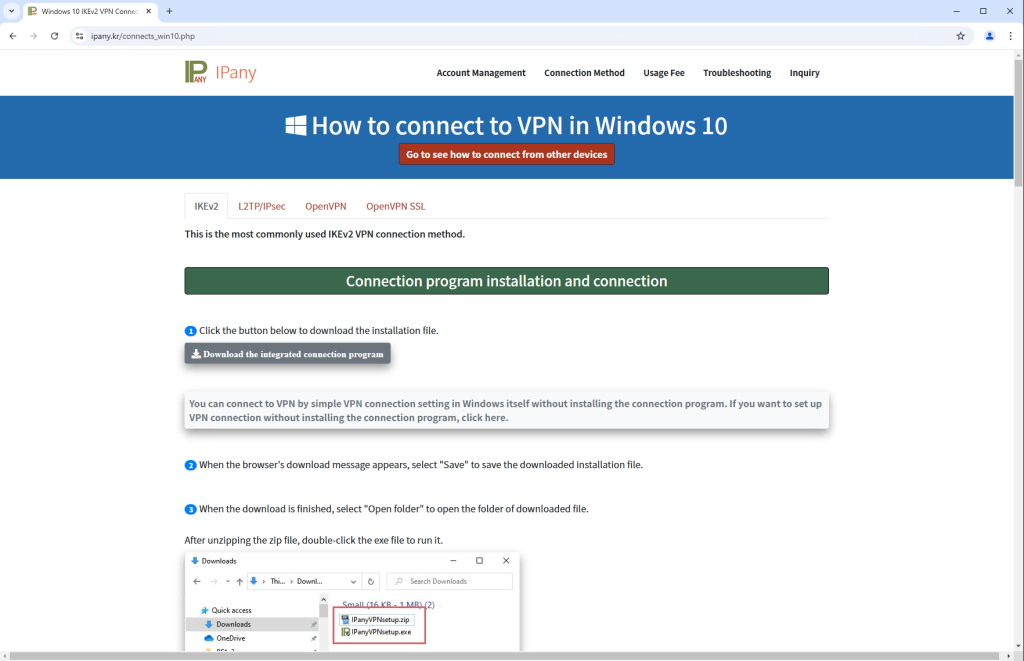
The attack camaign nvolved a supply chain compromise, where attackers infiltrated the legitimate update channels of IPany, a popular South Korean VPN software. PlushDaemon then replaced genuine installers with trojanized versions, which upon download and execution, deployed both the legitimate IPany VPN software and a custom backdoor named SlowStepper.
This means, by replacing the genuine installer with a trojanized version, PlushDaemon successfully embedded a malicious backdoor within the software. As per ESET’s research, SlowStepper is a feature-rich backdoor boasting over 30 modules. It is designed for extensive surveillance and data collection.
Written in C++, Python, and Go, the malware possesses a wide range of capabilities, including stealing sensitive data such as system information, user credentials, and network configurations, recording audio and video, enabling attackers to monitor their targets’ activities, and gathering detailed information about the victim’s network environment.
In addition, the backdoor features advanced persistence mechanisms, such as deploying files that ensure the continued presence of SlowStepper on infected systems and utilizing legitimate tools to sideload malicious code. The trojanized installer utilize advanced communication methods to connect with command-and-control (C&C) servers.
Instead of embedding IP addresses directly within the malware, SlowStepper crafts DNS queries to retrieve TXT records containing base64-encoded, AES-encrypted C&C server addresses. This multi-layered approach makes detection more challenging.
While ESET telemetry revealed manual downloads of the compromised software, suggesting a broad targeting strategy, the attack specifically focused on entities within South Korea’s critical semiconductor and software industries. The timely intervention of ESET, which alerted IPany to the compromised installer, prevented further widespread infection.
Although only recently discovered, researchers believe the PlushDaemon APT has been active since 2019, consistently building a diverse and powerful arsenal of tools. The sophistication of SlowStepper and the successful execution of this supply chain attack highlight the growing threat posed by this actor.
To stay safe from these cyber espionage groups there is an urgent need for continuous monitoring. Organizations must prioritize software update channel security and implement stringent verification procedures to ensure the integrity of all updates. Additionally, proactive threat intelligence sharing are vital for identifying and mitigating such attacks before they inflict damage.