So far, Facebook Messenger users in 80 countries have been targeted by this phishing scam, reports Group-IB.
The Singapore-based cybersecurity firm Group-IB has released a new report providing details of a new phishing campaign affecting users in over 80 countries.
The ‘global threat hunting and adversary-centric cyber intelligence agency’ revealed in its report that threat actors are targeting Facebook users in Europe, Asia, North and South America, and the Middle East with fake ads promoting a Facebook Messenger update.
Campaign Aimed at Stealing User Credentials
Group-IB’s Digital Risk Protection (DRP) analysts revealed that attackers deliver fake Facebook ads to promote an updated version of Facebook Messenger to steal users’ login credentials. The agency has discovered around 1,000 fake Facebook profiles that are being used to post the ads.
SEE: Facebook ads dropped malware posing as Clubhouse app for PC
According to researchers, the majority of users in countries such as Italy, Canada, Germany, France, South Africa, Singapore, Malaysia, and the USA have fallen victim to this scam and got their accounts hijacked.
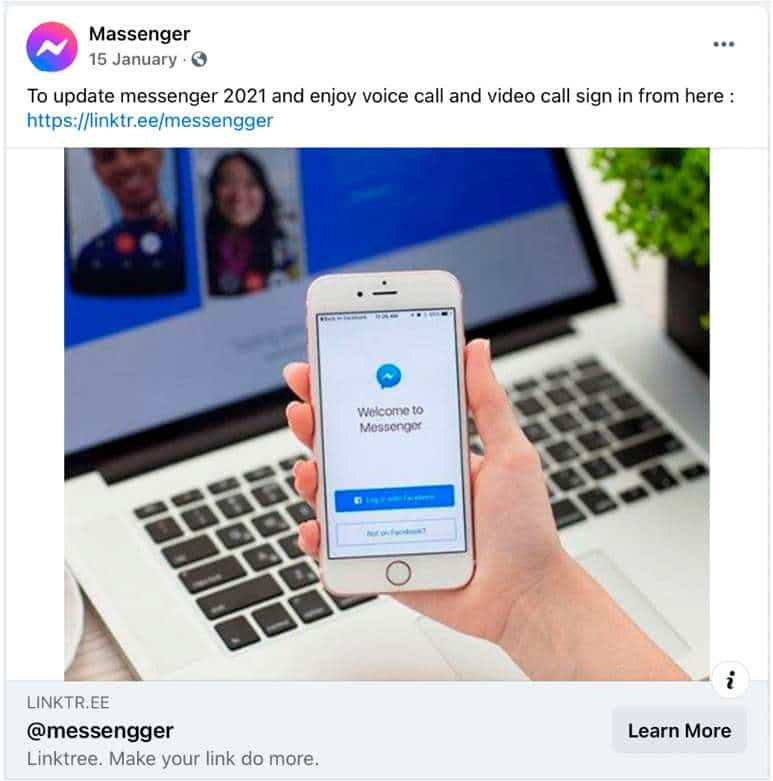
Phishing Scam Active since Last Summer
DRP analysts claim that they discovered this campaign back in summer 2020 after detecting its traces in Asia and Europe, and in April, the number of FB posts inviting users to install the new update had reached 5,700.
Dmitriy Tiunkin, the head of Group-IB Europe’s DRP department, stated in a press release that users are highly likely to fall prey to such scams because the internet has made them “abandon critical thinking.”
“Living in the era of instant-everything, clicking on an attractive ad, proposal, headline became a natural human reflex. This didn’t come unnoticed by fraudsters who have been relentlessly feeding on users’ carelessness,” Tiunkin said in a blog post.
How does it work?
Scammers use platforms like blogspot.com, sites.google.com, github.io, and godaddysites.com to register fake Facebook Messenger login pages.
Fraudsters register accounts with names mimicking the original app, such as Messanger, Masssengar, or Meseenger, etc. They also insert Facebook Messenger’s official logo in their profile picture.
To facilitate FB’s moderation process and bypass its scam filters, fraudsters use shortened links created using services like bit.ly, rb.gy, cutt.ly, and linktr.ee.
Moreover, to lure unsuspecting users, they offer users some non-existent features like finding out who visited one’s profile or viewing deleted messages, or even shift to Gold Messenger.
SEE: Ragnar Locker ransomware gang using Facebook ads to extort victims
In some cases, the campaigners threatened users that their accounts would be banned if they do not sign up on the fake page. When users click on the malicious link, a fake Facebook Messenger webpage appears containing a login form. Users are asked to enter their credentials, and that’s how the fraudsters steal login information.

Group-IB has informed Facebook about this campaign. Until it is shut down, Facebook users must remain cautious and avoid clicking on shortened URLs. Look out for misspellings in the names of brands and their web addresses to timely detect online scam campaigns.
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.