Cybercriminals are using GitHub to distribute malware through fake accounts. Learn how the “Stargazers Ghost” network operates and how to protect yourself from falling victim to this malicious scheme. Discover tips to identify suspicious repositories and stay safe online.
Researchers at Check Point Research (CPR) have uncovered a network of malicious actors exploiting GitHub, the world’s largest source code host, to distribute malware. This network, dubbed “Stargazers Ghost,” leverages a network of seemingly legitimate accounts to spread malware.
These “Ghost” accounts trap unsuspecting users by mimicking legitimate users by creating repositories and performing activities like Forking, Starring, and Subscribing to lend fake legitimacy to their actions and lure victims into downloading “advertised” content.
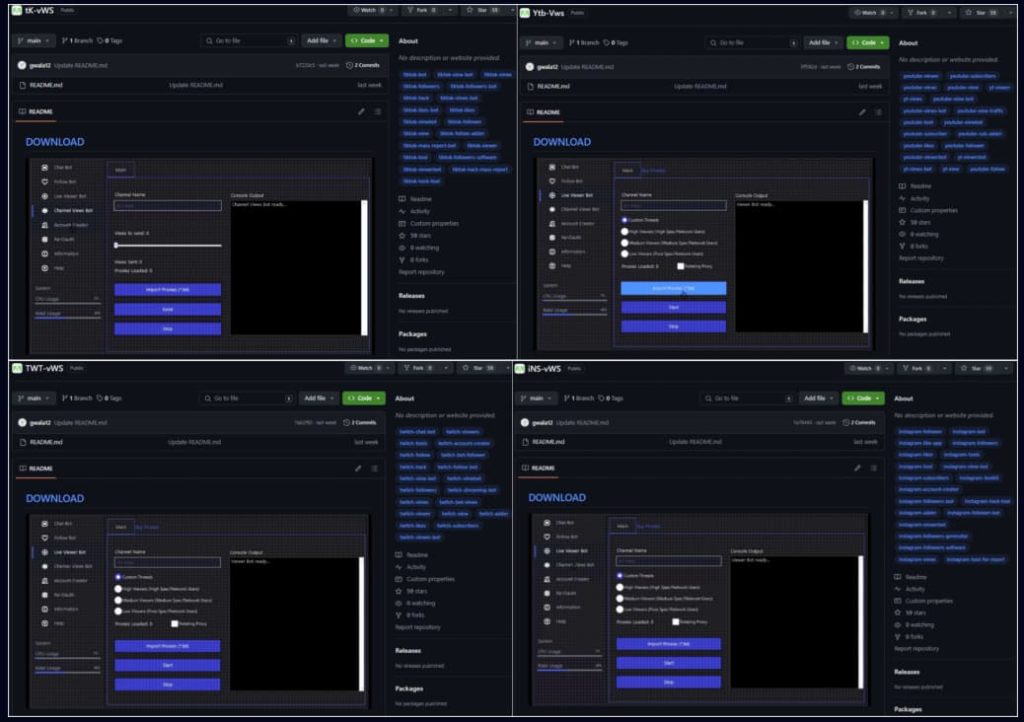
The malware is typically distributed through malicious links embedded within these repositories. Unsuspecting users clicking on these links unknowingly download and install the malware on their devices.
The number of accounts is unclear due to network evolution. Recent calculations suggest over 3,000 Ghost accounts, possibly even more because a campaign of 30 repositories uses around 380 Ghost accounts
According to CPR’s report, Stargazers Ghost uses identical tags and images but switches the target audience from one social media application or cracked software to another, using the same template, suggesting that it automates activities to ensure efficiency and scalability.
Additionally, the campaign uses three GitHub Ghost accounts with different responsibilities: serving the phishing repository template, providing the image, and serving malware as a password-protected archive.
The network challenges the traditional approach of malware attacks by providing a malicious repository where links are Starred and verified by multiple GitHub accounts, ensuring their legitimacy.
CPR found over 2,200 malicious repositories involved in “Ghost” activities during a campaign in January 2024, in which the Atlantida stealer, a new malware family that steals user credentials and cryptocurrency wallets, was distributed. Within four days, over 1,300 victims were infected. Other preferred malware includes Rhadamanthys, RisePro, Lumma Stealer, and RedLine.
Researchers believe that the malicious links to GitHub repositories were possibly distributed via Discord channels, targeting YouTube, TikTok, Twitch, and Instagram followers and containing phishing templates for cracked software and crypto-related activities.
This network “acts as a Distribution as a Service (DaaS)” allowing “threat actors to share malicious links or malware for distribution through highly victim-oriented phishing repositories,” CPR’s report read.
Social media, gaming, and cryptocurrency users are the network’s key targets for ransomware infections, credentials stealing, and compromised wallets. Currently targeting Windows users, similar methods could affect Linux or Android users.
This scheme has generated over $100,000 through over 3,000 ghost accounts on GitHub since its alleged inception in August 2022 and around $8,000 from mid-May to mid-June 2024.
Stargazer Goblin, the network’s operator, gained prominence a year ago when CPR discovered an advertisement in dark web forums offering a pricelist of actions to be taken.
“It’s concerning to see a large platform like GitHub being exploited for malware distribution by a sophisticated operation like Stargazers Ghost Network,” said Alexander Chailytko, Cyber Security, Research & Innovation Manager, Check Point Research.
“This precise targeting could impact a substantial number of victims worldwide, leading to severe consequences. The fact that we’ve also identified a similar campaign on YouTube suggests a shift in malware Distribution as a Service (DaaS) approach, where attackers leverage popular platforms to spread infections covertly,” he added.
To stay safe, be cautious of unfamiliar repositories and links within repositories. Research the developer and project before downloading anything and avoid clicking on links unless absolutely confident.