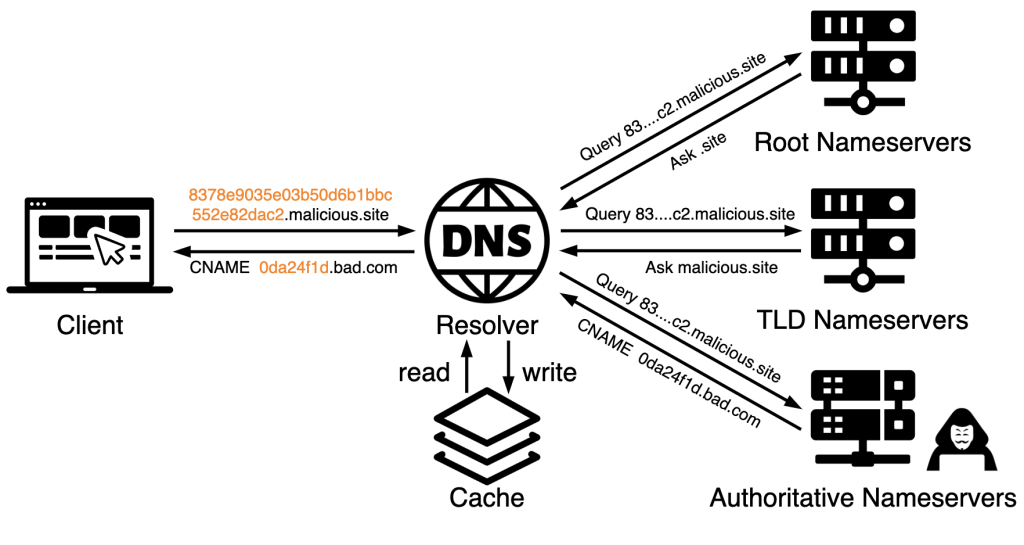
DNS tunneling is used to bypass security filters by hiding malicious traffic in DNS packets, allowing hackers to steal stolen data or hide inbound malware or command-and-control instructions.
However, Palo Alto Networks’ Unit 42 has discovered that threat actors are using DNS tunneling in innovative ways other than C2 and VPN, including scanning for network vulnerabilities and assessing the success of phishing campaigns.
DNS Tunneling for Tracking
Reportedly, attackers are abusing DNS tunneling to track victims’ activities related to spam, phishing, or advertisement contents, and delivering malicious domains with victims’ identity information encoded in subdomains.
For instance, in phishing attacks, DNS tunneling helps attackers embed tracking information within DNS requests, allowing them to monitor user interactions with content hosted on Content Delivery Networks (CDNs) and see if their emails are being delivered.
This was observed in the TrkCdn campaign, which targeted 731 potential victims using 75 IP addresses for nameservers, and in the SpamTracker campaign which targeted Japanese educational institutions using 44 tunneling domains with IP addresses 35.75.233210. Both campaigns used the same DGA naming and subdomain encoding method.
Attackers utilized DNS logs to track victims’ emails and monitor campaign performance. They registered new domains between October 2020 and January 2024, 2 to 12 weeks before distribution and monitored their behaviour for nine to 11 months and retired them after a year.
DNS Tunneling for Scanning
Adversaries can use DNS tunnelling to scan network infrastructure by encoding IP addresses and timestamps in tunneling payloads with spoofed source IP addresses, to discover open resolvers, exploit resolver vulnerabilities, and perform DNS attacks, potentially leading to malicious redirection or denial of service (DoS).
This method was observed in a campaign called “SecShow,” where attackers periodically scan a victim’s network infrastructure and perform reflection attacks.
“This campaign generally targets open resolvers. As a result, we find victims mainly come from education, high tech, and government fields, where open resolvers are commonly found,” Unit 42 researchers wrote.
Furthermore, attackers can use the same technique to track multiple victims and are exploiting DNS queries to detect network misconfigurations in targeted organizations, potentially exploiting them for DoS attacks, data theft, or malware installation.
To protect yourself, invest in security software that detects unusual DNS traffic patterns, and regularly update your operating system and applications to patch vulnerabilities. Always be wary of clicking on suspicious links in emails or messages.
RELATED TOPICS
- Dangers of DNS poisoning and how to prevent it
- DNSpionage group’s Karkoff malware selectively pick victims
- Roaming Mantis Malware Returns with DNS Changer Capability
- Check your VPN DNS test tool legitimacy: Is it “legit” or deceptive
- Cybersecurity Firm Hacks Itself, Finds DNS Flaw Leak AWS Credentials