SUMMARY
- Cleo Vulnerability Exploited: The Cl0p ransomware group claims to have exploited a critical vulnerability in Cleo’s managed file transfer software, targeting businesses globally.
- Data Leak Threats: Cl0p has announced plans to publish stolen data from affected organizations, increasing pressure on victims to pay ransom.
- Repeat Tactics: The attack mirrors Cl0p’s strategy used in the MOVEit and GoAnywhere breaches, focusing on high-impact vulnerabilities in widely used software.
- Supply Chain Risks: The exploitation of Cleo software poses a significant risk to supply chains, potentially disrupting operations across multiple industries.
- Urgent Patching Advised: Security experts urge organizations using Cleo products to immediately apply patches, review system security, and monitor for signs of compromise.
The Cl0p ransomware group has recently claimed responsibility for exploiting a critical vulnerability in Cleo’s managed file transfer (MFT) software, specifically targeting Cleo Harmony, VLTrader, and LexiCom products. This mirrors their previous attack on Progress Software’s MOVEit Transfer in 2023, where they exploited a zero-day vulnerability to breach systems and steal data.
In the MOVEit incident, Cl0p utilized a SQL injection vulnerability (CVE-2023-34362) to deploy a web shell named LEMURLOOT, enabling unauthorized access to databases and the extraction of sensitive information. This attack impacted several organizations globally, including government agencies and private enterprises, leading to significant data breaches and operational disruptions.
Cleo Vulnerability
The recent exploitation of Cleo’s software follows a similar modus operandi. Cl0p has announced its involvement, indicating the use of zero-day exploits to breach corporate networks and steal data. The specific vulnerability, now identified as CVE-2024-55956, has been acknowledged by Cleo, and organizations utilizing these products are urged to apply patches immediately to mitigate potential risks.
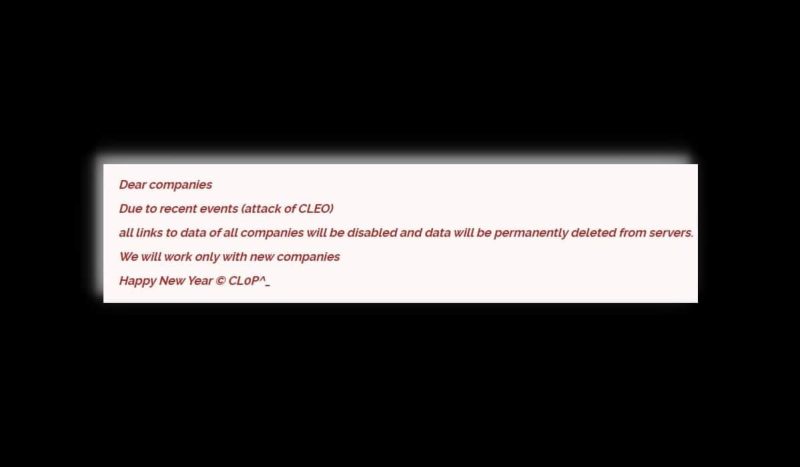
On its dark web blog, as seen by Hackread.com, the group posted the following message to substantiate its claims:
“Dear companies Due to recent events (attack of CLEO) all links to data of all companies will be disabled and data will be permanently deleted from servers. We will work only with new companies Happy New Year © CL0P^_.”
Ferhat Dikbiyik, Chief Research and Intelligence Officer at Black Kite commented on the situation:
“The Cl0p ransomware group has announced they’ll begin publishing victims from attacks exploiting CLEO vulnerabilities. This mirrors the MOVEit attacks of 2023, following Cl0p’s signature playbook: they don’t operate year-round but execute mass exploitation of Managed File Transfer (MFT) vulnerabilities in single, high-impact campaigns. We’ve seen this with GoAnywhere, with MOVEit, and now with CLEO,“ said Ferhat.
“Considering the impact of MOVEit, thousands of companies could be affected, either directly or indirectly. Organizations must stay vigilant, patch immediately, and assess their exposure to these vulnerabilities. It’s the holiday gift nobody wanted,“ he warned.
Cl0p’s strategy involves identifying and exploiting vulnerabilities in widely used MFT solutions and conducting large-scale attacks that can affect thousands of organizations simultaneously. Their approach emphasizes the importance of timely patch management and the need for organizations to maintain robust security postures, especially concerning third-party software dependencies.
RELATED TOPICS
- Starbucks Goes Manual After Blue Yonder Ransomware Attack
- Cl0p ransomware group members arrested, infrastructure seized
- Cl0p ransomware gang leaks sensitive data from 6 US universities
- TDECU Data Breach: 500,000+ Members Affected by MOVEit Exploit
- Massive MOVEit Hack: 630K+ US Defense Officials’ Emails Breached