Change.org, a famous online petition website is sending emails to its registered petitioners encouraging them to change their account password on the website. The email came days after Google employee, Tavis Ormandy of Project Zero exposed Cloudbleed bug that seems to have leaked sensitive and personal information passing through websites using CloudFlare’s service.
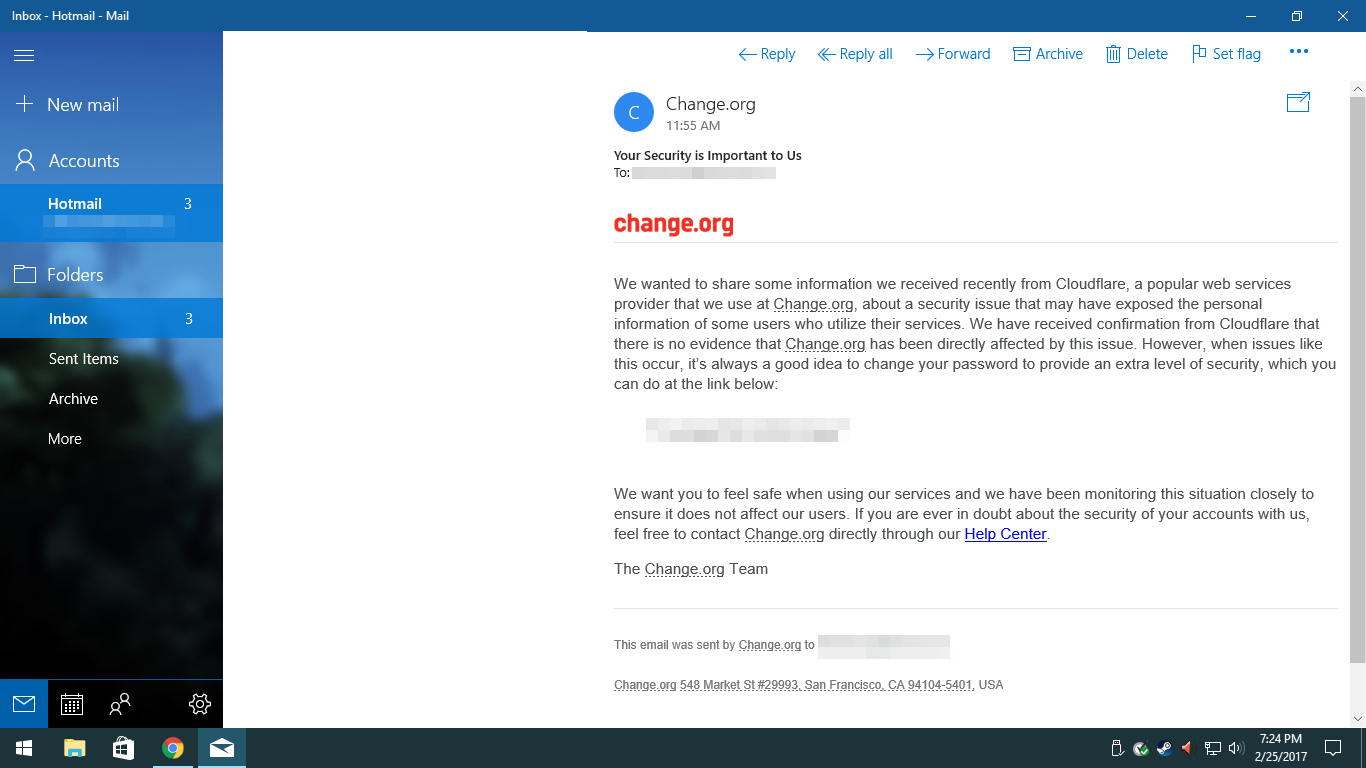
The email states that Change.org has received notification from CloudFlare about a security issue that may have exposed the personal information of some users who utilize their services. Although there is no evidence that Change.org has been directly affected by this issue, yet for users security, it is advisable to change their password. Here’s a full preview of the email sent by Change.org:
We wanted to share some information we received recently from Cloudflare, a popular web services provider that we use at Change.org, about a security issue that may have exposed the personal information of some users who utilize their services. We have received confirmation from Cloudflare that there is no evidence that Change.org has been directly affected by this issue. However, when issues like this occur, it’s always a good idea to change your password to provide an extra level of security, which you can do at the link below:
We want you to feel safe when using our services and we have been monitoring this situation closely to ensure it does not affect our users. If you are ever in doubt about the security of your accounts with us, feel free to contact Change.org directly through our Help Center. The Change.org Team.
Cloudbleed – Behind the scenes
Cloudbleed is a bug which is alleged to have originated from the renowned company Cloudflare. As you may already know, Cloudflare offers internet security and infrastructure to some of the world’s biggest tech companies. These include Cisco, Zendesk, Nasdaq etc. As such, if you have used a website that uses CloudFlare’s services, chances are that your information may also have been leaked unceremoniously by this bug.
How does it work?
Cloudbleed may not be as dangerous as Heartbleed. However, it is being speculated that the damage caused by Cloudbleed is still not completely known. As such, the actual damage may be a lot more. Up till now, only 3400 websites are reported to have been affected by the bug. However, these websites were Cloudflare’s clients. There might be a number of other websites that might also have been affected.
Essentially, secured websites whose addresses have “https”, instead of just “HTTP”, in the beginning, prevent private information such as one’s address or passwords to be leaked and Cloudflare provides the necessary infrastructure for the secure movement of information between such websites. However, due to Cloudbleed, the information got saved and was also cached by search engines such as Google. Hence, the information could be easily retrieved by any hacker.
As of now, all that is known is that Change.org, Uber, OKCupid, and FitBit are among the websites that were affected. However, the good news is that Cloudflare has now fixed the bug and it is no longer on the loose.
How to defend oneself from the bug?
To date, there is no clear-cut answer to this. What has been leaked cannot be made secure again. Nevertheless, one should change one’s passwords immediately. Furthermore, websites that use Cloudflare are to be avoided. Cloudflare has a list of the clients that it serves on its website.
For Cloudflare’s clients, it might be a good idea to release a forced alert to your visitors instructing them to change their passwords.
If you have an account on Change.org it is advised to change your password. Also, Change.org lets users sign in with their Facebook account so if you have ever signed in using your Facebook account change your Facebook account password as well.
DDoS attacks are increasing, calculate the cost and probability of a DDoS attack on your business with this DDoS Downtime Cost Calculator.





