Protect yourself from the ClickFix attack! Learn how cybercriminals are using fake Google Meet pages to trick users into downloading malware. Discover the latest tactics employed by these malicious actors and stay safe online.
Cybersecurity researchers at Sekoia have detected an uptick in cyberattacks targeting users of the popular video conferencing platform, Google Meet, employing a notorious tactic, dubbed “ClickFix.” This tactic emerged in May 2024 and involves mimicking legitimate services like Google Chrome, Facebook, or Google Meet, to trick users into downloading malware.
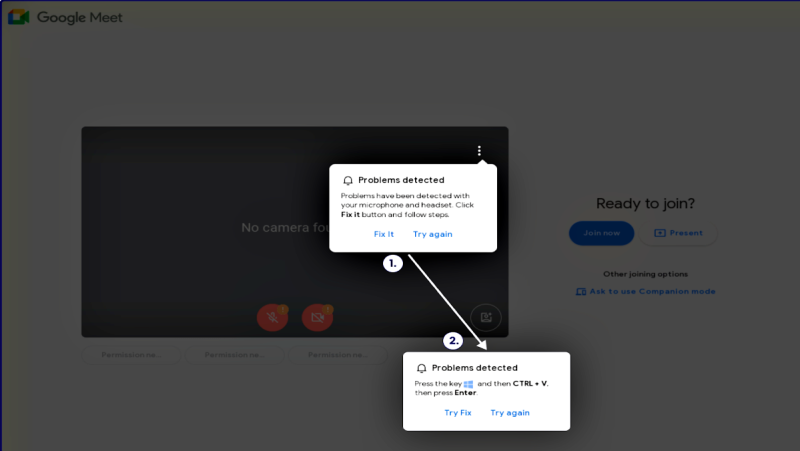
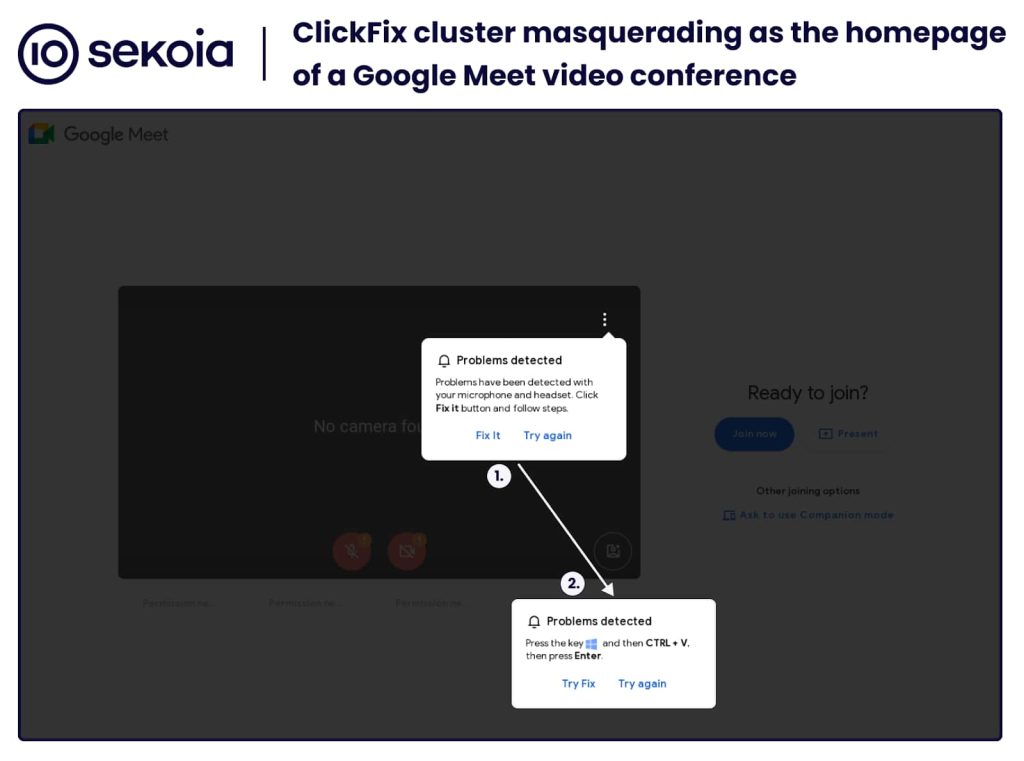
According to Sekoia’s report, attackers are displaying fake error messages mimicking legitimate alerts from Google Meet, prompting users to click a “Fix It” button or perform other actions. However, these actions unknowingly execute malicious code that installs malware on the victim’s device.
The ClickFix campaign leverages multiple malware distribution campaigns. Sekoia researchers analyzed a ClickFix cluster impersonating Google Meet video conferences, which targeted both Windows and macOS users.
For Windows users, the fake error message claimed microphone or headset issues, prompting them to copy a script that downloaded Stealc and Rhadamanthys infostealers. macOS users were tricked into downloading the AMOS Stealer malware.
“Given the variety of initial malicious websites redirecting to this infrastructure, we assess with high confidence that it is shared among multiple threat actors. They collaborate within a centralized Traffers team to share certain resources, including this infrastructure and the AMOS Stealer, which is also sold as Malware-as-a-Service.”
Sekoia
Possible Perpetrators
The investigation revealed that two cybercrime groups, “Slavic Nation Empire” (linked with cryptocurrency scam team Marko Polo) and “Scamquerteo Team” (a subgroup of cryptocurrency scam team CryptoLove), were likely behind this ClickFix cluster. These groups specialize in targeting users involved in cryptocurrency assets, Web3 applications, and decentralized finance (DeFi).
Both teams use the same ClickFix template to impersonate Google Meet, suggesting they share materials and infrastructure. Sekoia analysts estimate that both teams use the same cybercrime service to supply the fake Google Meet cluster, and it is likely that a third party manages their infrastructure or registers their domain names.
The malware delivered through these attacks includes infostealers, botnets, and remote access tools. These malicious programs can steal sensitive data, compromise systems, and enable further attacks.
ClickFix Scope
The ClickFix tactic is particularly dangerous because it bypasses traditional security measures. By not requiring users to download a file directly, it avoids detection by web browser security features. This makes it more likely to ensnare unsuspecting victims.
To protect yourself from ClickFix attacks, be cautious of unexpected error messages, verify scripts before copying and pasting them from unknown sources, use strong security software like antivirus and anti-malware, be cautious with links, and enable two-factor authentication to add an extra layer of security to your online accounts.
RELATED TOPICS
- Konni RAT Exploiting Word Docs to Steal Data from Windows
- Fake Chrome Browser Update Installs NetSupport Manager RAT
- Bifrost RAT Variant Targets Linux Devices, Mimics VMware Domain
- AsyncRAT Infiltrates Key US Infrastructure Through GIFs and SVGs
- Popular Android Screen Recorder iRecorder App Revealed as Trojan