If you’ve updated your Windows today like me, this article may just end up scaring you a bit. In the latest, it has been discovered that a malicious campaign has been installing ransomware under the pretext of updating your operating system.
Named as Cyborg ransomware; the attackers try to lure users by sending emails prompting them to take immediate action with a two-line subject stating “Install Latest Microsoft Windows Update now! Critical Microsoft Windows Update!”
See: Ransomware attack cripples SmarterASP.NET hosting’s network
Moreover, the email in itself contains only one sentence (clearly someone mixed up the difference between the subject and message part). Here’s what the email looks like:

Although the file – 28KB in size – appears to be of the JPG format, it opens up as an executable file being a .NET downloader attracting suspicion. According to TrustWave’s blog post, this is partly attributed to the spoofing of file extensions being a very common practice used by hackers and hence also immediately alerting any anti-virus software that a user may have enabled – This also indicated the importance of using the best anti-virus software available out there.
If one continues with the execution stage, an executable file named bitcoingenerator.exe is secretly downloaded from a Github account called misterbtc2020. Though the account has been removed now, it does provide us considerable insight from the days that it was active in.

Then the ransomware will encrypt all the user’s files appending them with an extension of “.777”. Alongside, to achieve its ultimate monetary motive, a notice is left asking the victim to pay $500 via Bitcoin.
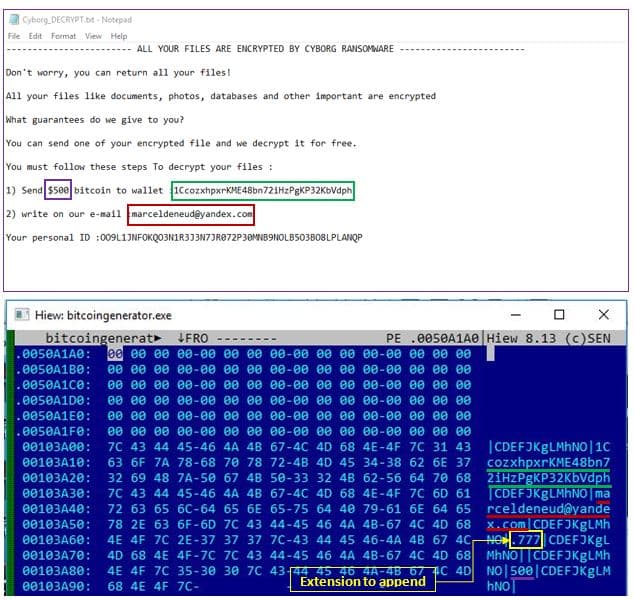
However, there’s one more interesting thing associated with this entire scheme. It turns out that anyone can generate a similar piece of ransomware using the “Cyborg Builder Ransomware” which is available on Github for anyone to make use of.

This was further proved by TrustWave who originally discovered the ransomware and shared details in the words of,
We compared the sample generated from the said builder (Ransom.exe) from what we have in this spam and they are similar! Only the overlay differs as it contains the data inputted by the builder’s user.
To conclude, there’s nothing that would qualify as rocket science or even advanced spoofing within this particular campaign. Hence, we can fairly say that if any user would make a small effort to find out the true origin of the information they’re receiving, such attacks could be easily averted.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.









