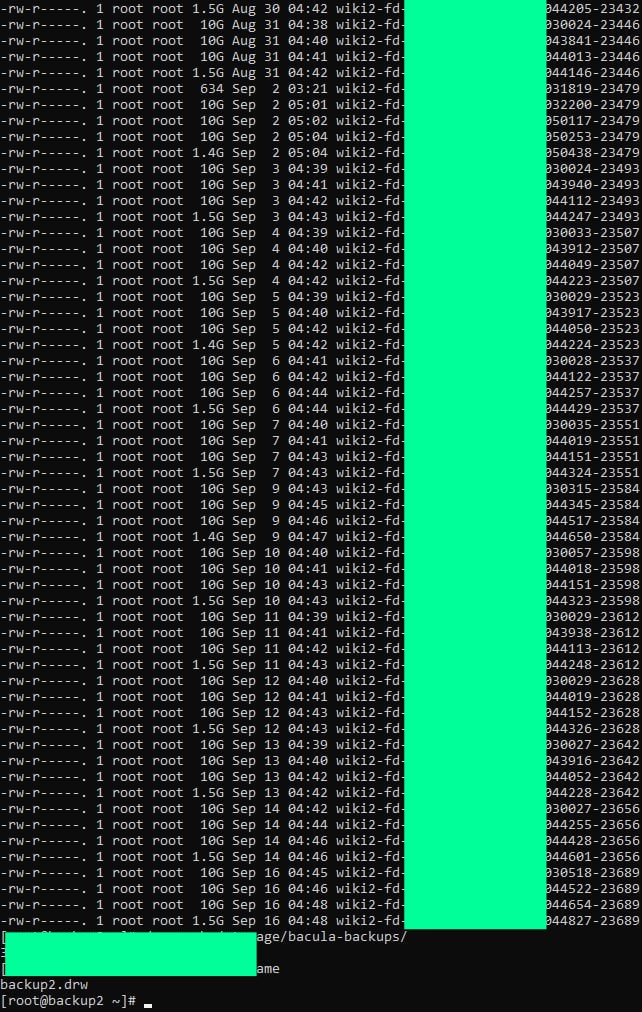
Pro-Ukrainian hacktivists from DumpForums claim to have breached Russian cybersecurity giant Dr.Web, stealing over 10 TB of sensitive data, including internal projects, client databases, and critical infrastructure access.
DumpForums, a pro-Ukrainian hacktivist forum, claims to have breached Dr.Web, a Russian cybersecurity company and antivirus solutions provider. As a result, hackers have announced stealing over 10 TB of internal, customer/client data, Hackread.com can exclusively confirm.
The attack dates back to Saturday, September 14th, when Dr.Web (also known as Doctor Web, Doctor Web Ltd., and Company Doctor Web) identified that it had suffered a cyberattack. After investigating, the Russian cybersecurity giant published a brief blog post on September 17, 2024, revealing that the company was targeted in a cyberattack aimed at its “resources.” At that time, Doctor Web claimed that it had “prevented the attack in a timely manner” and that no user data was accessed or stolen.
However, as Hackread.com’s research team discovered, on the morning of October 8th, 2024, DumpForums hacktivists used their Telegram account to announce and claim responsibility for the September attack. The hacktivists’ Telegram post contradicted what Doctor Web had stated about the hack in September.
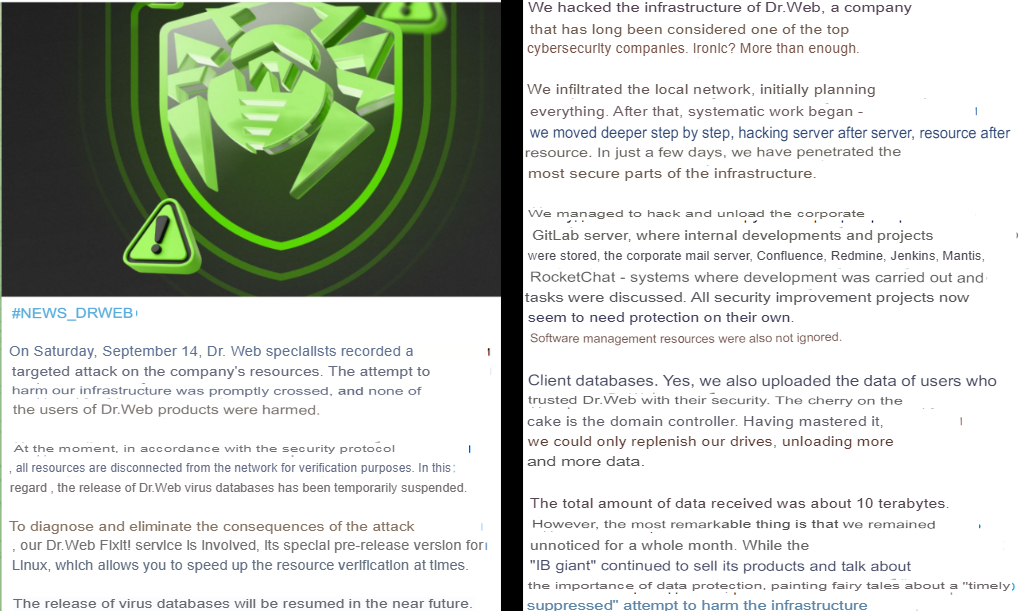
DumpForums Hacktivists Claim Dr.Web’s Infrastructure Hack
According to the post, the hacktivists stated they had hacked the infrastructure of Dr.Web, adding that they infiltrated the company’s local network after planning everything in advance. After that, they systematically hacked more servers and resources “within just a few days.”
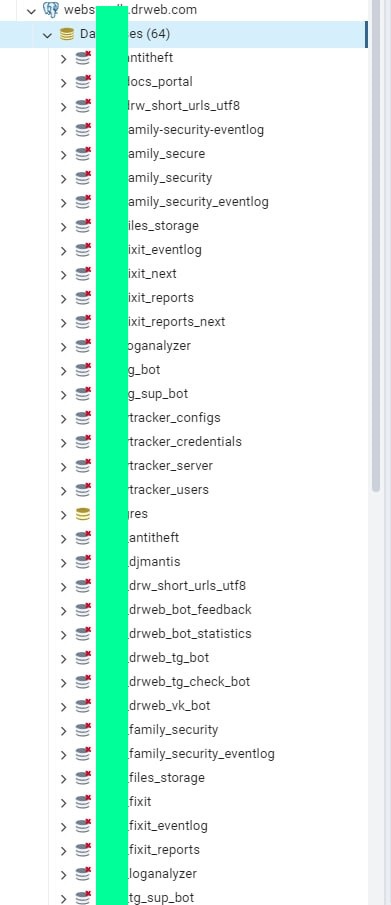
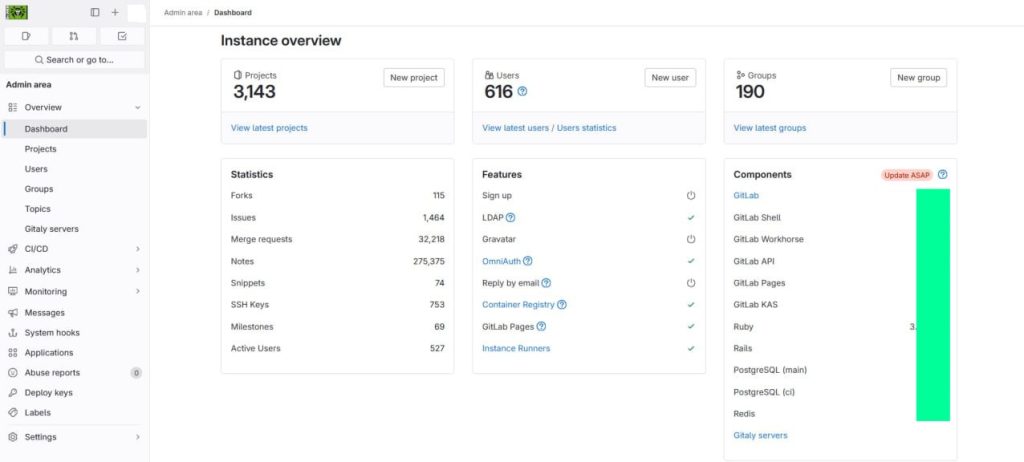
Additionally, the hackers claimed to have hacked and extracted data from Dr.Web’s corporate GitLab server, where internal developments and projects were stored, including the corporate email server, Confluence, Redmine, Jenkins, Mantis, and RocketChat.
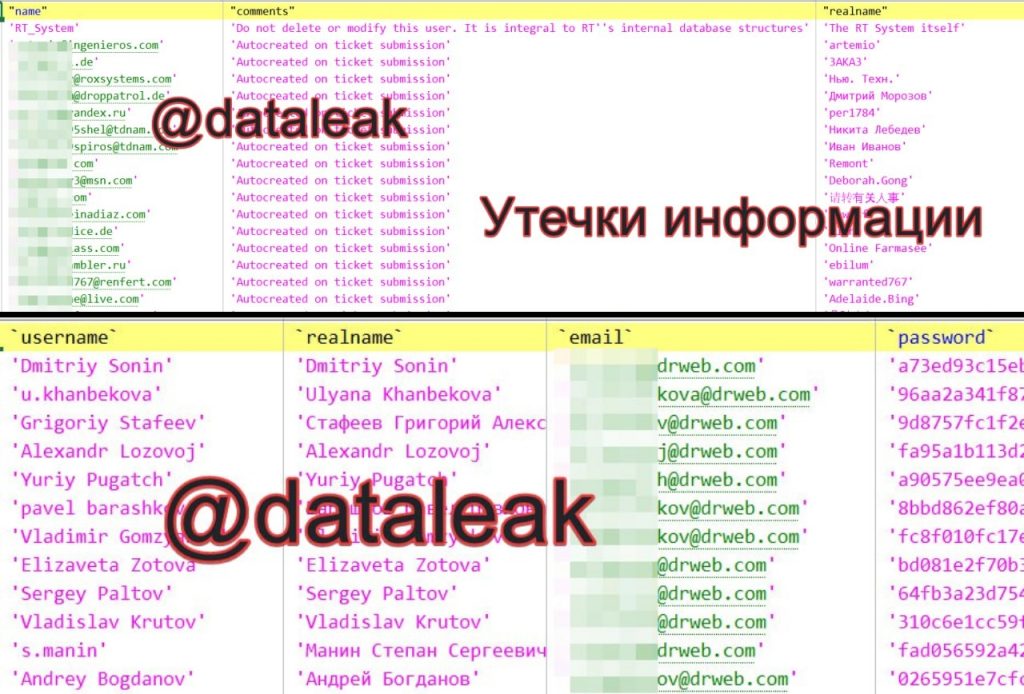
The hackers also claimed to have accessed and downloaded the entire client/user database, which they had already leaked on their official forum.
To further authenticate their claims, the hackers provided several dumps of databases from internal resources such as ldap.dev.drweb.com, vxcube.drweb.com, bugs.drweb.com, antitheft.drweb.com, and rt.drweb.com, among others.
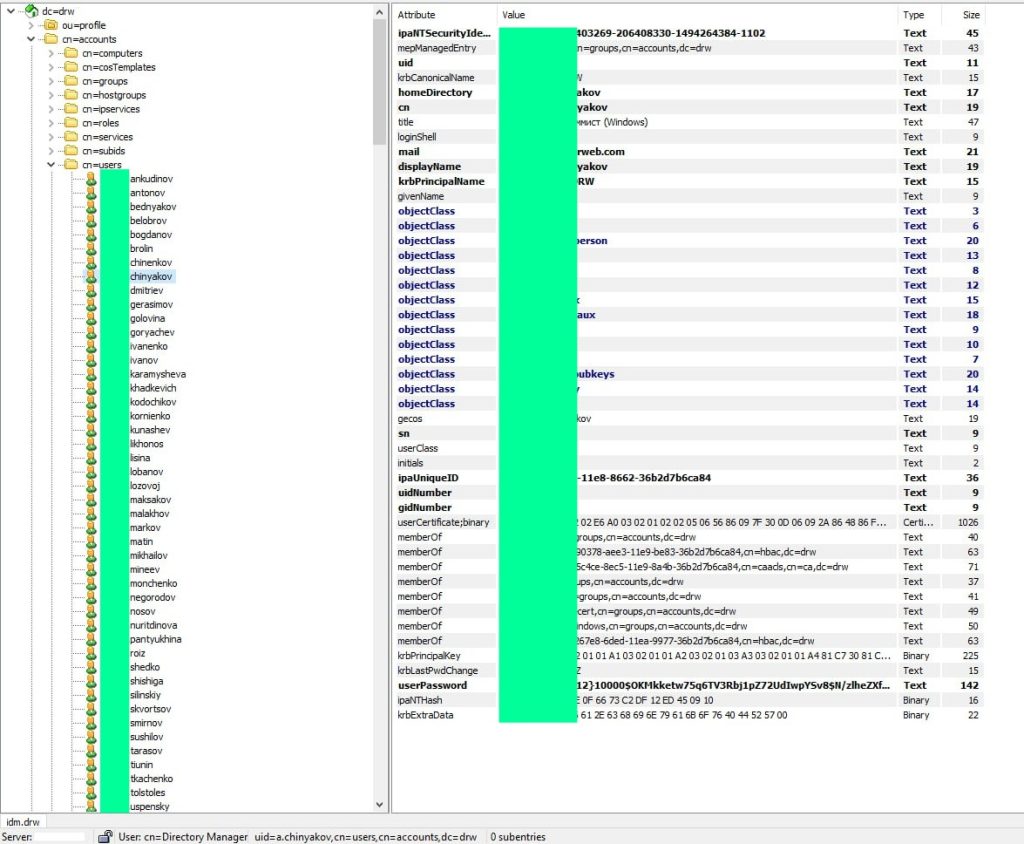
Accessing Dr.Web’s domain controller?
What’s even more concerning are the claims from the hacktivists that they gained control of Dr.Web’s domain controller, a critical part of the company’s infrastructure. The domain controller manages authentication and access to all systems within a network. By compromising it, the attackers would have had unlimited access to the entire network, allowing them to continuously extract massive amounts of sensitive data.
This level of control reportedly enabled them to remain undetected for a month while siphoning off around 10 terabytes of data. The group also pointed out Dr.Web’s alleged poor security, stating that they spent an “entire month” in the system while the company continued selling products to secure others.
It is important to note that Hackread.com has reached out to Dr.Web regarding the claims made by DumpForums hacktivists, and this article will be updated accordingly.
John Bambenek, President at Bambenek Consulting weighed in on the situation, highlighting the broader implications of the claims from DumpForums. “In times of geopolitical conflict, it’s not uncommon for organizations that appear to have ties to the adversary to be targeted,“ John explained.
“A security company should be experts at preventing attacks, however, when they are victims, it begs the question of whether the victim really knows what they are doing. 10 TB is a great deal of data. It should have been noticed as it was leaving the corporate perimeter,“ he argued.
Ukraine and Russia Cyberwarfare
It is also worth noting that DumpForums is known for attacking critical Russian infrastructure. In June 2022, the same group was behind the hack and defacement of the Russian Ministry of Construction, Housing, and Utilities. The hackers also stole the ministry’s entire database and demanded 0.5 BTC as ransom to prevent the data from being leaked online.
Nevertheless, the cyber warfare between Russia and Ukraine is gaining new momentum. Hackers from both countries have been targeting each other’s critical infrastructure since the conflict began on February 24, 2022.
According to Ukraine’s State Service of Special Communications and Information Protection (SSSCIP), there has been a significant shift in Russian cyber operations against Ukraine in the first half of 2024. The new strategy marks a departure from previous broad-spectrum attacks to a more targeted approach focusing on Ukraine’s military and defence sectors.
On the other hand, Ukrainian hackers have been quite active over the past few months. Some of their claimed cyberattacks include targeting banks and shutting down ATMs in Russia, targeting the government sector and damaging petabytes of data, crippling the country’s tax system, and other actions.
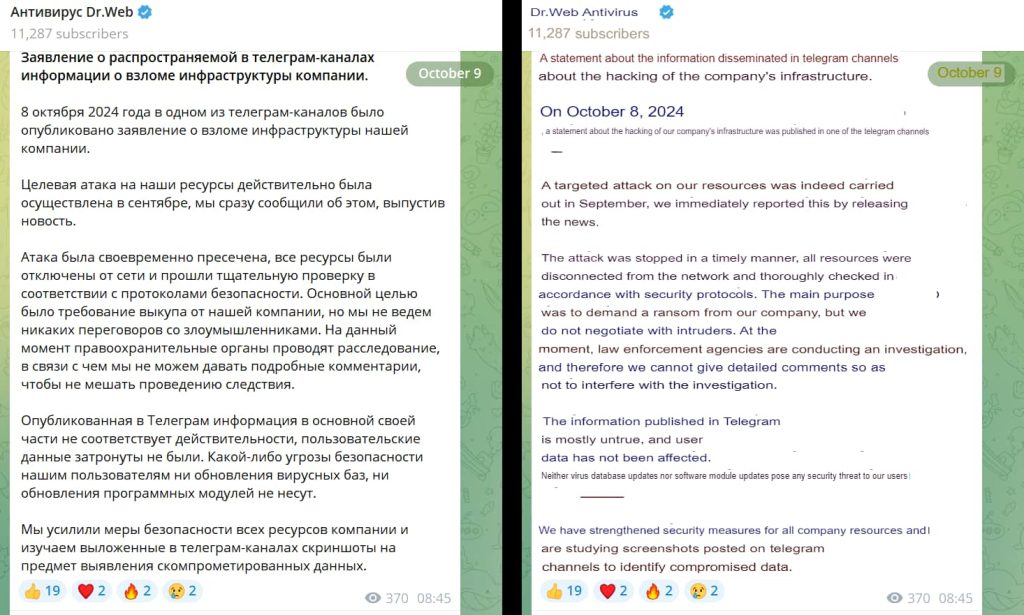
UPDATE (08:06 Wednesday, 9 Oct 2024 (GMT)
Dr.Web has yet to respond to Hackread.com’s inquiry. However, on its official Telegram channel, the company acknowledged experiencing a cyberattack but denied DumpForums’ claims of extracting 10 TB of data. Meanwhile, DumpForums continues to assert its claims and has vowed to leak the data.
Here’s what the cybersecurity firm said in its latest announcement:
RELATED TOPICS
- Ukrainian Hacktivists Trick Russian Military Wives for Personal Info
- Protestware Uses npm Packages to Call for Peace in Gaza, Ukraine
- Ukraine Hacks Russia’s Aviation Agency, Claims “Aviation Cannibalism”
- 57,000 Kaspersky Fan Club Forum User Data Leaked in Hosting Breach
- Ukrainian Hackers Breach Email of APT28 Leader, Who’s Wanted by FBI