Aftermath of MOVEit vulnerability: Data vigilante ‘Nam3L3ss’ leaks nearly 8 million employee records from industry giants like Amazon, 3M, HP, and Delta, exposing cybersecurity flaws across major firms.
A “Data Vigilante” using the alias Nam3L3ss has leaked millions of employee records from global industry giants, in connection with the widespread MOVEit vulnerability. For your information, the MOVEit flaw is a security vulnerability in the MOVEit file transfer software, which many organizations use to share sensitive data.
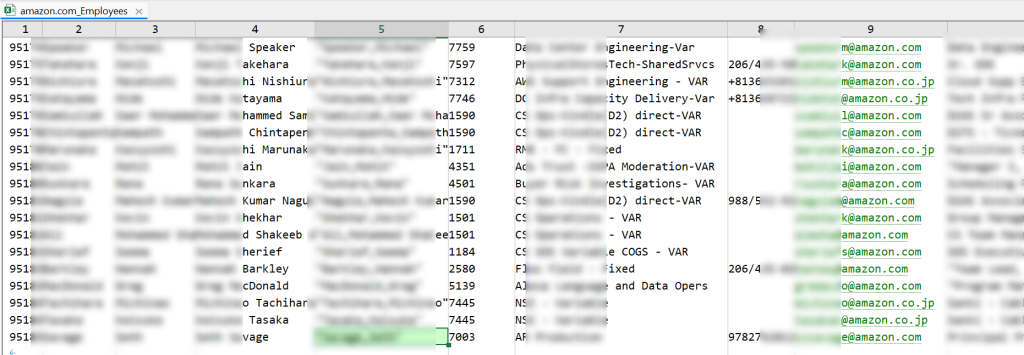
Nam3L3ss, who denies being a hacker, began leaking the data on Friday, November 8, 2024. So far, sensitive and non-sensitive records from 27 companies, totalling 7,952,414 employee records, have been exposed. This includes 2,861,111 records from Amazon employees, a breach acknowledged by the company.
“Amazon and AWS systems remain secure, and we have not experienced a security event. We were notified about a security event at one of our property management vendors that impacted several of its customers including Amazon,” Amazon spokesperson Adam Montgomery told Hackread.com. “The only Amazon information involved was employee work contact information, for example, work email addresses, desk phone numbers, and building locations.”
Data Analysis
The Hackread.com research team conducted an in-depth analysis of each file leaked by Nam3L3ss, revealing that the data includes full names, email addresses, phone numbers, office addresses, residential addresses, company names, location coordinates, and more.
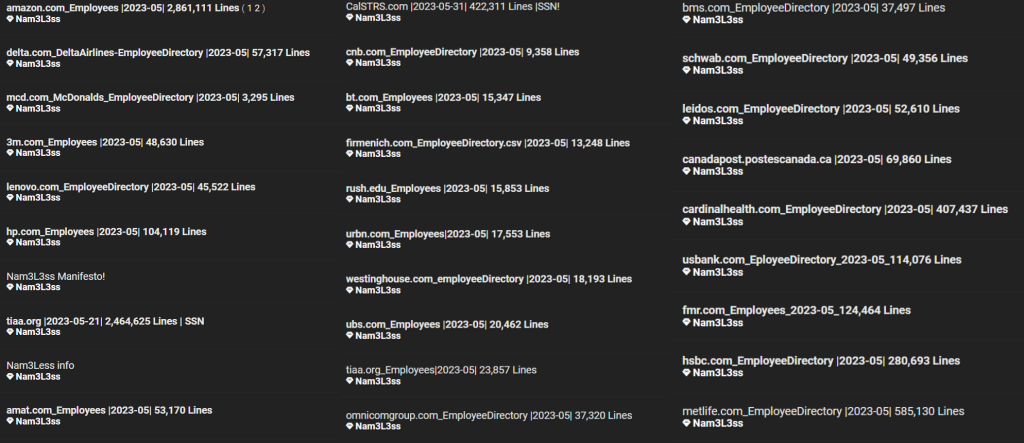
List of Affected Companies and Employee Counts
3M: 48,630 employees
HP: 104,119 employees
Delta: 57,317 employees
MetLife: 585,130 employees
Amazon: 2,861,111 employees
McDonald's: 3,295 employees
Lenovo: 45,522 employees
TIAA: 2,464,625 employees
CalSTRS: 422,311 employees
BT: 15,347 employees
URBN: 17,553 employees
Leidos: 52,610 employees
UBS: 20,462 employees
HSBC: 280,693 employees
Firmenich: 13,248 employees
U.S. Bank: 114,076 employees
Canada Post: 69,860 employees
Westinghouse: 18,193 employees
Rush University: 15,853 employees
Omnicom Group: 37,320 employees
Charles Schwab: 49,356 employees
City National Bank: 9,358 employees
Applied Materials: 53,170 employees
Cardinal Health: 407,437 employees
Bristol-Myers Squibb: 37,497 employees
TIAA (additional listing): 23,857 employees
Fidelity Investments: 124,464 employees
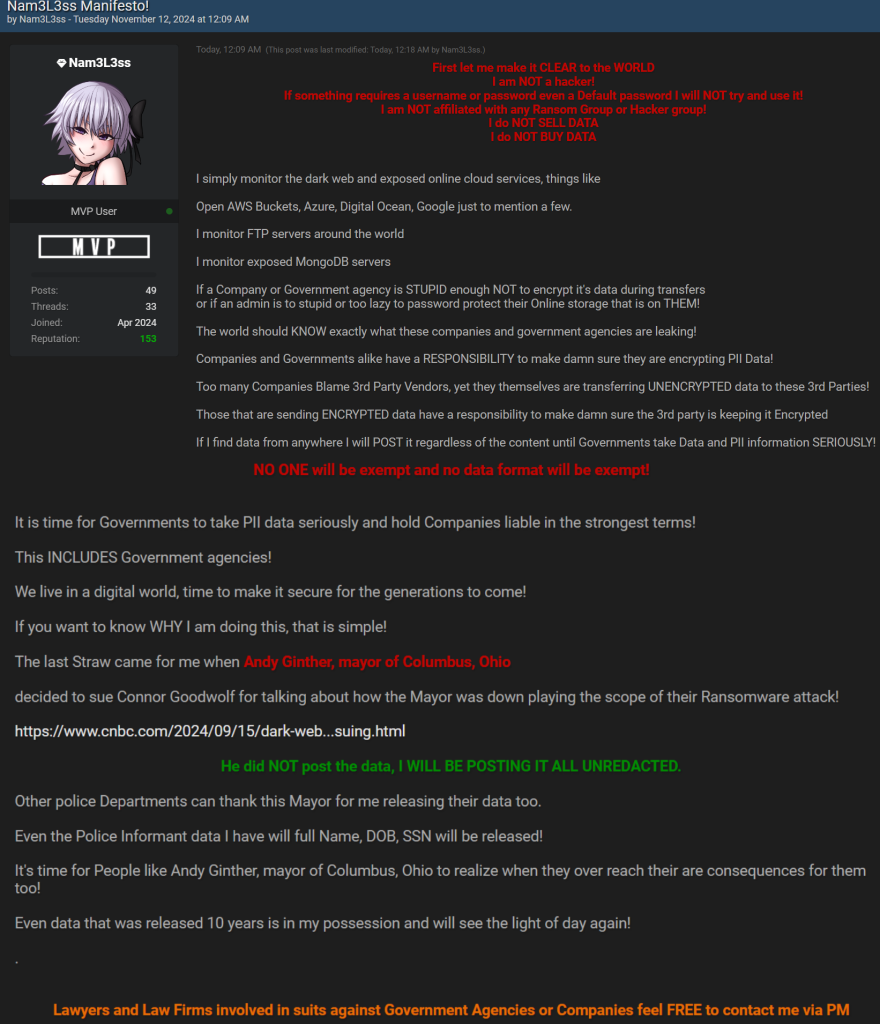
Nam3L3ss’s Manifesto: Motivation and Methodology
In a post on Breach Forums, Nam3L3ss outlined their “manifesto” to explain who they are and why they’re leaking data. According to the post, they monitor misconfigured and unsecured cloud databases across various services, including AWS Buckets, Azure, Digital Ocean, Google, and FTP and MongoDB servers, to extract and make this data public.
Nam3L3ss also claims to monitor ransomware groups, analyze stolen data, clean it by removing duplicates and irrelevant information, and then release it online. For example, the leaked MetLife employee directory originated from MetLife, a global financial services firm that suffered a ransomware attack in 2023.
The Cl0p ransomware gang exploited MOVEit extensively, targeting hundreds of organizations worldwide. They even created clear web websites to leak the stolen data in July 2024.
Ferhat Dikbiyik, chief research and intelligence officer at Black Kite, weighed in on the recent Amazon data breach, explaining, that Amazon’s recent data breach traced back to a third-party vendor’s use of the MOVEit tool, is another wake-up call for the supply chain’s hidden vulnerabilities.
“Amazon’s recent data breach traced back to a third-party vendor’s use of the MOVEit tool, is another wake-up call for the supply chain’s hidden vulnerabilities. The MOVEit flaw initially hit hundreds, but the shockwave extended across 2,700+ organizations as the ripple effects reached third and even fourth-party vendors,” Ferhat said.
“We’ve identified over 600 MOVEit servers that were likely caught in this “spray” attack—leaving a vast field of potential targets,” he explained. “CL0P ransomware, the group exploiting this flaw, named 270 victims within three months, and the count is still rising.”
“With 200 to 400 organizations speculated to have paid ransoms, the real impact stretches far beyond these numbers. This breach emphasizes that ransomware risk doesn’t stop at your company’s doorstep. In today’s ecosystem, exposure management must extend across the entire supply chain to truly defend against the next big attack.”
Data Vigilante?
Although the term Data Vigilante is debatable, Nam3L3ss expresses frustration with companies and government institutions for failing to secure their networks. By leaking this data, they aim to raise awareness about data security and encourage better cybersecurity practices.
Implications of the Data Leak and Advice to Employees
Although passwords and financial details weren’t included in the leaked files, the exposure poses significant risks to companies and employees. Threat actors, especially state-sponsored groups like North Korea’s Lazarus Group, are known to exploit such data to initiate phishing scams, steal cryptocurrency, and access financial information that could aid their country’s economy.
If you work for one of the affected companies, be on the lookout for phishing scams via email, SMS phishing (smishing), and voice phishing (vishing) attempts, as attackers may try to exploit this data for further scams.
RELATED TOPICS
- Hacker Leaks Thousands of Microsoft and Nokia Employee Details
- Hackers Calling Employees to Steal VPN Credentials from US Firms
- Hacker Leaks Data of 33K Accenture Employees in 3rd-Party Breach
- Shadow IT: Personal GitHub Repos Expose Employee Cloud Secrets
- Indian Ex-Employee Jailed for Wiping 180 Virtual Servers in Singapore