Beware “crowdstrike-hotfix.zip”! This fake file spreads Remcos malware, targeting LatAm CrowdStrike users. Don’t download it! Learn how to stay safe from phishing scams.
On July 19, 2024, a botched CrowdStrike Falcon® sensor update for Windows operating systems resulted in the biggest IT outage worldwide in recent history. Despite being the result of a technical issue, this incident has opened the door for real threat actors to exploit the situation, leading to a wave of malicious activities, particularly targeting CrowdStrike’s Latin American (LATAM) customers.
CrowdStrike Intelligence has reported the distribution of a deceptive ZIP archive, named crowdstrike-hotfix.zip, containing a HijackLoader payload designed to deploy the RemCos RAT (remote access tool).
The ZIP file, with Spanish filenames and instructions, suggests a targeted attack on LATAM users. The file was first uploaded by a Mexico-based submitter who uploaded it to an online malware-scanning service.
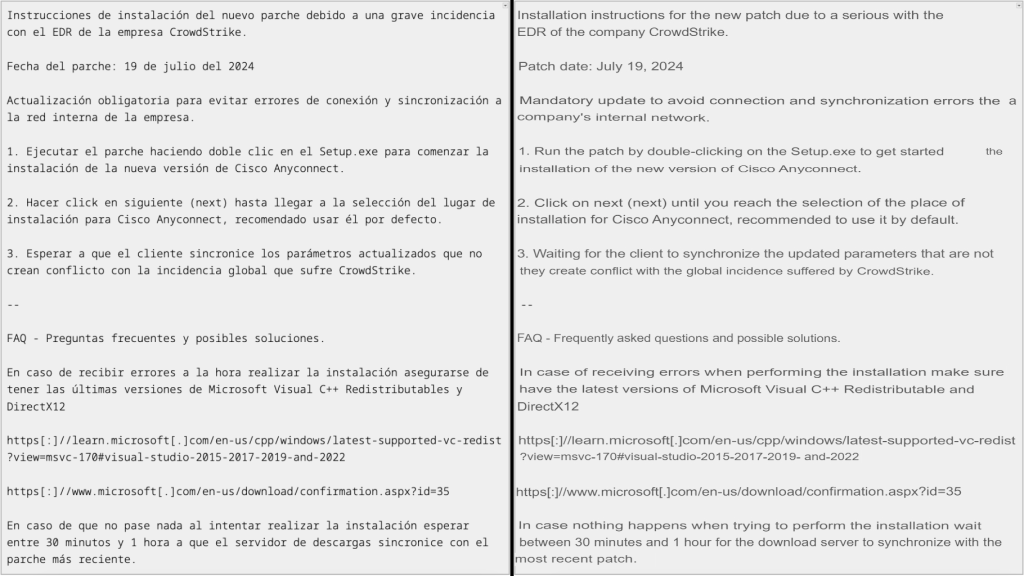
The attack sequence begins with the execution of Setup.exe, which uses DLL search-order hijacking to load HijackLoader. Advertised as a private crypting service known as ASMCrypt, HijackLoader is adept at evading detection. It executes the final RemCos payload, which connects to a command-and-control server at 213.5.130.58:433, allowing the attacker to gain control over the infected systems.
The U.S. Cyber Defense Agency, the U.K.’s National Cyber Security Centre, and Australia’s National Anti-Scam Centre have all issued warnings to be cautious of scams. Both advisories are available here and here.
These scams often involve phishing emails, fake support calls, and fraudulent offers of remediation services. The best practice is to contact businesses directly through their official channels rather than responding to unsolicited communications.
CrowdStrike has established a “Remediation and Guidance Hub” to assist those affected, while Microsoft has provided updated support guides. Both organizations stress the importance of verifying communications and not rushing into actions prompted by unsolicited messages.
To combat these threats, it is crucial to follow a few key practices: remain alert to potential phishing attempts, verify the authenticity of communications, avoid downloading files from untrusted sources, and report any suspected scams to the appropriate authorities.