Cybersecurity firm KnowBe4 was tricked by a North Korean hacker posing as an IT worker whose next step was to load malware on a company-issued Macbook. Learn how the hacker bypassed security measures and what steps businesses can take to protect themselves from similar attacks.
Cybersecurity firm KnowBe4 revealed today that it was successfully targeted by a sophisticated phishing scheme orchestrated by a North Korean hacker posing as a legitimate IT worker. The attacker, who managed to pass KnowBe4’s rigorous hiring process, was ultimately identified and stopped before any data was compromised.
The incident began when KnowBe4 hired a remote software engineer who cleared multiple rounds of interviews and background checks. Upon receiving a company-issued Mac, the device immediately began loading malware, triggering KnowBe4’s onboard security software.
An investigation, conducted in collaboration with the FBI and cybersecurity firm Mandiant, uncovered the shocking truth: the hired engineer was a North Korean national using a stolen US identity. The attacker’s profile picture was a convincing AI-generated image, further masking their true identity.
“This was a real person using a valid but stolen US-based identity,” wrote KnowBe4’s Chief Executive Officer & President Stu Sjouwerman. “The picture was AI ‘enhanced’.”
The attacker’s tactics involved manipulating session history files, transferring potentially harmful files, and executing unauthorized software. They used a Raspberry Pi to download the malware and attempted to disguise their activity as routine troubleshooting.
KnowBe4’s security team quickly contained the threat, preventing any further damage. The incident highlights the growing sophistication of state-sponsored cyberattacks and the need for robust security measures.
Experts warn that North Korean operatives are increasingly targeting Western companies, exploiting remote work trends and using sophisticated methods to bypass traditional security protocols.
“This incident reveals how state-sponsored attackers are evolving to create convincing fake identities,” said Stephen Kowski, Field CTO at SlashNext Email Security+. “It’s clear we need to rethink our approach to security.”
Callie Guenther, Senior Manager, Cyber Threat Research at Critical Start, added, “Companies can identify potential threats by scrutinizing resumes, verifying identities, and monitoring for unusual behaviour.”
You’ve Been Warned!
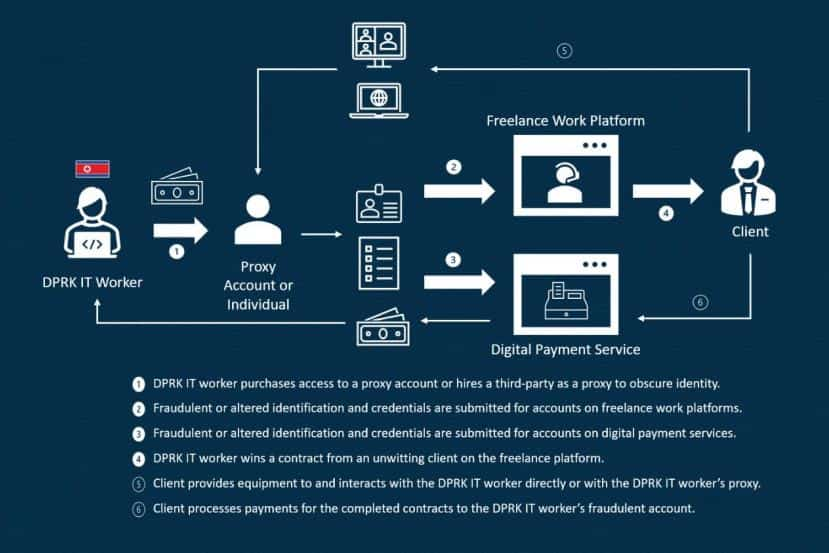
In May 2022, the US government warned organizations to beware of North Korean hackers in the guise of IT freelancers claiming to be non-DPRK (Democratic People’s Republic of Korea) nationals.
According to the advisory issued by the United States State and Treasury Departments and the Federal Bureau of Investigation (FBI), highly skilled mobile app and software developers from North Korea were trying to get employed by posing as IT freelancers. The advisory stated that the purpose behind this fraudulent activity was to pave the way for cyber intrusions from the North Korean government.
Protecting Your Organization: 10 Key Takeaways for HR Managers
Here are 10 points for HR managers to protect themselves from fake employee scenarios and what to do if they’ve been compromised:
Prevention:
- Rigorous Vetting: Implement multi-layered background checks that go beyond basic criminal records. Utilize third-party services specializing in identity verification and social media analysis.
- Video Interviews: Conduct video interviews for all candidates, especially remote positions. Pay close attention to inconsistencies between the candidate’s appearance and their online presence.
- Reference Checks: Verify references thoroughly, going beyond confirming employment dates. Speak to previous supervisors and colleagues to gain a deeper understanding of the candidate’s work ethic and character.
- Behavioural Assessments: Incorporate behavioural assessments into the hiring process to evaluate a candidate’s personality traits, work style, and potential for deception.
- Red Flag Awareness: Train hiring managers to recognize red flags such as inconsistencies in resumes, evasive answers during interviews, and overly eager or insistent candidates.
- Cybersecurity training: Make cybersecurity training a must in your organisation. Any employee with access to the company’s data or electronic device must be trained in identifying phishing scams, social engineering tactics and identifying fake profiles.
Response:
- Immediate Containment: If suspicious activity is detected, immediately isolate the affected user account and restrict access to sensitive systems.
- Forensic Investigation: Engage a cybersecurity firm to conduct a thorough forensic investigation to determine the extent of the breach and identify the attacker’s methods.
- Law Enforcement Notification: Report the incident to the FBI and other relevant law enforcement agencies.
- Data Breach Response Plan: Have a comprehensive data breach response plan in place to guide actions in the event of a security incident.
- Employee Communication: Communicate transparently with employees about the incident, outlining the steps taken to mitigate the risk and protect their data.
Remember, common sense and a multi-layered approach are vital for protecting your organization from such sophisticated cyberattacks.
RELATED TOPICS
- Feds Bust N. Korean Identity Theft Ring Targeting US Firms
- Hackers used fake job website to scam jobless US veterans
- Fake LinkedIn job offers scam spreading More_eggs backdoor
- Fake GitHub Repos Caught Dropping Malware as PoCs AGAIN!
- Employee Duped by AI-Generated CFO in $25.6M Deepfake Scam
- Fake PoC Script Tricked Researchers into Downloading VenomRAT