KEY POINTS
- DroidBot Discovery: A new Android spyware, DroidBot, was identified in mid-2024, operating as Malware-as-a-Service (MaaS).
- Targets and Tactics: It targets financial institutions and users by disguising itself as security or banking apps and exploiting Android Accessibility Services.
- Capabilities: DroidBot can intercept messages, log keystrokes, capture screenshots, and remotely control devices.
- Affiliate Network: Used by 17 affiliate groups, it has attacked 77 targets across Europe, with expansion likely.
- Prevention Tips: Avoid unknown apps, update devices, and use reliable antivirus tools.
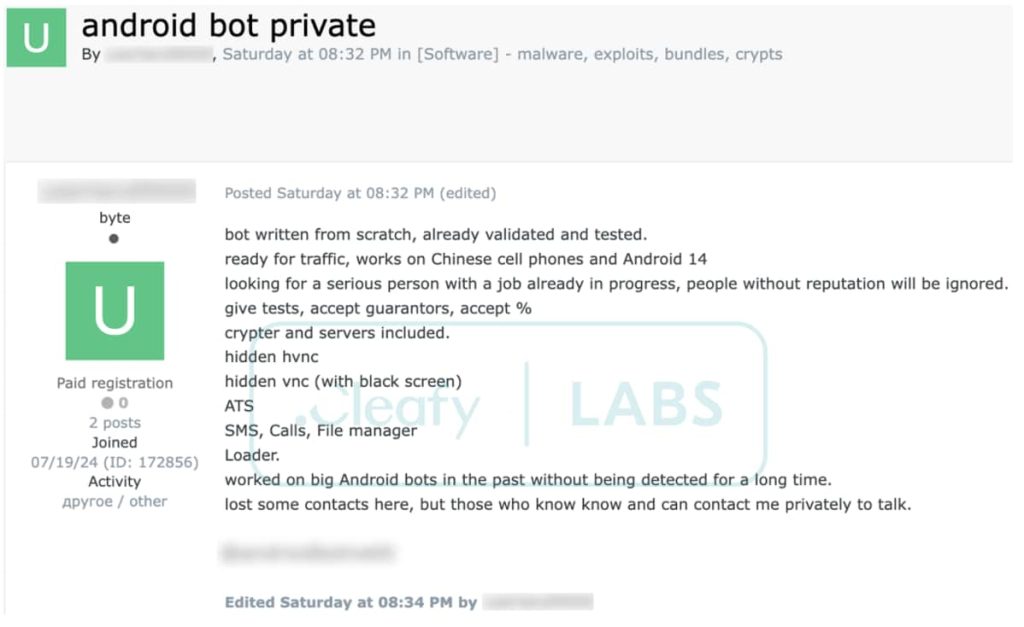
A recent discovery by Cleafy Labs has shed light on a new Android spyware threat dubbed DroidBot, identified in mid-2024 and operates on the MaaS (Malware-as-a-Service) operation model.
Similar to the legitimate Software-as-a-Service (SaaS) model, malware developers rent access to the malware in the MaaS model, making it easier for cybercriminals to launch attacks without requiring advanced technical expertise.
According to Cleafy Labs’ investigation, DroidBot is a sophisticated Android Remote Access Trojan (RAT) targeting financial institutions and individuals across Europe. This spyware is believed to have been developed by a Turkish-speaking group and leverages advanced techniques to steal sensitive information and control infected devices.
Research revealed that DroidBot is designed to target a wide range of victims, including banking customers, cryptocurrency exchange users, and government employees. It employs various tactics to compromise devices, such as disguising itself “as generic security applications, Google services, or popular banking apps,” and exploiting the Android Accessibility Services for its malicious activities.
After infecting your device, DroidBot can intercept SMS messages, log keystrokes, and capture screenshots of the device’s screen. It can also remotely control the device, allowing attackers to make calls, send messages, and access sensitive data.
This spyware offers a combination of hidden VNC and overlay capabilities with spyware-like features. It includes a keylogger and monitoring routines, enabling user interception, making it a potent tool for surveillance and credential theft.
Additionally, DroidBot’s dual-channel communication mechanism allows for outbound data transmission using the MQTT protocol, which was also used by Copybara and BRATA/AmexTroll banking trojans, and inbound commands over HTTPS, enhancing its operational flexibility and resilience.
The most concerning aspect of DroidBot is that it operates on the MaaS model with 17 distinct affiliate groups identified each using a unique identifier. This allows cybercriminals to rent access to the malware, making it easier for them to launch attacks without requiring advanced technical expertise.
“At the time of analysis, 77 distinct targets have been identified, including banking institutions, cryptocurrency exchanges, and national organisations, underscoring its potential for widespread impact,” researchers noted in the blog post.
DroidBot is currently in active development, with some functions like root checks being placeholders and features varying between samples. Despite these inconsistencies, the malware has demonstrated potential, targeting users in the UK, Italy, France, Spain, Turkey, and Portugal, and a probable expansion into Latin American regions.
“Within the code, we can see that this information is customised for 4 main languages: English, Italian, Spanish, and Turkish,” Cleafy Labs revealed.
To protect yourself from DroidBot and similar threats, be cautious when downloading apps from unknown sources, keep your devices updated with the latest security patches and use reliable antivirus software.
RELATED TOPICS
- First Mobile Crypto Drainer on Google Play Steals $70K
- Spyware Found in Google Play Store Apps, 2m Downloads
- Google Removes Swing VPN App Exposed as DDoS Botnet
- Malware infected Minecraft modpacks hit Google Play Store
- These 8 Apps on Play Store Contain Android/FakeApp Trojan
- 35 malicious apps found on Google Play, installed by 2m users